This series of walkthroughs aims to help out complete beginners with finishing the Web Fundamentals path on the TryHackMe (thm)1 website.
It is based on the learning content provided in the Walking An Application room.
Task 1 - Walking An Application
Read the intro and the short breakdown about the room. Make sure to start the machine.
Question 1: I confirm that I have deployed the virtual machine and opened the website.
No answer needed
Task 2 - Exploring The Website
Check out the website, and it’s various directories. To get a better picture, run gobuster to find the most common ones.
gobuster dir -u https://10-10-205-27.p.thmlabs.com/ -w /usr/share/dirb/wordlists/common.txt
| command name | description |
|---|---|
| gobuster | Gobuster is a tool used to brute-force URIs including directories and files as well as DNS subdomains. |
| options | description |
|---|---|
| dir : <command> | Uses directory/file enumeration mode |
| -u / –url string | The target URL |
| -w / –wordlist string | Path to the wordlist |
Here is the complete terminal interaction in kali:
──(bluewalle@kali)-[~]
└─$ gobuster dir -u https://10-10-205-27.p.thmlabs.com/ -w /usr/share/dirb/wordlists/common.txt
===============================================================
Gobuster v3.2.0-dev
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: https://10-10-205-27.p.thmlabs.com/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirb/wordlists/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.2.0-dev
[+] Timeout: 10s
===============================================================
2022/10/17 21:43:32 Starting gobuster in directory enumeration mode
===============================================================
/assets (Status: 301) [Size: 178] [--> http://10-10-205-27.p.thmlabs.com/assets/]
/contact (Status: 200) [Size: 3108]
/customers (Status: 302) [Size: 0] [--> /customers/login]
/development.log (Status: 200) [Size: 27]
/monthly (Status: 200) [Size: 28]
/news (Status: 200) [Size: 2538]
/private (Status: 301) [Size: 178] [--> http://10-10-205-27.p.thmlabs.com/private/]
/robots.txt (Status: 200) [Size: 46]
/sitemap.xml (Status: 200) [Size: 1495]
Progress: 4607 / 4615 (99.83%)===============================================================
2022/10/17 21:44:03 Finished
===============================================================
┌──(bluewalle@kali)-[~]
└─$
Notice, that just by running a simple directory enumeration, we already found three other folders that were not listed in the task.
- /assets
- /monthly
- /private
Besides the directories, some interesting file paths were also discovered:
- /development.log
- /sitemap.xml
- /robots.txt
In a pentest scenario, these files could potentially hold important information, but as that is not the aim for this room, we will skip them.
But first, check out the main page in the browser.
Question 1: Read the above.
No answer needed
Task 3 - Viewing The Page Source
Check out the page source, and follow the instructions in the task to get the flags.
Question 1: What is the flag from the HTML comment?
flag
To get the first flag, check out the webpage that is hidden in the developers comment. On firefox, press CTRL+U to view the page source.
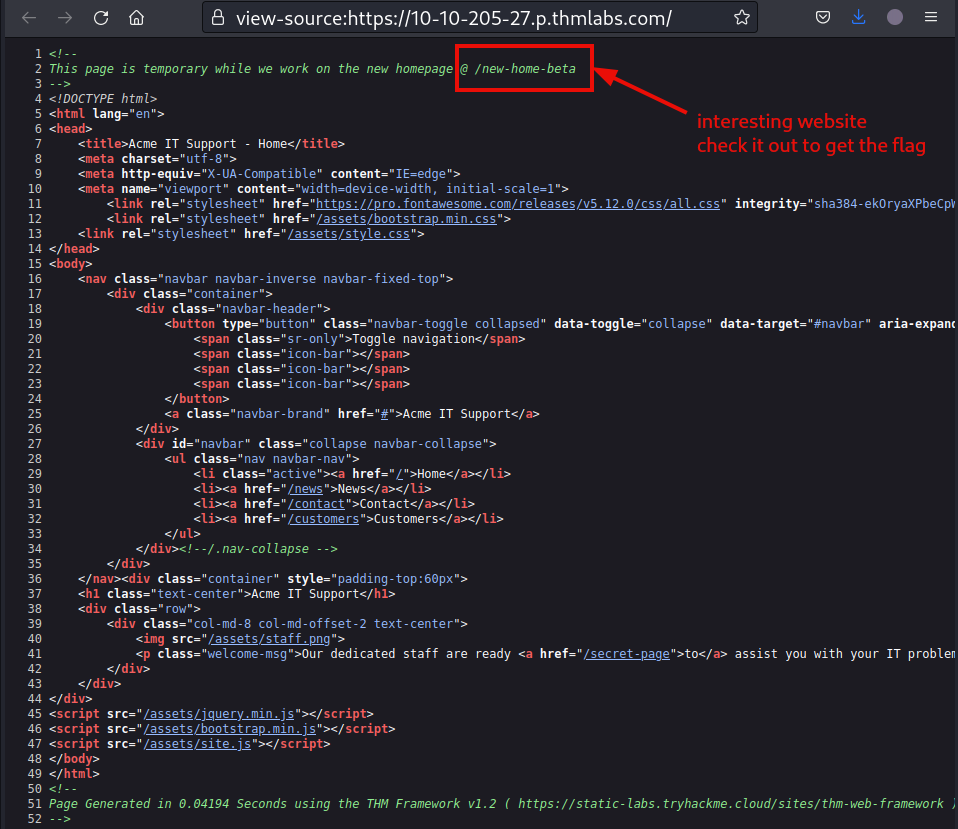
Head over to the hidden website mentioned by the developer, and grab the flag
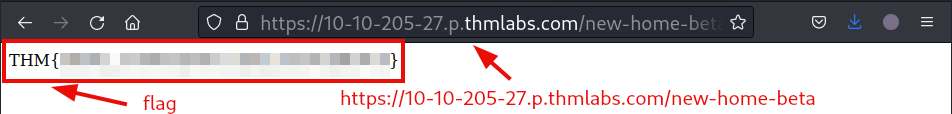
Question 2: What is the flag from the secret link?
flag
There is an other hidden page mentioned in the page source further down.
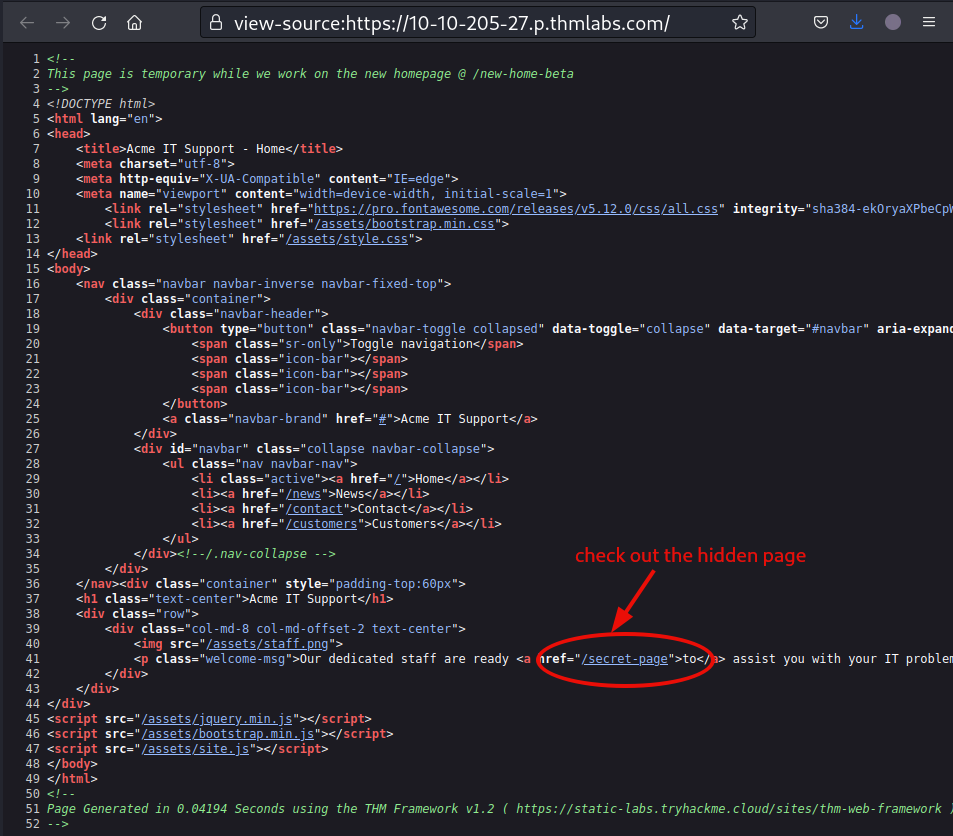
The same as before, follow the page to get the flag.
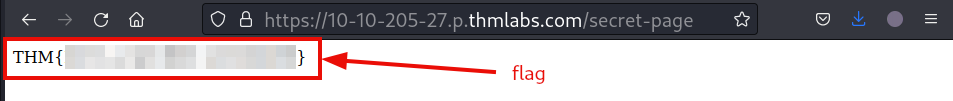
Question 3: What is the directory listing flag?
flag
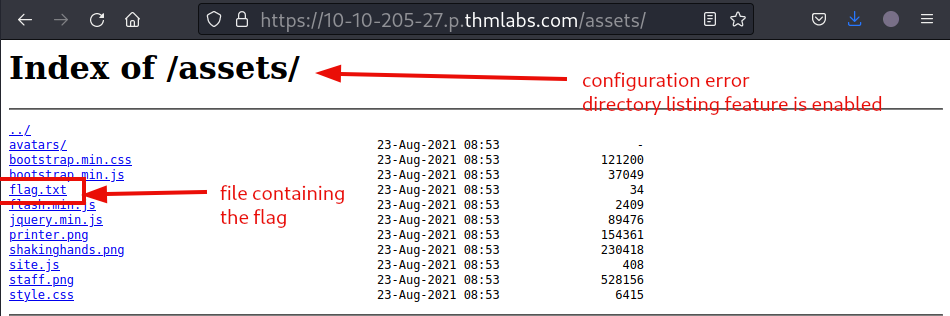
As mentioned, there is a configuration error (directory listing feature remains enabled) in the web application. That is why, we can simply traverse the /assets directory and get the flag that is stored in the flag.txt file.
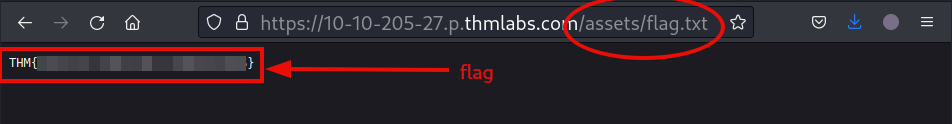
Question 4: What is the framework flag?
flag
For the last flag in this task, follow the link to the framework’s website. It is listed at the bottom of the page source.
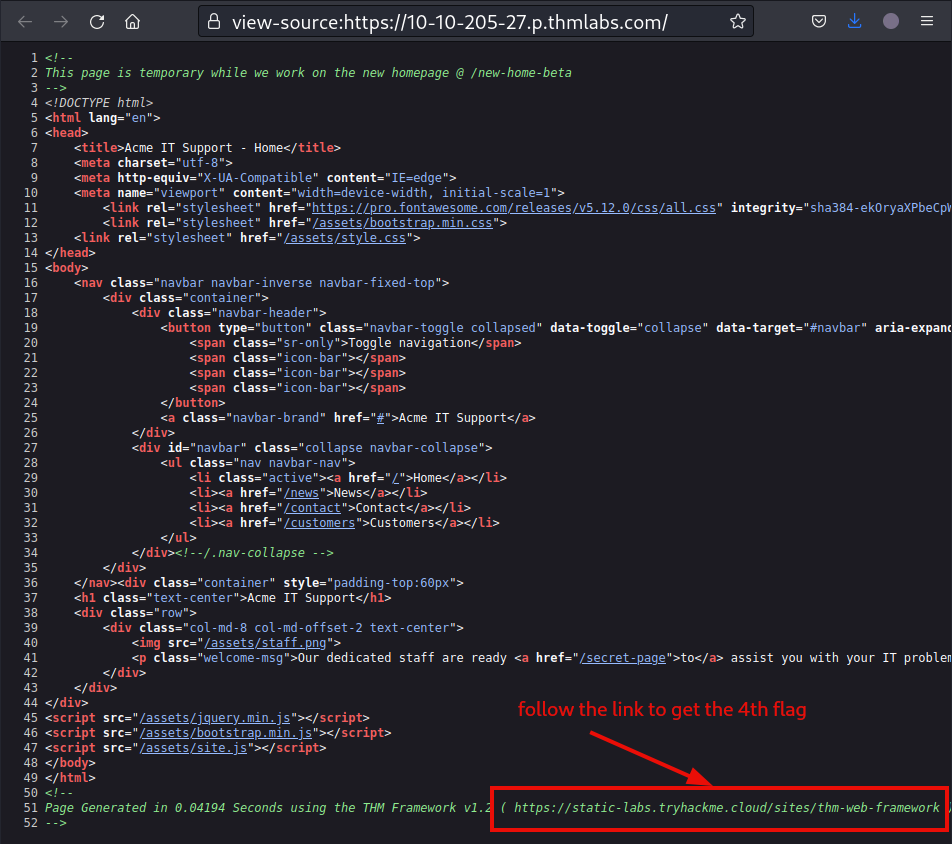
We will notice, that our version is one patch behind.
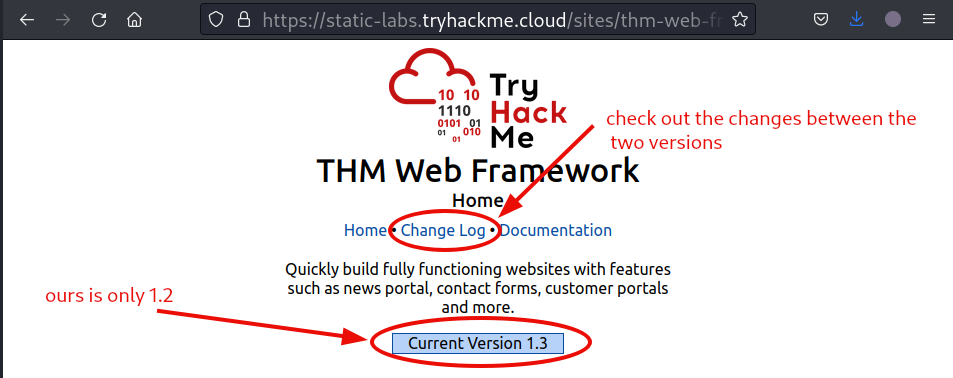
Let’s check out the changes since the last version. The change log mentions a file by the name of /tmp.zip. Check it out.
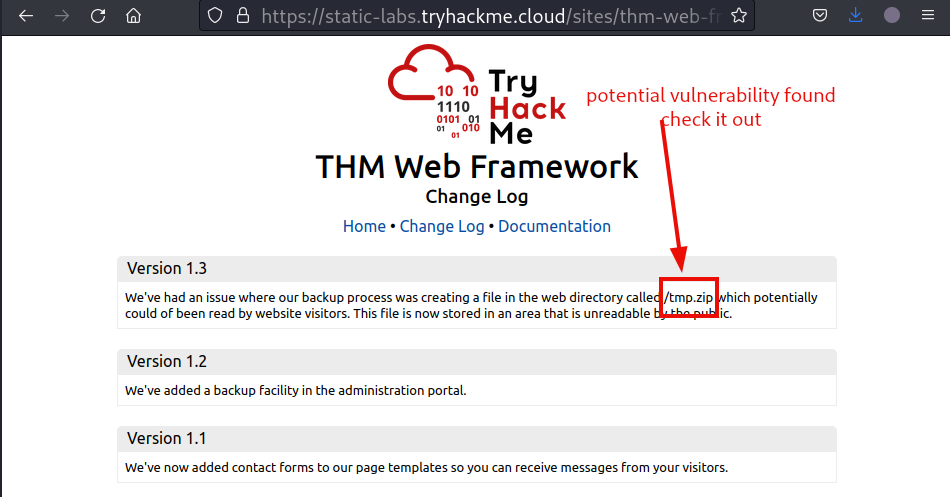
By entering the file path, our browser will automatically try and download it. Let’s allow it.
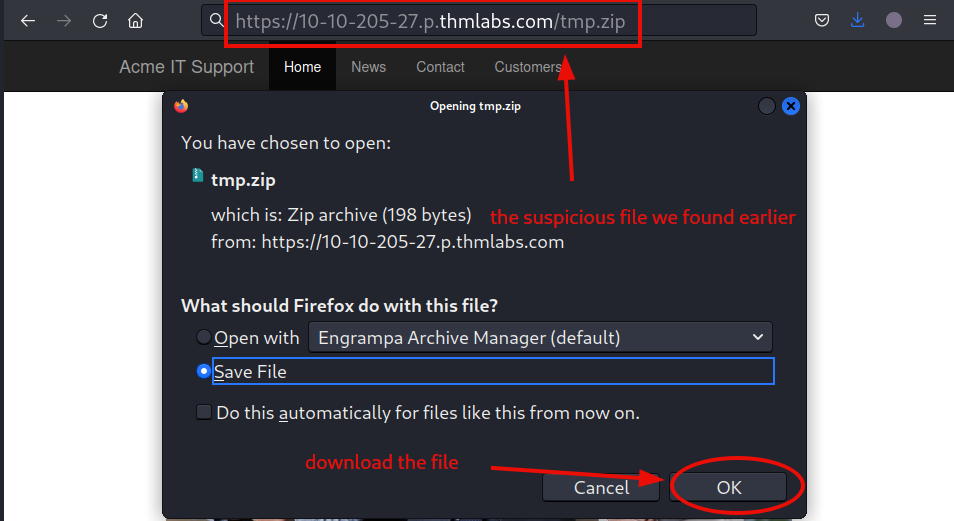
On our system, go to the directory where the file was saved and check it’s contents.
cd Downloads/ ; ls -hlag
Unzip the compressed file, and get the flag.
unzip tmp.zip
cat flag.txt
Do not forget to clean up after yourself.
rm tmp.zip flag.txt
The commands used above are listed here. For more information about them, check out their man pages.
| command name | description |
|---|---|
| cd | change directory |
| ls | list directory contents |
| unzip | list, test and extract compressed files in a ZIP archive |
| cat | concatenate files and print on the standard output |
| rm | remove files or directories |
Here is the complete terminal interaction on kali:
┌──(bluewalle@kali)-[~]
└─$ cd Downloads/ ; ls -hlag
total 12K
drwxr-xr-x 2 bluewalle 4.0K Oct 17 22:49 .
drwxr-xr-x 32 bluewalle 4.0K Oct 17 21:52 ..
-rw-r--r-- 1 bluewalle 198 Oct 17 22:47 tmp.zip
┌──(bluewalle@kali)-[~/Downloads]
└─$ unzip tmp.zip
Archive: tmp.zip
extracting: flag.txt
┌──(bluewalle@kali)-[~/Downloads]
└─$ cat flag.txt
THM{*flag*}
┌──(bluewalle@kali)-[~/Downloads]
└─$ rm tmp.zip flag.txt
Task 4 - Developer Tools - Inspector
Read about the development tools and head over to the news directory to follow along.
Question 1: What is the flag behind the paywall?
flag
Open up the 3rd article, and inspect the blocked out part as described. As an alternative, you can open up the inspector from developer tools in firefox by pressing [CTRL+SHIFT+I].

Click on the premium-customer-blocker class in the inspector module, and change the style from display: block to display: none. This will then remove the blocker displayed on the article.

Do not forget to grab the flag while you are at it.

Task 5 - Developer Tools - Debugger
Question 1: What is the flag in the red box?
flag
For the next flag, move to the /contract directory and open up the debugger module in developer tools. Then check out the flash.min.js javascript file that is stored in the /assets directory. Beautify it with the built-in “Pretty Print” function to get a better readability.

Set the breakpoint as instructed and refresh tha page.

Get the flag.

Task 6 - Developer Tools - Network
Question 1: What is the flag shown on the contact-msg network request?
flag
For the last flag; first, open up the network module in developer tools. Then, fill out the contact form with dummy data. Finally, send the request.

We are notified by a pop-up window that our request was successfully sent and received. Check out the our request for more detail.

You will find the last flag under our response headers, with a header named X-FLAG. As an alternative, we could simply head over to /contact-msg to grab the same flag.

Make sure to terminate the machine that was started before moving on to the next room.
thm - shorthand for TryHackMe from now on ↩︎