SYNOPSIS
Outlining the attack path demonstrated in this writeup is much easier through a picture rather than a description, since a picture is worth a thousand words.
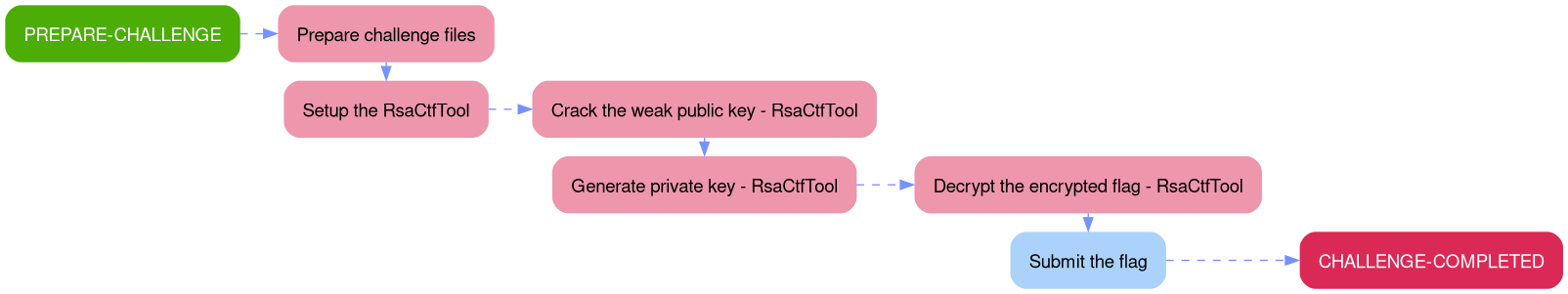
The aim of this walkthrough is to provide help with the Weak RSA challenge on the Hack The Box website. Please note that no flags are directly provided here. Moreover, be aware that this is only one of the many ways to solve the challenges.
It belongs to a series of tutorials that aim to help out with finishing the Beginner-Track challenges.
PREPARING-CHALLENGE-FILES
After a quick look at the challenge description
Can you decrypt the message and get the flag?
we proceed directly by downloading the challenge files.
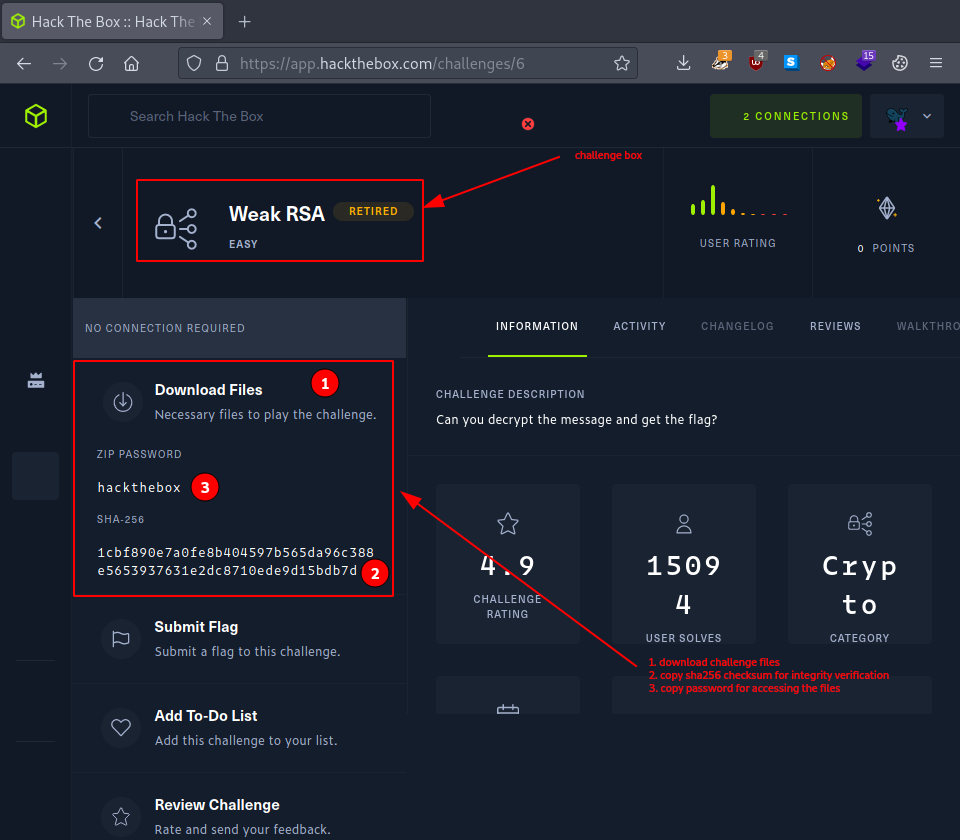
There is only one compressed file called - Weak RSA.zip - and we use the provided sha256 checksum to verify it’s integrity.
# shell command
echo "1cbf890e7a0fe8b404597b565da96c388e5653937631e2dc8710ede9d15bdb7d Weak RSA.zip" | sha256sum -c
# command line interaction
┌─[eu-dedivip-2]─[10.10.14.25]─[htb-bluewalle@htb-cgu0osry2k]─[~/weak-rsa]
└──╼ [★]$ ll
total 4.0K
-rw-r--r-- 1 htb-bluewalle htb-bluewalle 826 May 27 14:34 'Weak RSA.zip'
┌─[eu-dedivip-2]─[10.10.14.25]─[htb-bluewalle@htb-cgu0osry2k]─[~/weak-rsa]
└──╼ [★]$ echo "1cbf890e7a0fe8b404597b565da96c388e5653937631e2dc8710ede9d15bdb7d Weak RSA.zip" | sha256sum -c
Weak RSA.zip: OK
┌─[eu-dedivip-2]─[10.10.14.25]─[htb-bluewalle@htb-cgu0osry2k]─[~/weak-rsa]
└──╼ [★]$
It looks like our file has not been tampered with so we continue with decompressing it.
# shell command
unzip -P hackthebox Weak\ RSA.zip
# command line interaction
┌─[eu-dedivip-2]─[10.10.14.25]─[htb-bluewalle@htb-cgu0osry2k]─[~/weak-rsa]
└──╼ [★]$ unzip -P hackthebox Weak\ RSA.zip
Archive: Weak RSA.zip
inflating: flag.enc
inflating: key.pub
┌─[eu-dedivip-2]─[10.10.14.25]─[htb-bluewalle@htb-cgu0osry2k]─[~/weak-rsa]
└──╼ [★]$
The archive contains two files:
- flag.enc
- key.pub
Once we check them out
# shell command
cat flag.enc
# command line interaction
┌─[eu-dedivip-2]─[10.10.14.25]─[htb-bluewalle@htb-cgu0osry2k]─[~/weak-rsa]
└──╼ [★]$ cat flag.enc
�_�vc[��~�kZ�1�Ĩ�4�I�9V�ֿ�^G���(�+3Lu"�T$���F0�VP�־j@�����|j������{¾�,�����YE�����Xx��,��c�N&Hl2�Ӎ��[o��┌─[eu-dedivip-2]─[10.10.14.25]─[htb-bluewalle@htb-cgu0osry2k]─[~/weak-rsa]
└──╼ [★]$
# shell command
cat key.pub
# command line interaction
┌─[eu-dedivip-2]─[10.10.14.25]─[htb-bluewalle@htb-cgu0osry2k]─[~/weak-rsa]
└──╼ [★]$ cat key.pub
-----BEGIN PUBLIC KEY-----
MIIBHzANBgkqhkiG9w0BAQEFAAOCAQwAMIIBBwKBgQMwO3kPsUnaNAbUlaubn7ip
4pNEXjvUOxjvLwUhtybr6Ng4undLtSQPCPf7ygoUKh1KYeqXMpTmhKjRos3xioTy
23CZuOl3WIsLiRKSVYyqBc9d8rxjNMXuUIOiNO38ealcR4p44zfHI66INPuKmTG3
RQP/6p5hv1PYcWmErEeDewKBgGEXxgRIsTlFGrW2C2JXoSvakMCWD60eAH0W2PpD
qlqqOFD8JA5UFK0roQkOjhLWSVu8c6DLpWJQQlXHPqP702qIg/gx2o0bm4EzrCEJ
4gYo6Ax+U7q6TOWhQpiBHnC0ojE8kUoqMhfALpUaruTJ6zmj8IA1e1M6bMqVF8sr
lb/N
-----END PUBLIC KEY-----
┌─[eu-dedivip-2]─[10.10.14.25]─[htb-bluewalle@htb-cgu0osry2k]─[~/weak-rsa]
└──╼ [★]$
it becomes clear, that only the - key.pub - file contains ASCII text, the encrypted flag file on the other hand appears to have some other character encoding in place.
PREPARING-NECESSARY-TOOLS
So in a nutshell, we have a weak public rsa key - with which our flag was probably encrypted with - our encrypted flag on our hands. Our goal is then to decrypt the flag by leveraging the weak public key and then generate the matching private rsa key. The crux of the issue lies in finding this matching private rsa key. Once the private key is found, decrypting our flag becomes trivial.
Doing a bit of research on the topic rewards us with a very nice rsactftool which we can use to to do just that.
Following the tool’s Ubuntu 18.04 and Kali specific instructions, we fist clone the repo,
# shell command
git clone https://github.com/RsaCtfTool/RsaCtfTool.git
# command line interaction
┌─[eu-dedivip-2]─[10.10.14.25]─[htb-bluewalle@htb-cgu0osry2k]─[~/weak-rsa]
└──╼ [★]$ git clone https://github.com/RsaCtfTool/RsaCtfTool.git
Cloning into 'RsaCtfTool'...
remote: Enumerating objects: 4587, done.
remote: Counting objects: 100% (118/118), done.
remote: Compressing objects: 100% (72/72), done.
remote: Total 4587 (delta 73), reused 76 (delta 46), pack-reused 4469
Receiving objects: 100% (4587/4587), 16.52 MiB | 16.55 MiB/s, done.
Resolving deltas: 100% (3153/3153), done.
┌─[eu-dedivip-2]─[10.10.14.25]─[htb-bluewalle@htb-cgu0osry2k]─[~/weak-rsa]
└──╼ [★]$
then we install the required packages.
# shell command
sudo apt-get install libgmp3-dev libmpc-dev
# command line interaction
┌─[eu-dedivip-2]─[10.10.14.25]─[htb-bluewalle@htb-cgu0osry2k]─[~/weak-rsa]
└──╼ [★]$ sudo apt-get install libgmp3-dev libmpc-dev
Reading package lists... Done
Building dependency tree... Done
Reading state information... Done
The following additional packages will be installed:
libmpfr-dev
Suggested packages:
libmpfr-doc
The following NEW packages will be installed:
libgmp3-dev libmpc-dev libmpfr-dev
0 upgraded, 3 newly installed, 0 to remove and 0 not upgraded.
Need to get 639 kB of archives.
After this operation, 1,909 kB of additional disk space will be used.
Do you want to continue? [Y/n] Y
Get:1 https://deb.parrot.sh/parrot parrot/main amd64 libgmp3-dev amd64 2:6.2.1+dfsg-1+deb11u1 [330 kB]
Get:2 https://deb.parrot.sh/parrot parrot/main amd64 libmpfr-dev amd64 4.1.0-3 [252 kB]
Get:3 https://deb.parrot.sh/parrot parrot/main amd64 libmpc-dev amd64 1.2.0-1 [56.7 kB]
Fetched 639 kB in 0s (2,423 kB/s)
Selecting previously unselected package libgmp3-dev:amd64.
(Reading database ... 506084 files and directories currently installed.)
Preparing to unpack .../libgmp3-dev_2%3a6.2.1+dfsg-1+deb11u1_amd64.deb ...
Unpacking libgmp3-dev:amd64 (2:6.2.1+dfsg-1+deb11u1) ...
Selecting previously unselected package libmpfr-dev:amd64.
Preparing to unpack .../libmpfr-dev_4.1.0-3_amd64.deb ...
Unpacking libmpfr-dev:amd64 (4.1.0-3) ...
Selecting previously unselected package libmpc-dev:amd64.
Preparing to unpack .../libmpc-dev_1.2.0-1_amd64.deb ...
Unpacking libmpc-dev:amd64 (1.2.0-1) ...
Setting up libmpfr-dev:amd64 (4.1.0-3) ...
Setting up libmpc-dev:amd64 (1.2.0-1) ...
Setting up libgmp3-dev:amd64 (2:6.2.1+dfsg-1+deb11u1) ...
Scanning application launchers
Removing duplicate launchers or broken launchers
Launchers are updated
┌─[eu-dedivip-2]─[10.10.14.25]─[htb-bluewalle@htb-cgu0osry2k]─[~/weak-rsa]
└──╼ [★]$
After that, we head over to the cloned repo and install the necessary python modules too.
# shell command
cd RsaCtfTool/ ; ll
# command line interaction
┌─[eu-dedivip-2]─[10.10.14.25]─[htb-bluewalle@htb-cgu0osry2k]─[~/weak-rsa]
└──╼ [★]$ cd RsaCtfTool/
┌─[eu-dedivip-2]─[10.10.14.25]─[htb-bluewalle@htb-cgu0osry2k]─[~/weak-rsa/RsaCtfTool]
└──╼ [★]$ ll
total 76K
drwxr-xr-x 1 htb-bluewalle htb-bluewalle 98 May 27 15:25 attacks
-rw-r--r-- 1 htb-bluewalle htb-bluewalle 3.3K May 27 15:25 CHANGELOG.md
-rw-r--r-- 1 htb-bluewalle htb-bluewalle 891 May 27 15:25 CONTRIBUTING.md
-rw-r--r-- 1 htb-bluewalle htb-bluewalle 394 May 27 15:25 Dockerfile
-rw-r--r-- 1 htb-bluewalle htb-bluewalle 3.2K May 27 15:25 Dockerfile_full
drwxr-xr-x 1 htb-bluewalle htb-bluewalle 1.7K May 27 15:25 examples
drwxr-xr-x 1 htb-bluewalle htb-bluewalle 414 May 27 15:25 lib
-rw-r--r-- 1 htb-bluewalle htb-bluewalle 250 May 27 15:25 LICENSE.md
-rw-r--r-- 1 htb-bluewalle htb-bluewalle 33 May 27 15:25 optional-requirements.txt
-rw-r--r-- 1 htb-bluewalle htb-bluewalle 11K May 27 15:25 README.md
-rw-r--r-- 1 htb-bluewalle htb-bluewalle 145 May 27 15:25 requirements.txt
-rwxr-xr-x 1 htb-bluewalle htb-bluewalle 17K May 27 15:25 RsaCtfTool.py
drwxr-xr-x 1 htb-bluewalle htb-bluewalle 356 May 27 15:25 sage
-rw-r--r-- 1 htb-bluewalle htb-bluewalle 938 May 27 15:25 setup.py
-rwxr-xr-x 1 htb-bluewalle htb-bluewalle 11K May 27 15:25 test.sh
┌─[eu-dedivip-2]─[10.10.14.25]─[htb-bluewalle@htb-cgu0osry2k]─[~/weak-rsa/RsaCtfTool]
└──╼ [★]$
# shell command
pip3 install -r "requirements.txt"
# command line interaction
┌─[eu-dedivip-2]─[10.10.14.25]─[htb-bluewalle@htb-cgu0osry2k]─[~/weak-rsa/RsaCtfTool]
└──╼ [★]$ pip3 install -r "requirements.txt"
Requirement already satisfied: six in /usr/lib/python3/dist-packages (from -r requirements.txt (line 1)) (1.16.0)
Collecting cryptography==39.0.1
Downloading cryptography-39.0.1-cp36-abi3-manylinux_2_28_x86_64.whl (4.2 MB)
|████████████████████████████████| 4.2 MB 13.2 MB/s
Requirement already satisfied: urllib3==1.26.5 in /usr/lib/python3/dist-packages (from -r requirements.txt (line 3)) (1.26.5)
Collecting requests==2.25.1
Downloading requests-2.25.1-py2.py3-none-any.whl (61 kB)
|████████████████████████████████| 61 kB 6.9 MB/s
...
...
Installing collected packages: requests, z3-solver, pycryptodome, psutil, gmpy2, factordb-pycli, cryptography, bitarray
ERROR: pip's dependency resolver does not currently take into account all the packages that are installed. This behaviour is the source of the following dependency conflicts.
crackmapexec 5.4.1 requires paramiko<3.0.0,>=2.7.2, but you have paramiko 3.1.0 which is incompatible.
crackmapexec 5.4.1 requires requests>=2.27.1, but you have requests 2.25.1 which is incompatible.
censys 2.1.9 requires backoff<3.0.0,>=2.0.1, but you have backoff 1.10.0 which is incompatible.
censys 2.1.9 requires requests>=2.26.0, but you have requests 2.25.1 which is incompatible.
censys 2.1.9 requires rich>=10.16.2, but you have rich 10.12.0 which is incompatible.
Successfully installed bitarray-2.7.3 cryptography-39.0.1 factordb-pycli-1.1.1 gmpy2-2.1.2 psutil-5.9.4 pycryptodome-3.10.4 requests-2.25.1 z3-solver-4.12.2.0
┌─[eu-dedivip-2]─[10.10.14.25]─[htb-bluewalle@htb-cgu0osry2k]─[~/weak-rsa/RsaCtfTool]
└──╼ [★]$
DEBUGGING
Since there were some error messages and warnings during the installation of the necessary python modules, we decide to install the optional requirements too.
# shell command
pip3 install -r "optional-requirements.txt"
# command line interaction
┌─[eu-dedivip-2]─[10.10.14.25]─[htb-bluewalle@htb-cgu0osry2k]─[~/weak-rsa/RsaCtfTool]
└──╼ [★]$ pip3 install -r "optional-requirements.txt"
Collecting wolframalpha
Downloading wolframalpha-5.0.0-py3-none-any.whl (7.5 kB)
Collecting SageMath
Downloading sagemath-1.3.0.tar.gz (9.4 kB)
Collecting gmpy==1.17
Downloading gmpy-1.17.zip (147 kB)
|████████████████████████████████| 147 kB 31.6 MB/s
Collecting cython>=0.26
Downloading Cython-0.29.35-cp39-cp39-manylinux_2_17_x86_64.manylinux2014_x86_64.manylinux_2_24_x86_64.whl (2.0 MB)
|████████████████████████████████| 2.0 MB 59.4 MB/s
Collecting jaraco.context
Downloading jaraco.context-4.3.0-py3-none-any.whl (5.3 kB)
Requirement already satisfied: xmltodict in /usr/lib/python3/dist-packages (from wolframalpha->-r optional-requirements.txt (line 1)) (0.12.0)
Requirement already satisfied: more-itertools in /usr/lib/python3/dist-packages (from wolframalpha->-r optional-requirements.txt (line 1)) (4.2.0)
Building wheels for collected packages: gmpy, SageMath
Building wheel for gmpy (setup.py) ... done
Created wheel for gmpy: filename=gmpy-1.17-cp39-cp39-linux_x86_64.whl size=243383 sha256=50e19384f637b09189bde707e5c932207510717306eeb23fe388cd7057ba2426
Stored in directory: /home/htb-bluewalle/.cache/pip/wheels/51/cd/a9/d2cbef6019ffcb5d63560bf572a00956ce0ebf043519eaef5c
Building wheel for SageMath (setup.py) ... done
Created wheel for SageMath: filename=sagemath-1.3.0-py3-none-any.whl size=9346 sha256=a1303dcb41118248b616236b879759160e25d52da1773ab6a435d423b267405c
Stored in directory: /home/htb-bluewalle/.cache/pip/wheels/25/00/30/c3c9c8116235d0f05f58254f3713f97b6c974cbde229032be6
Successfully built gmpy SageMath
Installing collected packages: jaraco.context, cython, wolframalpha, SageMath, gmpy
Successfully installed SageMath-1.3.0 cython-0.29.35 gmpy-1.17 jaraco.context-4.3.0 wolframalpha-5.0.0
┌─[eu-dedivip-2]─[10.10.14.25]─[htb-bluewalle@htb-cgu0osry2k]─[~/weak-rsa/RsaCtfTool]
└──╼ [★]$
Trying to uncipher the flag on the first run throws an error message indicating that the -private argument is not set, the private key will not be displayed, even if recovered-.
There is a quick fix for this mentioned under - Issues - by simply uncommenting lines 425 and 426 in the - RsaCtfTool.py - file.
# RsaCtfTool.py
...
# if we have uncipher but no uncipherfile
if args.uncipher is not None:
uncipher_array = []
for uncipher in args.uncipher.split(","):
uncipher = get_numeric_value(uncipher)
uncipher = get_base64_value(uncipher)
uncipher_array.append(n2s(uncipher))
args.uncipher = uncipher_array
# if we have uncipherfile
if args.uncipherfile is not None:
if uncipher_file(args, logger):
sys.exit(0)
#else:
# sys.exit(-1)
# If we have n and one of p and q, calculated the other
if args.n and (args.p or args.q):
args.p, args.q = generate_pq_from_n_and_p_or_q(args.n, args.p, args.q)
...
ATTACKING-WEAK-RSA-PUBLIC-KEY
Then we try again.
# shell command
./RsaCtfTool.py --publickey ../key.pub --uncipherfile ../flag.enc --private
# command line interaction
┌─[eu-dedivip-2]─[10.10.14.25]─[htb-bluewalle@htb-cgu0osry2k]─[~/weak-rsa/RsaCtfTool]
└──╼ [★]$ ./RsaCtfTool.py --publickey ../key.pub --uncipherfile ../flag.enc --private
[*] Testing key ../key.pub.
attack initialized...
attack initialized...
[*] Performing factordb attack on ../key.pub.
[!] internal error :-(
[+] Time elapsed: 0.0410 sec.
[*] Performing fibonacci_gcd attack on ../key.pub.
100%|██████████████████████████████████████████████████| 9999/9999 [00:00<00:00, 76579.79it/s]
[+] Time elapsed: 0.1452 sec.
[*] Performing lucas_gcd attack on ../key.pub.
100%|██████████████████████████████████████████████████| 9999/9999 [00:00<00:00, 78579.10it/s]
[+] Time elapsed: 0.1278 sec.
[*] Performing mersenne_primes attack on ../key.pub.
27%|██████████████▌ | 14/51 [00:00<00:00, 279620.27it/s]
[+] Time elapsed: 0.0007 sec.
[*] Performing nonRSA attack on ../key.pub.
[+] Time elapsed: 0.0017 sec.
[*] Performing pastctfprimes attack on ../key.pub.
100%|███████████████████████████████████████████████████| 113/113 [00:00<00:00, 923891.52it/s]
[+] Time elapsed: 0.0006 sec.
[*] Performing smallq attack on ../key.pub.
[+] Time elapsed: 0.4057 sec.
[*] Performing system_primes_gcd attack on ../key.pub.
100%|█████████████████████████████████████████████████| 7007/7007 [00:00<00:00, 604784.20it/s]
[+] Time elapsed: 0.0407 sec.
[*] Performing SQUFOF attack on ../key.pub.
[!] Timeout.
[+] Time elapsed: 60.0004 sec.
[*] Performing boneh_durfee attack on ../key.pub.
Can't load boneh_durfee because sage binary is not installed
[*] Performing carmichael attack on ../key.pub.
[!] Timeout.
[+] Time elapsed: 60.0005 sec.
[*] Performing classical_shor attack on ../key.pub.
[!] Timeout.
[+] Time elapsed: 60.0004 sec.
[*] Performing comfact_cn attack on ../key.pub.
[+] Time elapsed: 0.0003 sec.
[*] Performing compositorial_pm1_gcd attack on ../key.pub.
100%|██████████████████████████████████████████████████| 9999/9999 [00:00<00:00, 12892.83it/s]
[+] Time elapsed: 0.7763 sec.
[*] Performing cube_root attack on ../key.pub.
[+] Time elapsed: 0.0001 sec.
[*] Performing ecm2 attack on ../key.pub.
Can't load ecm2 because sage binary is not installed
[*] Performing factor_2PN attack on ../key.pub.
[+] Time elapsed: 0.0001 sec.
[*] Performing factorial_pm1_gcd attack on ../key.pub.
100%|█████████████████████████████████████████████████| 29998/29998 [00:09<00:00, 3211.78it/s]
[+] Time elapsed: 9.3420 sec.
[*] Performing fermat attack on ../key.pub.
[!] Timeout.
[+] Time elapsed: 60.0005 sec.
[*] Performing fermat_numbers_gcd attack on ../key.pub.
100%|█████████████████████████████████████████████████████████| 28/28 [00:01<00:00, 25.24it/s]
[+] Time elapsed: 1.1110 sec.
[*] Performing hart attack on ../key.pub.
[!] Timeout.
[+] Time elapsed: 60.0004 sec.
[*] Performing highandlowbitsequal attack on ../key.pub.
[+] Time elapsed: 0.0002 sec.
[*] Performing kraitchik attack on ../key.pub.
[!] Timeout.
[+] Time elapsed: 60.0004 sec.
[*] Performing lattice attack on ../key.pub.
[!] simple lattice attack is for partial keys only...
[+] Time elapsed: 0.0002 sec.
[*] Performing lehman attack on ../key.pub.
[!] Timeout.
[+] Time elapsed: 60.0003 sec.
[*] Performing lehmer attack on ../key.pub.
[!] Timeout.
[+] Time elapsed: 60.0005 sec.
[*] Performing mersenne_pm1_gcd attack on ../key.pub.
100%|██████████████████████████████████████████████████| 1024/1024 [00:00<00:00, 80179.35it/s]
[+] Time elapsed: 0.0136 sec.
[*] Performing noveltyprimes attack on ../key.pub.
100%|█████████████████████████████████████████████████████| 21/21 [00:00<00:00, 222425.21it/s]
[+] Time elapsed: 0.0007 sec.
[*] Performing partial_d attack on ../key.pub.
[!] partial_d attack is only for partial private keys not pubkeys...
[!] partial_d internal error...
[+] Time elapsed: 0.0003 sec.
[*] Performing partial_q attack on ../key.pub.
[!] partial_q attack is only for partial private keys not pubkeys...
[+] Time elapsed: 0.0001 sec.
[*] Performing pisano_period attack on ../key.pub.
[+] Time elapsed: 0.0001 sec.
[*] Performing pollard_p_1 attack on ../key.pub.
8%|████▎ | 76/997 [00:59<13:07, 1.17it/s][!] Timeout.
8%|████▎ | 76/997 [00:59<12:07, 1.27it/s]
[+] Time elapsed: 60.0008 sec.
[*] Performing primorial_pm1_gcd attack on ../key.pub.
100%|████████████████████████████████████████████████| 10000/10000 [00:00<00:00, 10667.54it/s]
[+] Time elapsed: 0.9382 sec.
[*] Performing qicheng attack on ../key.pub.
Can't load qicheng because sage binary is not installed
[*] Performing qs attack on ../key.pub.
Can't load qs because sage binary is not installed
[*] Performing siqs attack on ../key.pub.
Can't load siqs because yafu binary is not installed
[*] Performing small_crt_exp attack on ../key.pub.
Can't load small_crt_exp because sage binary is not installed
[*] Performing wiener attack on ../key.pub.
26%|█████████████▎ | 158/607 [00:00<00:00, 485494.53it/s]
[*] Attack success with wiener method !
[+] Total time elapsed min,max,avg: 0.0001/60.0008/17.8371 sec.
Results for ../key.pub:
Private key :
-----BEGIN RSA PRIVATE KEY-----
MIICOQIBAAKBgQMwO3kPsUnaNAbUlaubn7ip4pNEXjvUOxjvLwUhtybr6Ng4undL
tSQPCPf7ygoUKh1KYeqXMpTmhKjRos3xioTy23CZuOl3WIsLiRKSVYyqBc9d8rxj
NMXuUIOiNO38ealcR4p44zfHI66INPuKmTG3RQP/6p5hv1PYcWmErEeDewKBgGEX
xgRIsTlFGrW2C2JXoSvakMCWD60eAH0W2PpDqlqqOFD8JA5UFK0roQkOjhLWSVu8
c6DLpWJQQlXHPqP702qIg/gx2o0bm4EzrCEJ4gYo6Ax+U7q6TOWhQpiBHnC0ojE8
kUoqMhfALpUaruTJ6zmj8IA1e1M6bMqVF8srlb/NAiBhwngxi+Cbie3YBogNzGJV
h10vAgw+i7cQqiiwEiPFNQJBAYXzr5r2KkHVjGcZNCLRAoXrzJjVhb7knZE5oEYo
nEI+h2gQSt1bavv3YVxhcisTVuNrlgQo58eGb4c9dtY2blMCQQIX2W9IbtJ26KzZ
C/5HPsVqgxWtuP5hN8OLf3ohhojr1NigJwc6o68dtKScaEQ5A33vmNpuWqKucecT
0HEVxuE5AiBhwngxi+Cbie3YBogNzGJVh10vAgw+i7cQqiiwEiPFNQIgYcJ4MYvg
m4nt2AaIDcxiVYddLwIMPou3EKoosBIjxTUCQQCnqbJMPEQHpg5lI6MQi8ixFRqo
+KwoBrwYfZlGEwZxdK2Ms0jgeta5jFFS11Fwk5+GyimnRzVcEbADJno/8BKe
-----END RSA PRIVATE KEY-----
Unciphered data :
HEX : 0x000221cfb29883b06f409a679a58a4e97b446e28b244bbcd0687d178a8ab8722bf86da06a62e042c892d2921b336571e9ff7ac9d89ba90512bac4cfb8d7e4a3901bbccf5dfac01b27bddd35f1ca55344a75943df9a18eadb344cf7cf55fa0baa7005bfe32f41004854427b73316d706c335f5769336e3372735f34747434636b7d
INT (big endian) : 1497194306832430076266314478305730170974165912795150306640063107539292495904192020114449824357438113183764256783752233913408135242464239912689425668318419718061442061010640167802145162377597484106658670422900749326253337728846324798012274989739031662527650589811318528908253458824763561374522387177140349821
INT (little endian) : 22546574266225300968123857704721191858671593287972919965619572675918636257464402082642870677657579044805501825719744981953609630743396909394906721219496019830622451770590549653716476856077849644487076110495020954617170743371827481017047908786316114794508942268154434710618690751442928771926238749045133355844096
STR : b'\x00\x02!\xcf\xb2\x98\x83\xb0o@\x9ag\x9aX\xa4\xe9{Dn(\xb2D\xbb\xcd\x06\x87\xd1x\xa8\xab\x87"\xbf\x86\xda\x06\xa6.\x04,\x89-)!\xb36W\x1e\x9f\xf7\xac\x9d\x89\xba\x90Q+\xacL\xfb\x8d~J9\x01\xbb\xcc\xf5\xdf\xac\x01\xb2{\xdd\xd3_\x1c\xa5SD\xa7YC\xdf\x9a\x18\xea\xdb4L\xf7\xcfU\xfa\x0b\xaap\x05\xbf\xe3/A\x00<flag>'
PKCS#1.5 padding decoded!
HEX : <flag-hex-encoded>
INT (big endian) :
<flag-big-endian-encoded>
INT (little endian) :
<flag-little-endian-encoded>
utf-8 : <flag>
STR : b'\x00<flag>'
┌─[eu-dedivip-2]─[10.10.14.25]─[htb-bluewalle@htb-cgu0osry2k]─[~/weak-rsa/RsaCtfTool]
└──╼ [★]$
This time it works, and using the Wiener attack a matching private rsa key is found. Decrypting our flag goes pretty fast after that.
CLEAN-UP
Given that this was a challenge box without any instantiated targets, there is simply not much to clean up here. Once the flag is submitted, we move on to the next machine.