This series of walkthroughs aims to help out complete beginners with finishing the Pre Security Path on the TryHackMe (thm)1 website.
It is based on the learning content provided in the Packets & Frames room.
Task 1 - What are Packets and Frames?
Learn how to differentiate between packets and frames and when they are used. (That poor dog again…)
Question 1: What is the name for a piece of data when it does have IP addressing information?
Packet
Question 2: What is the name for a piece of data when it does not have IP addressing information?
Frame
Task 2 - TCP/IP (The Three-Way Handshake)
Discover the TCP/IP model, which is very similar to the OSI model discussed before, and check out how the Three-way handshake works.
Question 1: What is the header in a TCP packet that ensures the integrity of data?
Checksum
Question 2: Provide the order of a normal Three-way handshake (with each step separated by a comma)
SYN,SYN/ACK,ACK
Task 3 - Practical - Handshake
Use the static lab that is provided in the task to reassemble a communication between Alice and Bob following the order set by the TCP handshake. Get the flag at the end.
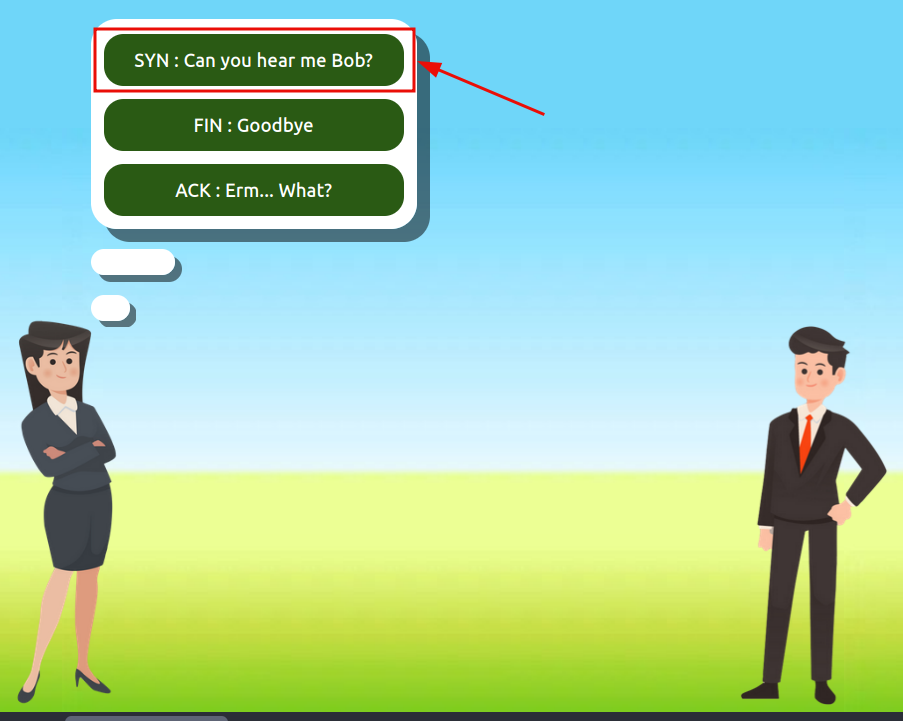
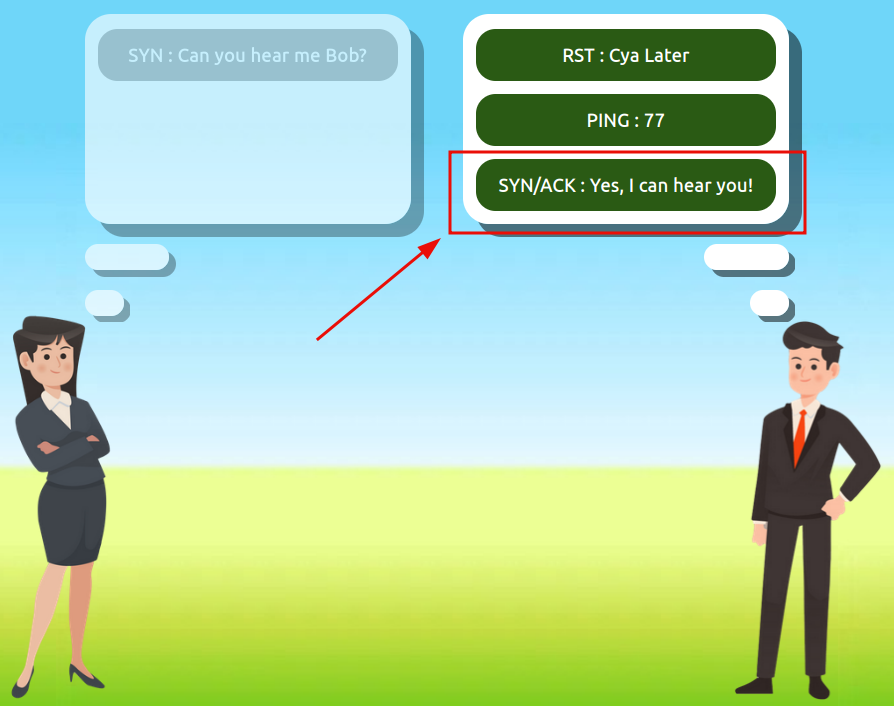
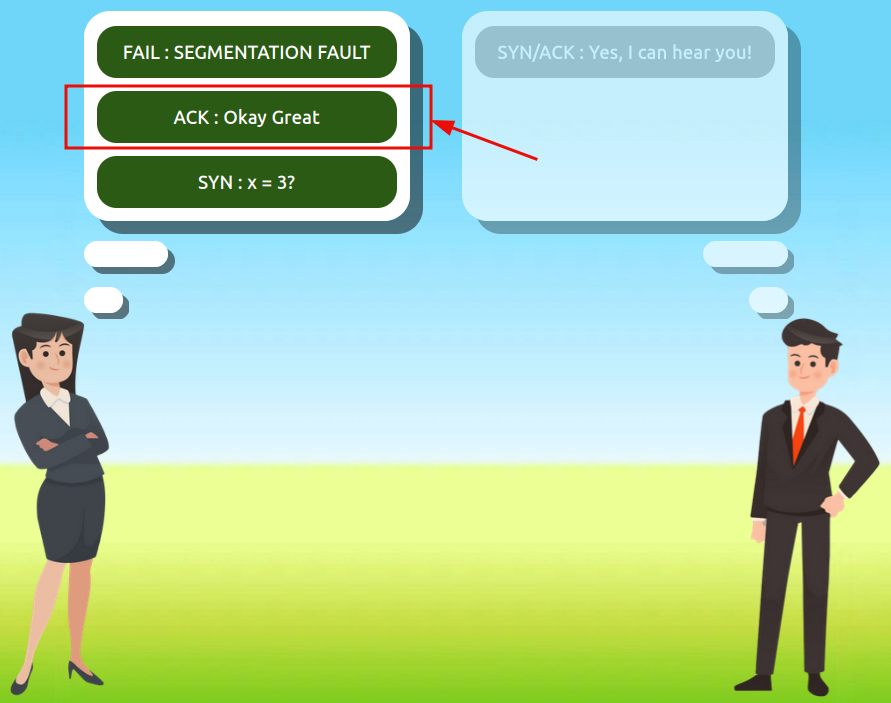
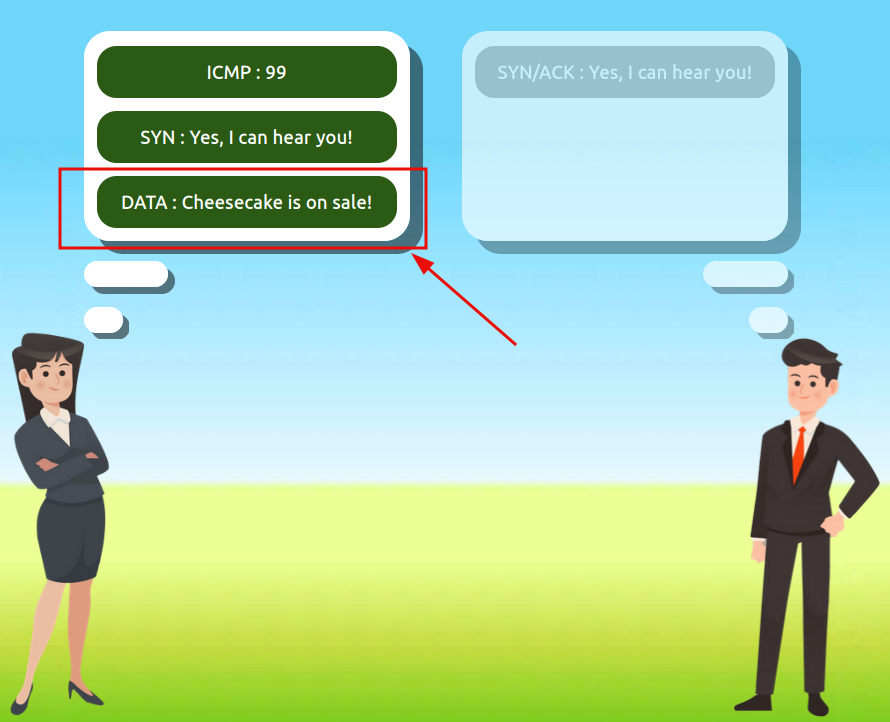
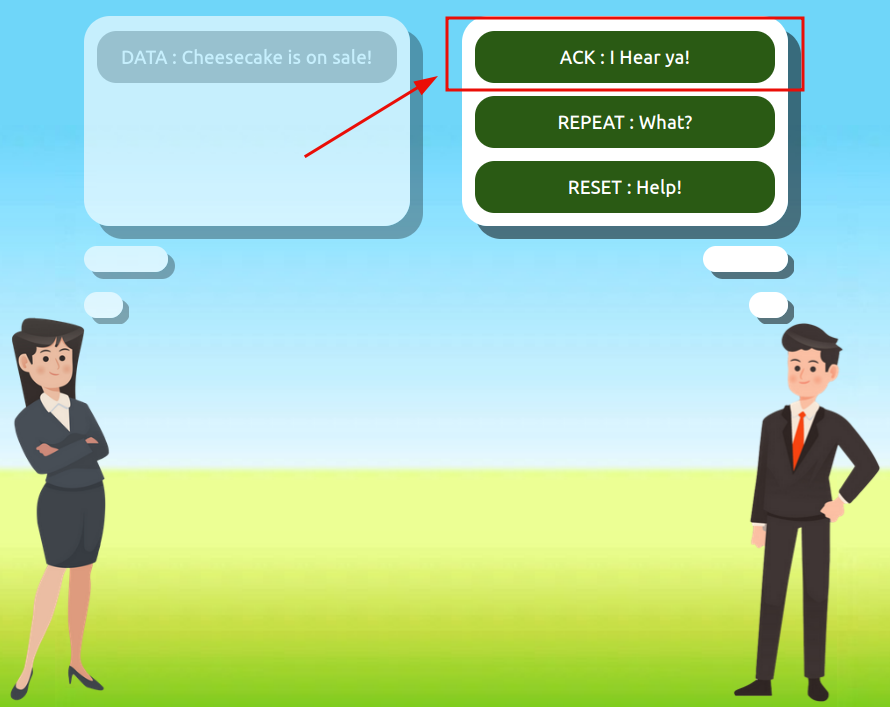
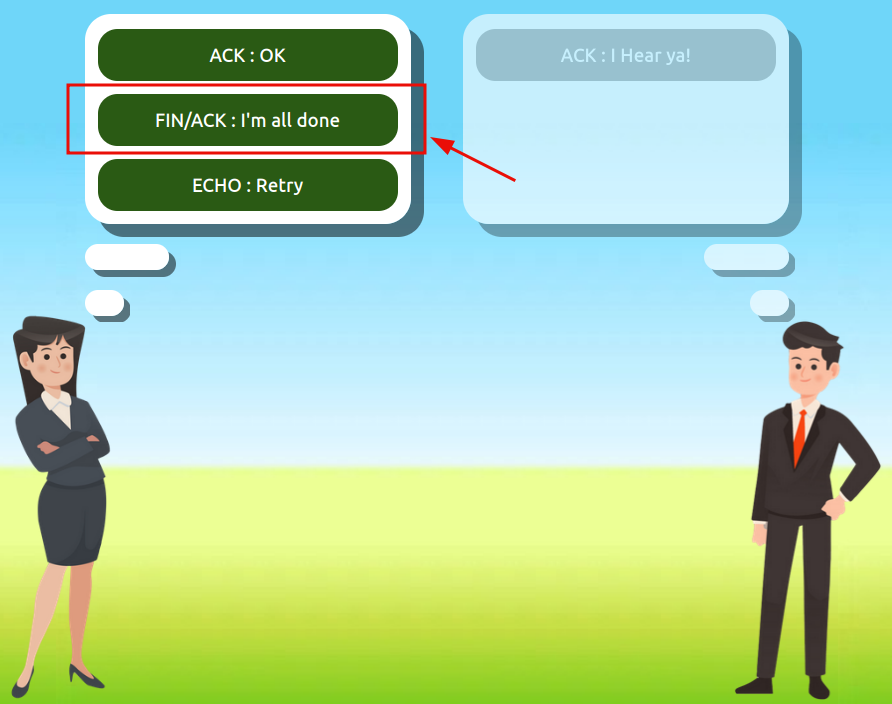
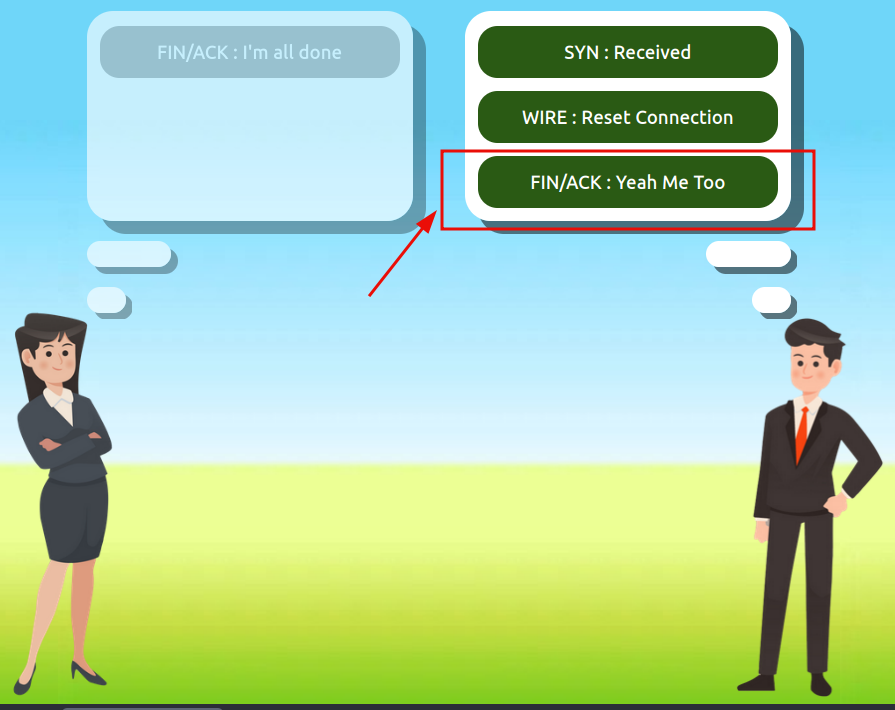
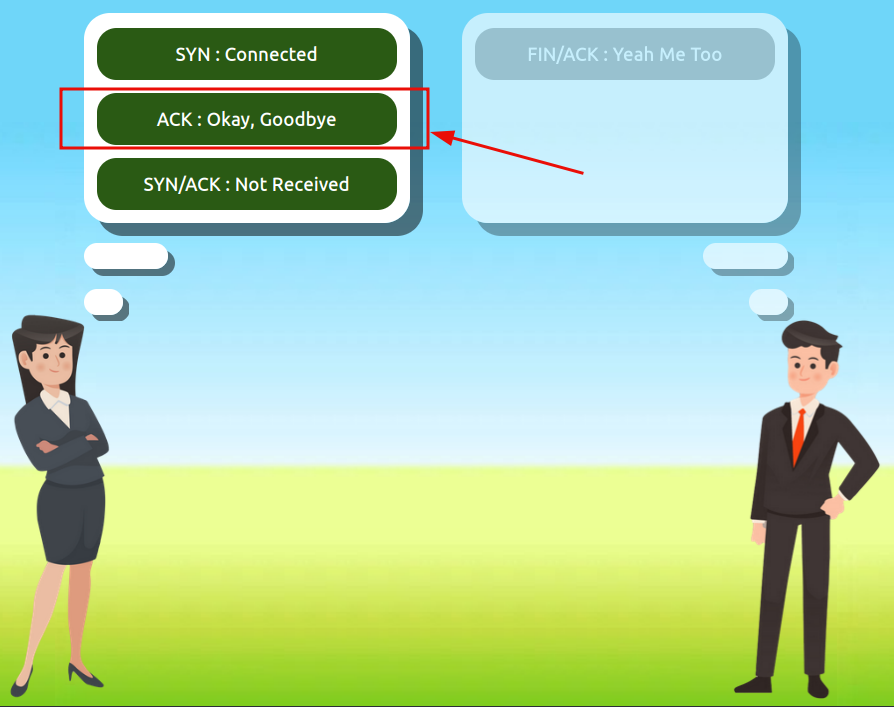
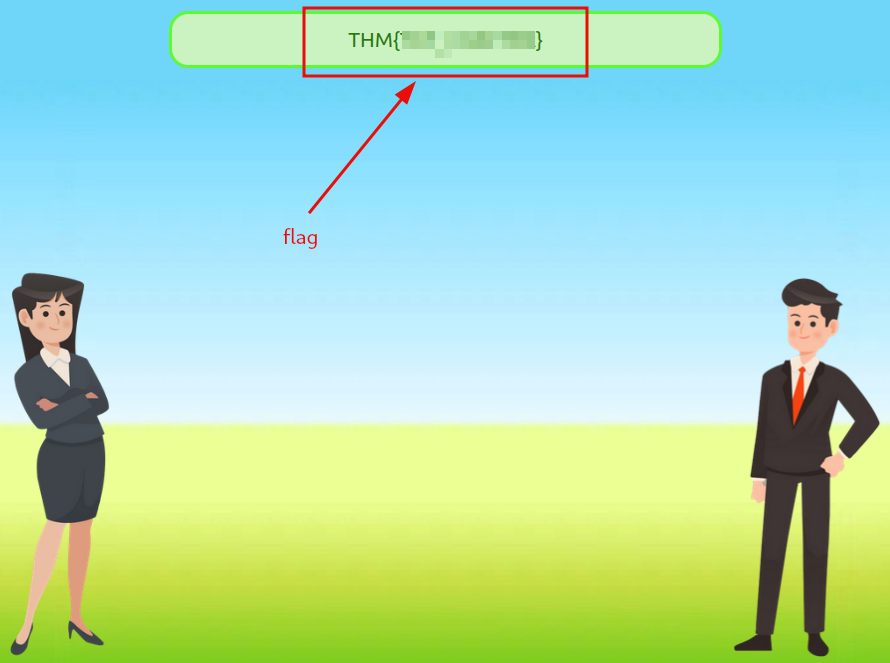
Question 1: What is the value of the flag given at the end of the conversation?
flag
Task 4 - UDP/IP
Discover the properties of the User Datagram Protocol before proceeding to the next task.
Question 1: What does the term “UDP” stand for?
User Datagram Protocol
Question 2: What type of connection is “UDP”?
stateless
Question 3: What protocol would you use to transfer a file?
TCP
Question 4: What protocol would you use to have a video call?
UDP
Task 5 - Ports 101 (Practical)
Use the provided site to connect to the IP address 8.8.8.8 (one of google’s) on port 1234. Check out the flag before moving to the final task.
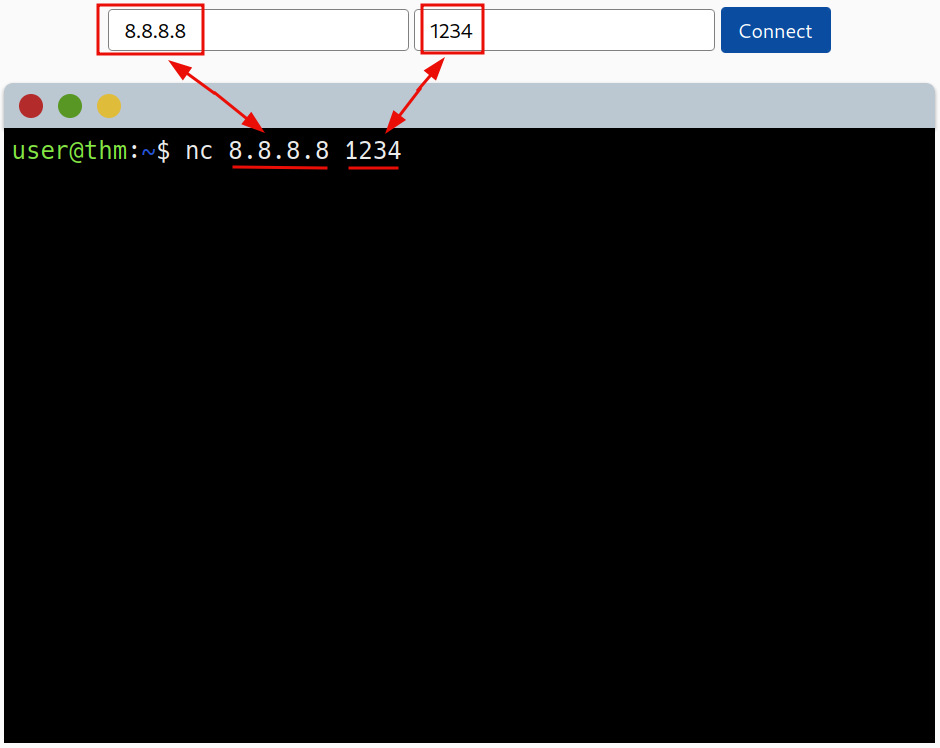
Command used above in the terminal:
nc 8.8.8.8 1234
| command name | description |
|---|---|
| nc | Netcat is a simple Unix utility which reads and writes data across network connections, using TCP or UDP protocol. |
| 8.8.8.8 | [hostname] |
| 1234 | [port] |
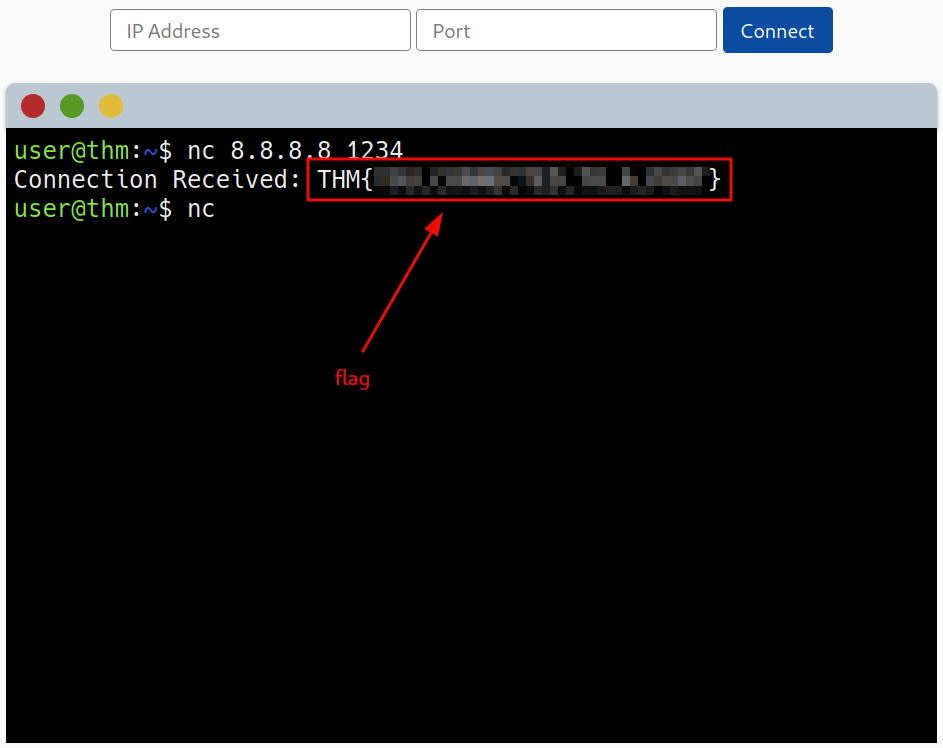
Question 1: What is the flag received from the challenge?
flag
Task 6 - Continue Your Learning: Extending Your Network
With this room complete, only one more room to go to finish the module.
Question 1: Terminate the static site lab deployed in tasks 3 and 5.
No answer needed
Question 2: Join the Extending Your Network room to continue your learning.
No answer needed
thm - shorthand for TryHackMe from now on ↩︎